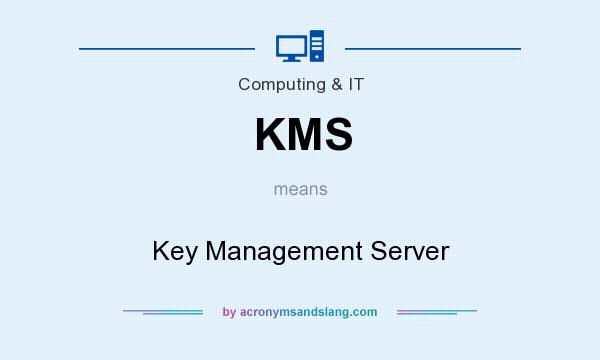
Key Management Server
Key storage As a general principle, the person or company who stores your encrypted content should not also store the Policy management While the primary role of encryption keys is to protect data, they can also.

Key management server. VMware Compatibility Guide This document lists Key Management Servers, also referred to as KMS, developed and released by Security and Cloud vendors for encryption in virtualized environments. The Key Management component has the following features IdentityServer key generation, storage, and rotation;. Key management software, which can run either on a dedicated server or within a virtual/cloud server;.
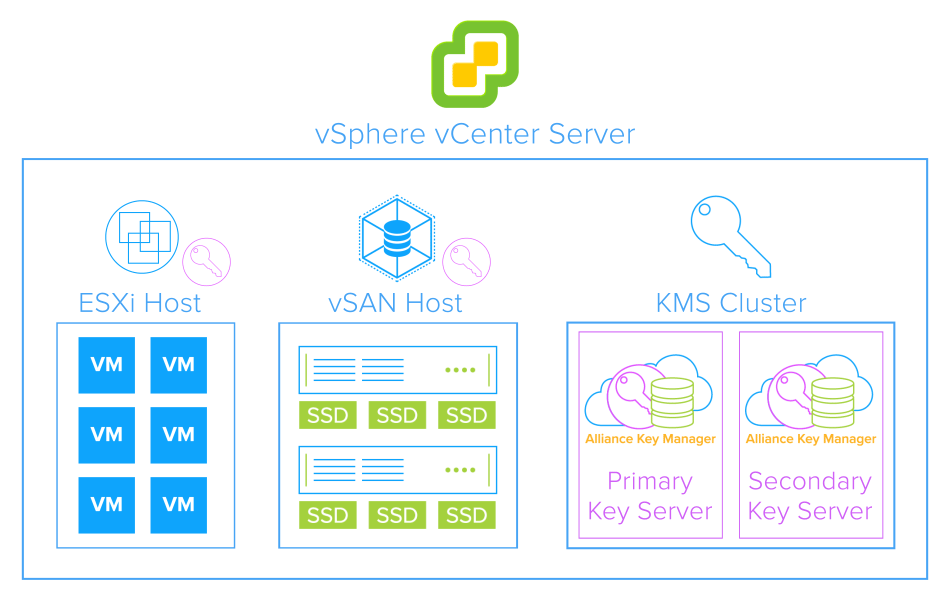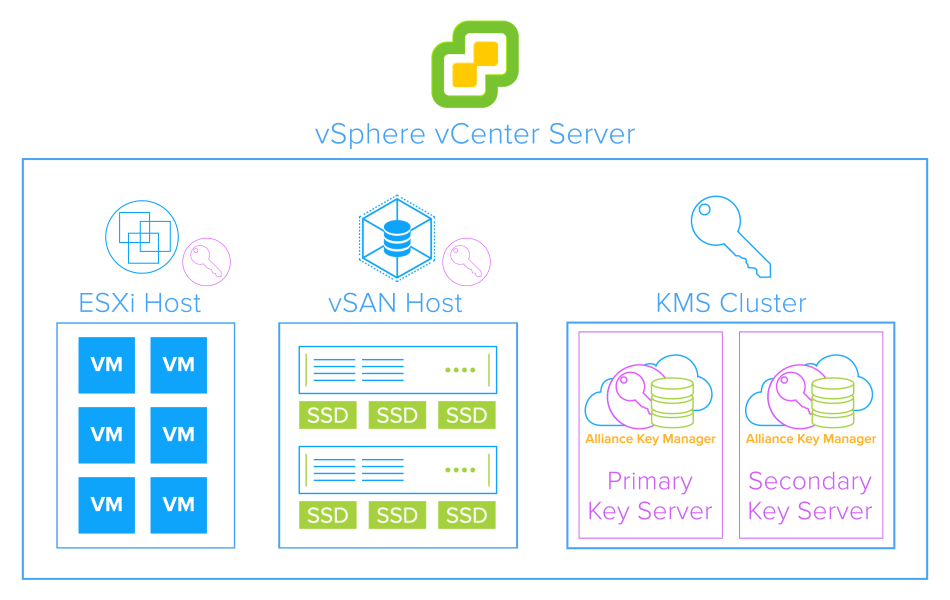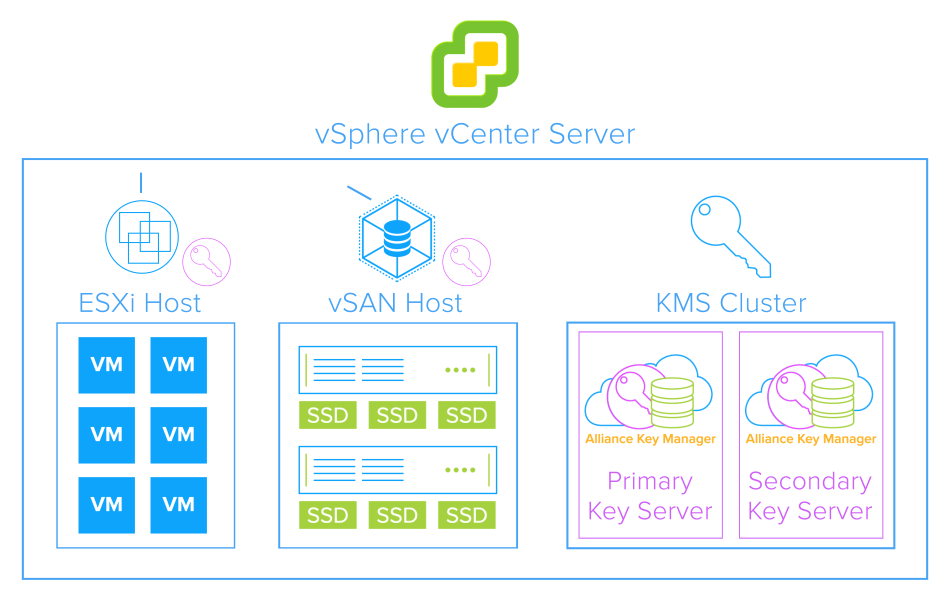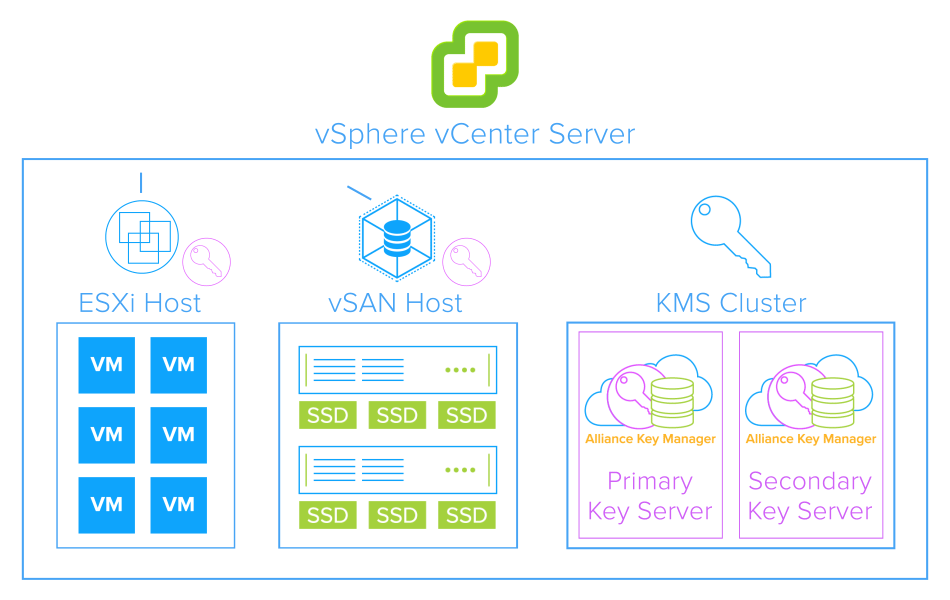
A Key Management Server (KMS) cluster provides the keys that you can use to encrypt the Virtual SAN datastore Before you can encrypt the Virtual SAN datastore, you must set up a KMS cluster to support encryption. Problem The Key Management Server (KMS) rejects periodic activation requests, and the Windows® operating system shows as unlicensed Cause The two leading causes of this issue are Windows cannot locate the KMS The server’s clock differs from the KMS clock by more than four hours Use the steps in the following sections to resolve this issue. Key Management Software as a Service (SaaS).
Enterprise key management is a system that empowers clients with professional key management solutions, which offer encryption keys across a variety of databases and operating systems According to 360 Quadrant analysis, the following have been identified as the top 10 vendors in the Best Enterprise key management Software Top 10 Enterprise key management Software. Key management involves separating keys from data for increased flexibility and security You can have multiple keys for the same data, the same key for multiple files, key backup and recovery, and many more choices Best practice is to use a dedicated external key management system There are four types2. Key management servers (KMS) are used to administer the full lifecycle of cryptographic keys and protect them from loss or misuse KMS solutions, and other Key Management Solutions, ultimately control the generation, usage, storage, archival, and deletion of encryption keys.
Sample Code IdentityServer key generation, storage, and rotation IdentityServer creates tokens, and those tokens must be signed by a key IdentityServer can be configured with an explicit signing. These key stores are part of a global key management infrastructure that is managed by our professionals on a 24x7x365 basis to ensure availability and security The SGTDEMySQL key management features will allow you to generate, distribute, rotate and revoke the data encryption keys with ease. When the Key Management Service (KMS) is initially enabled on a server, it should automatically register an SRV record in DNS that will allow KMS clients on the network to locate it Should this registration fail for some reason, the appropriate DNS record may be created manually by following the procedure below.
The Eperi Key Management plugin is a key management and encryption plugin that uses the eperi Gateway for Databases The eperi Gateway for Databases stores encryption keys on the key server outside of the database server itself, which provides an extra level of security. To activate, use the slmgrvbs command Open an elevated command prompt and run one of the following commands To install the KMS key, type slmgrvbs /ipk To activate online, type slmgrvbs /ato To activate by telephone, follow these steps Run slmgrvbs /dti and confirm the installation ID. The Key Management Server (KMS) service is offered to CalNetAD campus customers to activate current versions of Windows and Office The KMS service will activate the following operating systems Windows 7 Windows 81;.
Key Management in Secret Server Cloud allows you to add an additional layer of encryption using a thirdparty provider to protect these encryption keys for added protection and control To do this you must first set up your own encryption key with a third party that you fully control, and then provide Secret Server limited access to it. Keyzapp is key management software, and includes features such as audit trail, checkin / checkout, key holder management, and overdue tracking Software pricing starts at $3753/month Some competitor software products to Keyza. The Key Management component has the following features IdentityServer key generation, storage, and rotation;.
An HSM or other hardware key management appliance, which provides the highest level of physical security;. ASPNET Data Protection key storage;. Configure the Key Management Server Use this procedure to configure CloudLink Center as the Key Management Server in vSphere Web Client Procedure Use the vSphere Web Client to log in to the vCenter Server Select the vCenter Server in the.
Alliance Key Manager is a FIPS 1402 compliant enterprise key manager that helps organizations meet compliance requirements and protect private information Centralized Encryption Key Management Server (KMS) Townsend Security. I think it is actually the stepbystep method on cleanly uninstalling KMS (key management service) 1 Uninstall the KMS host key first by running the following command slmgr –upk 2 Then install the default kms key by running the following command slmgr /ipk. Installing the Key Management Server by Lauren Malhoit in SMB Technologist, in Microsoft on April 22, 12, 950 PM PST Lauren Malhoit helps those implementing KMS to be aware of some caveats.
The Microsoft Key Management Server (KMS) is part of the Microsoft Volume Activation solution managing Windows OS activation keys and performs activation for supported clients automatically Starting with Windows Server 08 & Windows Vista, Microsoft switched to an online activation system where every Windows OS requires activation. The Key Management Interoperability Protocol (KMIP) is an extensible communication protocol that defines message formats for the manipulation of cryptographic keys on a key management server This facilitates data encryption by simplifying encryption key management Keys may be created on a server and then retrieved, possibly wrapped by other keys. The KeyManagerOptions class provides properties to control the key management and rotation feature These properties are KeyIdSize (int) Size, in bits, of key identifiers Defaults to 128 KeySize (int) Size, in bits, of RSA keys Defaults to 48 KeyType (enum) Key type to create RSA will use RSA keys.
Key management server free download Nextcloud Server Nextcloud server is a free and open source server software that allows you to store all of your data key management server free download SourceForge. The Key Management Server must support the Key Management Interoperability Protocol (KMIP) 11 standard See the vSphere Compatibility Matrices for details You can find information about VMware certified KMS vendors in the VMware Compatibility Guide under Platform and Compute If you select Compatibility Guides, you can open the Key Management Server (KMS) compatibility documentation. Refer to Dev Options to learn more about Vault dev server options The Vault dev server is now ready for use » Scenario Introduction In this tutorial, you will use a Vault dev mode server to configure the Key Management secrets engine for use with Microsoft Azure, and then perform some lifecycle operations with the secrets engine, like writing, reading, updating, rotating keys.
Microsoft has developed the Key Management Service (KMS) as a means to simplify activation of volumelicensed products Using KMS, a server is deployed internally and keeps track of the activation status of volumelicensed products within the environment Machines on the network use this internal server for activation instead of contacting Microsoft. ASPNET Data Protection key storage;. EKM Provider software performs encryption and key management tasks as an extension to the SQL Server database The EKM Provider architecture opened the door for third party key management vendors to extend encryption to include proper encryption key management From a high level point of view the EKM architecture looks like this.
Key management refers to management of cryptographic keys in a cryptosystemThis includes dealing with the generation, exchange, storage, use, cryptoshredding (destruction) and replacement of keys It includes cryptographic protocol design, key servers, user procedures, and other relevant protocols Key management concerns keys at the user level, either between users or systems. Select the vCenter Server in the Object Navigator Select Configure > Key Management Servers in vSphere Web Client Click Add KMS > Create a new cluster and provide the following values Cluster name —A name for the cluster Server alias —A name for the CloudLink Center instance. Windows Server 08(R2) Windows Server 12(R2) Windows Server 16;.
Problem The Key Management Server (KMS) rejects periodic activation requests, and the Windows® operating system shows as unlicensed Cause The two leading causes of this issue are Windows cannot locate the KMS The server’s clock differs from the KMS clock by more than four hours Use the steps in the following sections to resolve this issue. Key management server free download Nextcloud Server Nextcloud server is a free and open source server software that allows you to store all of your data key management server free download SourceForge. Available via StorMagic Cloud Services, Key ManagementasaService (KMaaS) allows an organization to deploy a cloudbased key management service, instead of running one or more key managers on physical hardware It ensures an organization can keep all keys secure and accessible within the cloud, regardless of encryption workload or location.
With the release of version 193, Tableau Server includes an updated key management system (KMS) Tableau Server local KMS The Tableau Server local KMS uses the secret storage capability described in Manage Server Secrets to encrypt and store the master extract key In this scenario, the Java keystore serves as the root of the key hierarchy. The following information outlines initial planning considerations that you need to review for Key Management Services (KMS) activation involving Windows Server 16 For information about KMS activation involving operating systems older than those listed here, see Step 1 Review and Select Activation Methods. Leveraging FIPS 1402compliant virtual or hardware appliances, Thales key management tools and solutions deliver high security to sensitive environments and centralize key management for your homegrown encryption, as well as your thirdparty applications This gives you greater command over your keys while increasing your data security.
Key Management Service Host File Make sure you have downloaded the Key Management Service Host for the specific Windows product Once downloaded, run the executable and enter your KMS product key for the specific product when prompted If this part isn’t completed, the KMS product key you entered manually into VAMT won’t work Firewall Rules. There is one key on the server that all the users would use to access the server – AllenKll Apr 22 '14 at 1323 Ok, I clearly misunderstood your question, so the authorized_keys on your servers will be static and your not looking for a way to change them, but your looking for a method of distributing the corresponding private keys to ~60 users?. Install the KMS host product key First, install the KMS key on the KMS Server by running the following from an elevated command prompt (right click Command Prompt and choose “Run as administrator”) slmgrvbs /ipk After that completes successfully, run the following command to activate the key online with Microsoft slmgrvbs /ato.
Promaster Key Manager is key management software, and includes features such as access Controls/Permissions, Alerts/Notifications, key holder management, and overdue tracking Software pricing starts at $/onetime/user. Sample Code IdentityServer key generation, storage, and rotation IdentityServer creates tokens, and those tokens must be signed by a key IdentityServer can be configured with an explicit signing. Manage Secrets and Protect Sensitive Data Secure, store and tightly control access to tokens, passwords, certificates, encryption keys for protecting secrets and other sensitive data using a UI, CLI, or HTTP API Download Get Started with Vault.
Vault secures, stores, and tightly controls access to tokens, passwords, certificates, API keys, and other secrets in modern computing Vault handles leasing, key revocation, key rolling, auditing, and provides secrets as a service through a unified API. KMS (Key Management Service) is an activation service that allows organizations to manage the activation of their Windows systems and Office by eliminating the need for individual computers to connect to Microsoft for product activation This service makes activation easier to manage and control for midsize and largesize companies. Key management refers to management of cryptographic keys in a cryptosystemThis includes dealing with the generation, exchange, storage, use, cryptoshredding (destruction) and replacement of keys It includes cryptographic protocol design, key servers, user procedures, and other relevant protocols Key management concerns keys at the user level, either between users or systems.
Finally took the time to do this for you guys Sorry for the wait Before it will start doing what you want it to, you need to meet certain thresholds, with. VMware Compatibility Guide This document lists Key Management Servers, also referred to as KMS, developed and released by Security and Cloud vendors for encryption in virtualized environments. Take a look at KeyManager, which is the key management component of the OpenStack suite The application can be used as a standalone key management solution outside of OpenStack Being a component of OpenStack, KeyManager is being actively developed with new features planned on six month cycles.
When maintaining keys used for cryptographic operations (such as when running a token server that maintains keys used to sign tokens), a good security practice is to periodically rotate your keys This is the process of retiring one key and onboarding another. Find and compare top Key Management software on Capterra, with our free and interactive tool Quickly browse through hundreds of Key Management tools and systems and narrow down your top choices Filter by popular features, pricing options, number of users, and read reviews from real users and find a tool that fits your needs. What are the critical components performed by encryption key management servers?.
Microsoft Key Management Service (KMS) for Windows Server 03 SP1 and later is part of Microsoft Windows Volume Activation It allows enterprise users to host KMS on Windows Server 03 to enable activation of Windows Vista and Windows Server 08 using a KMS key. This document lists Key Management Servers, also referred to as KMS, developed and released by Security and Cloud vendors for encryption in virtualized environments The KMS listed below passed VMware's KMS Certification tests, which allows these certified KMS to provide a measure of reliability and stability of the end solution in customer. A Key Management Server (KMS) is a cryptographic appliance that allows for the standardscompliant management of the encryption key lifecycle creating, managing, distributing, and retiring keys Futurex key management devices are a hardened, enterpriseclass key management platform with full key and certificate lifecycle management as well as rolebased user permissions and full automation capabilities.
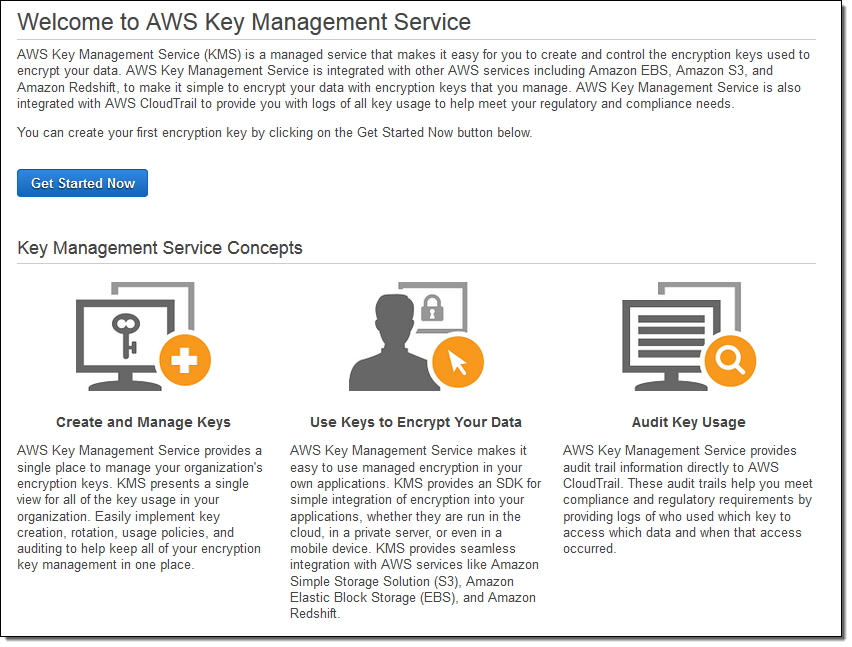
The Key Management Server must support the Key Management Interoperability Protocol (KMIP) 11 standard See the vSphere Compatibility Matrices for details You can find information about VMware certified KMS vendors in the VMware Compatibility Guide under Platform and Compute. A key management virtual appliance;. AWS Key Management Service (KMS) makes it easy for you to create and manage cryptographic keys and control their use across a wide range of AWS services and in your applications AWS KMS is a secure and resilient service that uses hardware security modules that have been validated under FIPS 1402, or are in the process of being validated, to.
Encryption key management is administering the full lifecycle of cryptographic keys This includes generating, using, storing, archiving, and deleting of keys Protection of the encryption keys includes limiting access to the keys physically, logically, and through user/role access Click here to view this eBook offline. When a key management server activates a client that's running Vista, the activation is only good for six months By default, client computers contact the key management server once a week to renew. AWS Key Management Service (KMS) Easily create and control the keys used to encrypt or digitally sign your data Create an AWS Account AWS Key Management Service (KMS) makes it easy for you to create and manage cryptographic keys and control their use across a wide range of AWS services and in your applications.
VMwarecertified key management CloudLink is a certified VMware Ready™ Key Management Server (KMS), giving customers granular control of VMs and data Easily secure your data and meet compliance needs Now you can leverage a single offering to secure and manage sensitive data in the cloud and on premises. Key Management Interoperability Protocol (KMIP) As defined by OASIS, KMIP is a communication “protocol used for the communication between clients and servers to perform certain management operations on objects stored and maintained by a key management system” This protocol is a standardized way of managing encryption keys throughout the lifecycle of the key and is designed to facilitate “symmetric and asymmetric cryptographic keys, digital certificates, and templates used to simplify. The KeyZone software suite is SaaS software KeyZone is key management software, and includes features such as access Controls/Permissions, audit trail, checkin / checkout, and master key management Some competitor software products to KeyZone include SimpleK, KeyCop Manager, and Google Cloud Key Management.
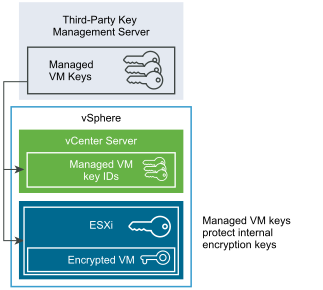
Vsphere Virtual Machine Encryption Components

Cloud Key Management Service Deep Dive Documentation Google Cloud

Etri Etri Journal 1225 6463 2233 7326 Electronics And Telecommunications Research Institute Etri Etri J001 15 V37n4 696 10 4218 Etrij 15 0114 08 Articles Efficient Key Management Protocol For Secure Rtmp Video Streaming Toward
Key Management Server のギャラリー
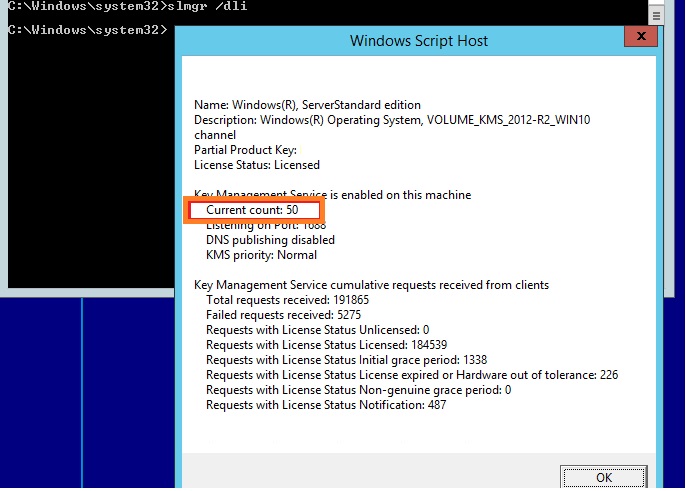
How To Increase Kms Current Count Count Is Insufficient Windows Os Hub

Vormetric To Demonstrate Cryptographic Key Management
Q Tbn And9gcshg7brmyi40xnr Gk0f Awrhjcq6 Bqohkxzsvhcc0v4tn1kiu Usqp Cau

Encryption Key Management System Winmagic

Deep Dive Into Vsphere Vm Encryption Datacenter Rookie

Activation Key An Overview Sciencedirect Topics
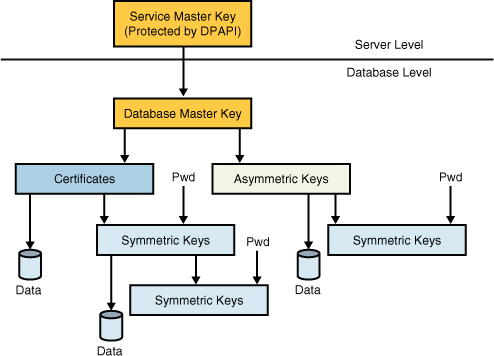
Sql Server 08 Data Encryption Sql Server Key Management Microsoft Certification Examples Exercises Practises Tutorials Solutions About Database

Moving Your Key Management Server Kms To Another Server Or Host Yuri S Technology Blog
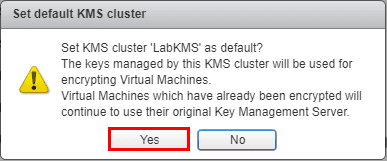
Vmware Virtual Machine Encryption Key Management Virtualization Howto
Key Management Servers
Kms Server Deployment Step By Step Guide Welcome To Mohammed Hamada S Site

Introducing Amazon Ecr Server Side Encryption Using Aws Key Management System Containers
Logging In To The Key Management Server S Management Interface Oceanstor V5 Series V500r007 Encryption User Guide Huawei

Create External Security Key
Volume Activation For Windows Configuring Kms With Ad Roles For Windows 12 12r2 Interworks

Microsoft Key Management Server Kms Reporting Inventory Best Practices Tarun Wadhawan S Diary

Key Management Wikipedia

Securing Data At Rest With Encryption Vox
Svkms Data Sheet Encryption Key Management Stormagic

Key Management Server Kms Cloud Vmware Code

Ibm Knowledge Center

Hardware Based Encryption Workflow
Key Management Wikipedia
How To Setup Kms Key Management Server For Activating Windows 10 Youtube
Nutanix Software Data Encryption With Native Key Management Server Nutanix Hyperconverge Infrastructure
Encryption Key Management Server Kms Application Aria

Ssh Key Management Why You Must Not Manage Ssh Keys Manually

Testing The Key Management Server Kms Youtube

Moving Your Key Management Server Kms To Another Server Or Host Yuri S Technology Blog

Security Policy And Key Management Centrally Manage Encryption Keys
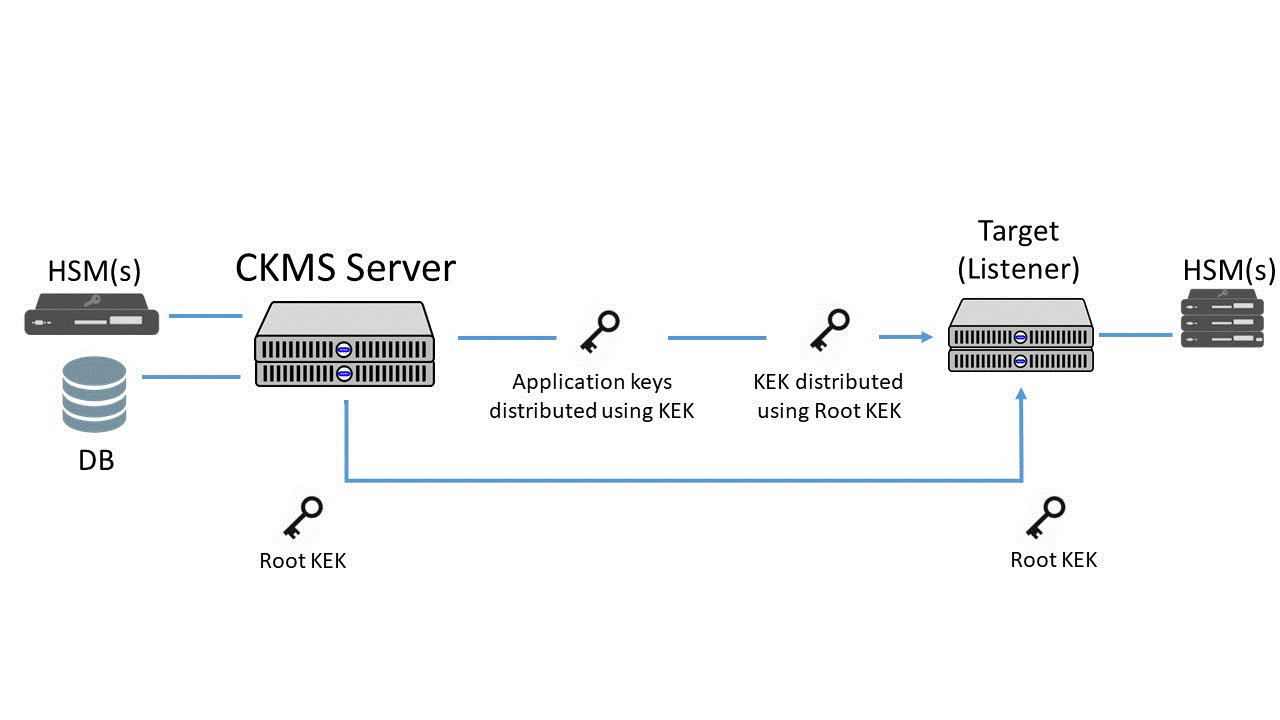
The Link Between Hsms And A Centralized Key Management System
Windows 7 0xc004f074 The Key Management Server Kms Is Unavailable

Key Management An Overview Sciencedirect Topics
Nutanix Software Data Encryption With Native Key Management Server Nutanix Hyperconverge Infrastructure
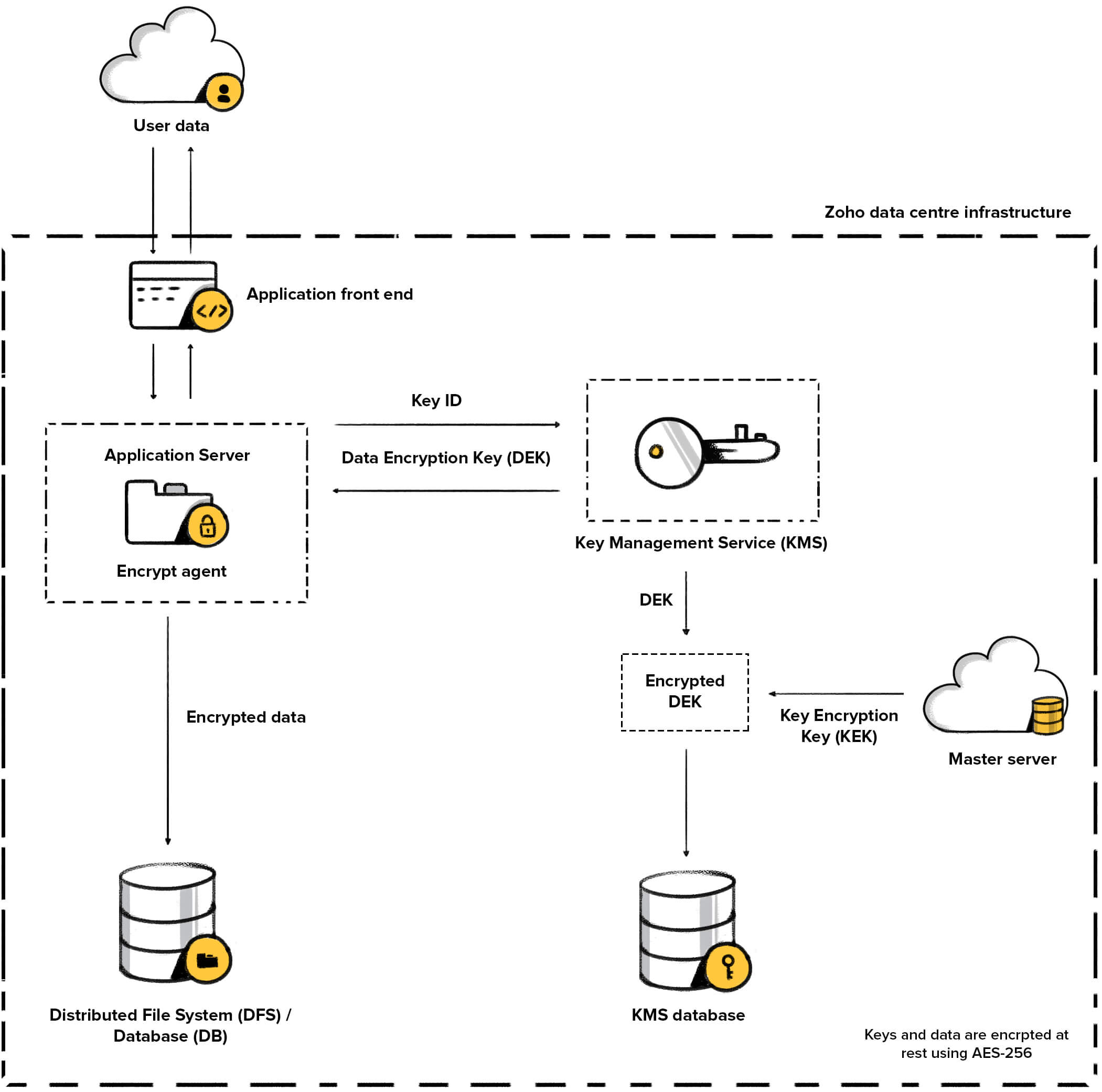
Encryption At Zoho

New Pgp Key Management Server Help Net Security
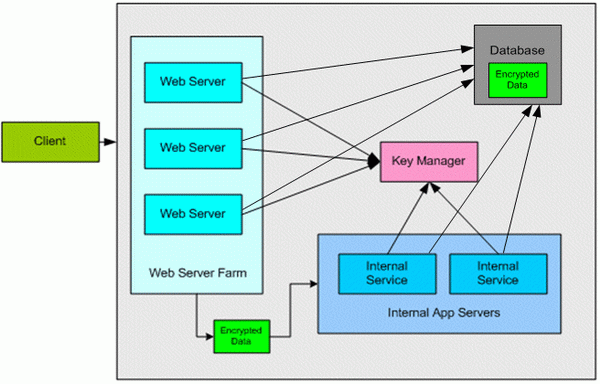
Central Key Management Codeproject

Key Management Service Volume License Activation System Center Spartan

How To Activate Windows With Your Kms Server Kms License Key List

Windows Server Registering A Key Management Service Kms Host Server In Dns Dell Us
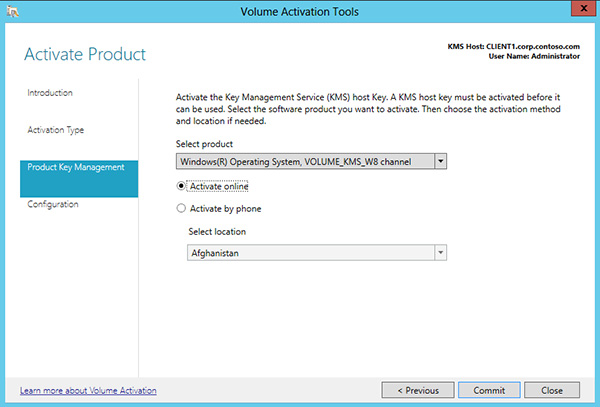
Activate Using Key Management Service Windows 10 Windows Deployment Microsoft Docs
Upgrading A Key Management Server Oceanstor Dorado V3 Series V300r001 Disk Encryption User Guide Huawei

Symantec Pgp Key Management Server Initial Maintenance 1 Year 1 Serve Enc Kms Sup 50 100 Security Cdw Com

Encryption Key Management Software Virtru
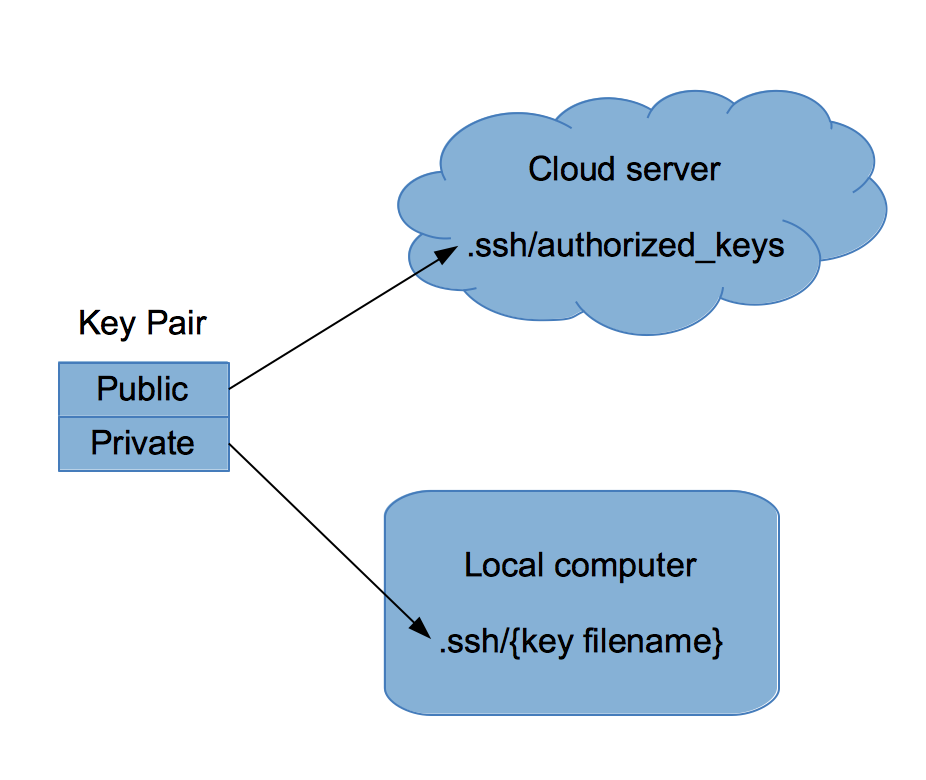
How To Best Manage Encryption Keys On Linux Linux Com

Key Management System Tableau

Cryptomanager Provisioning Security Ip Rambus
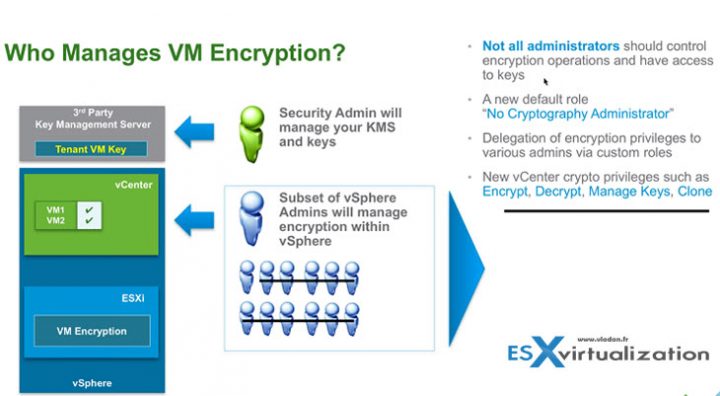
Free Nfr Keys For Kms From Hytrust For All Vmware Vexperts Esx Virtualization
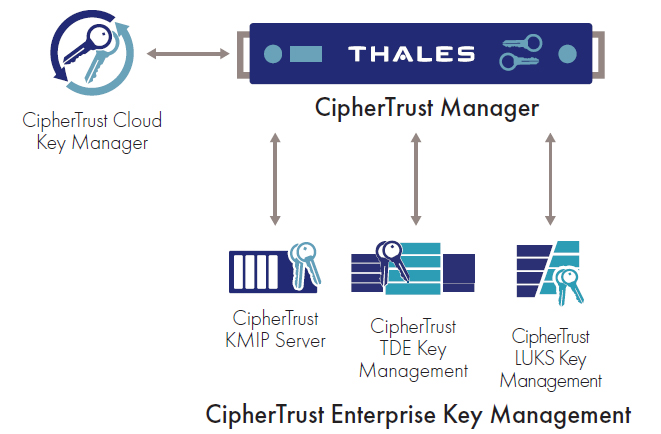
Enterprise Key Management Thales

Third Party Key Management

Key Management Service Aws News Blog
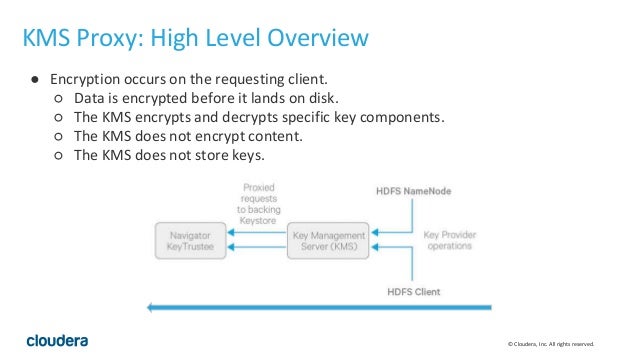
Hadoop Distributed File System Hdfs Encryption With Cloudera Naviga
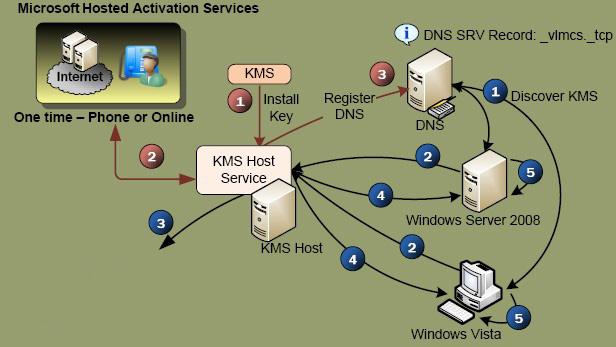
Microsoft Kms Volume Activation Faq Windows Os Hub

Cisco Mds 9000 Family Storage Media Encryption Configuration Guide Cisco Sme Cluster Management Cisco Mds 9000 Nx Os And San Os Software Cisco Systems

Nutanix Software Data Encryption With Native Key Management Server Nutanix Hyperconverge Infrastructure
Ieeexplore Ieee Org Iel7 Pdf
Q Tbn And9gcq7 Cbw5ng7lvptj5q1pancuyy1uywzmthq9w0jldsg1pi6qvtm Usqp Cau

Introducing Amazon Ecr Server Side Encryption Using Aws Key Management System Containers
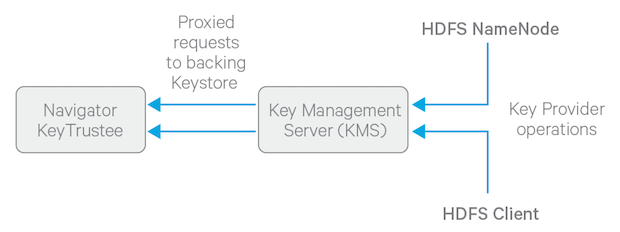
Keystores And The Hadoop Key Management Server
Q Tbn And9gctyxwkimmuarjngbaghd6vtjpqgl6cyq0bn78zfsgbeuvkm4vwr Usqp Cau

Controller Swap With External Key Management And All Drives Secured

Kmsa Key Management Server Administrator By Acronymsandslang Com

Restoring A Key Management Server To Factory Settings Oceanstor V5 Series V500r007 Encryption User Guide Huawei
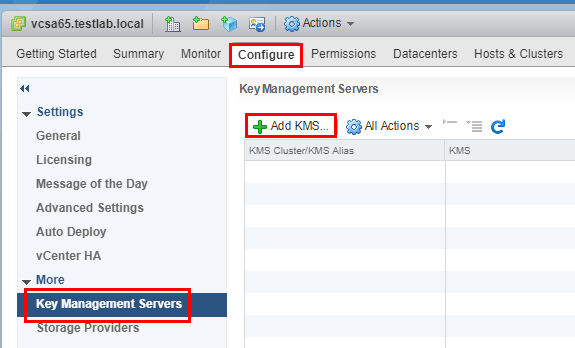
Vmware Virtual Machine Encryption Key Management Virtualization Howto

Configure Safenet As A Kmip Complaint Server Marklogic Community

Vmware Virtual Machine Encryption Key Management Virtualization Howto
Http Www Falkensecurenetworks Com Pdfs Voltage Key Management Server Pdf
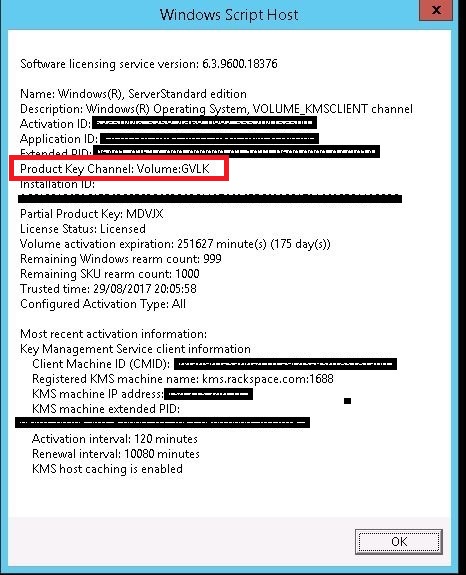
Common Windows Issues Key Management Server Activation Rackspace Developer Center
The Definitive Guide To Vmware Encryption And Key Management
Simple And Secure Infrastructure Management With An External Key Management Server Nutanix Community

Oceanstor V5 Series V500r007 Encryption User Guide Huawei

Aria Key Management Server Cybersecurity Excellence Awards
Kms Key Management Server By Acronymsandslang Com
New Aws Key Management Service Kms Aws News Blog
Http Mysupport Download Microfocus Com Sso Online Help Discovery Autonomy digital Connected mx Connected mx kms 1 0 Guides Pdf English Cmx Kms 1 0 Install En Pdf
Restoring The Key Management Server To Factory Settings Oceanstor Dorado V3 Series V300r001 Disk Encryption User Guide Huawei

Activation Key Management Best Practices

Installing Kms Server On Windows Server 12 R2 Windows Os Hub
2
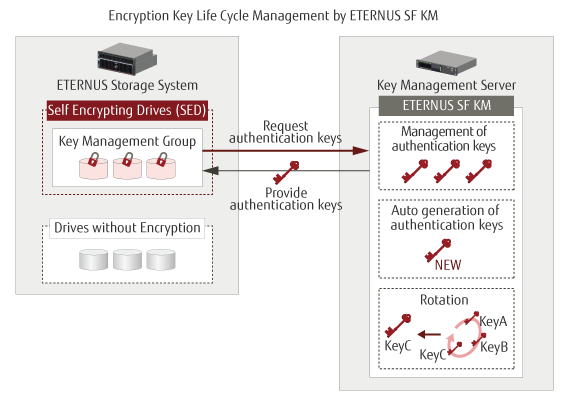
Fujitsu Storage Eternus Sf Km Features Fujitsu Global
Configuring A Key Management Server Cluster Oceanstor Dorado V3 Series V300r001 Disk Encryption User Guide Huawei

Part 4 Sql Server Tde And Extensible Key Management Using Azure Key Vault Microsoft Tech Community
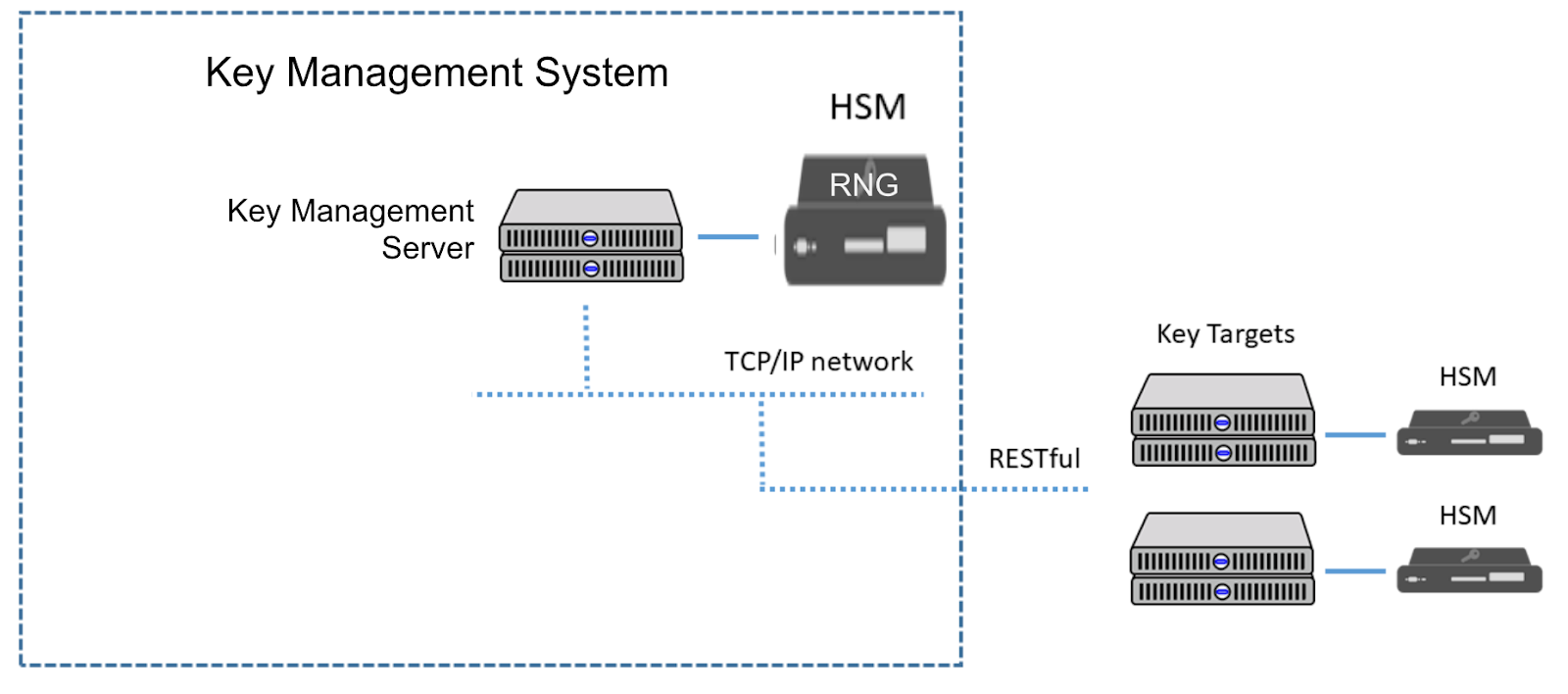
The Role Of Random Number Generators In Relation To Hsms Key Management
Www Delltechnologies Com En Us Collaterals Unauth White Papers Products Servers Sekm Setup And Deployment Guide White Paper Pdf

Windows Server Registering A Key Management Service Kms Host Server In Dns Dell Us
Www Delltechnologies Com En Us Collaterals Unauth White Papers Products Servers Sekm Setup And Deployment Guide White Paper Pdf
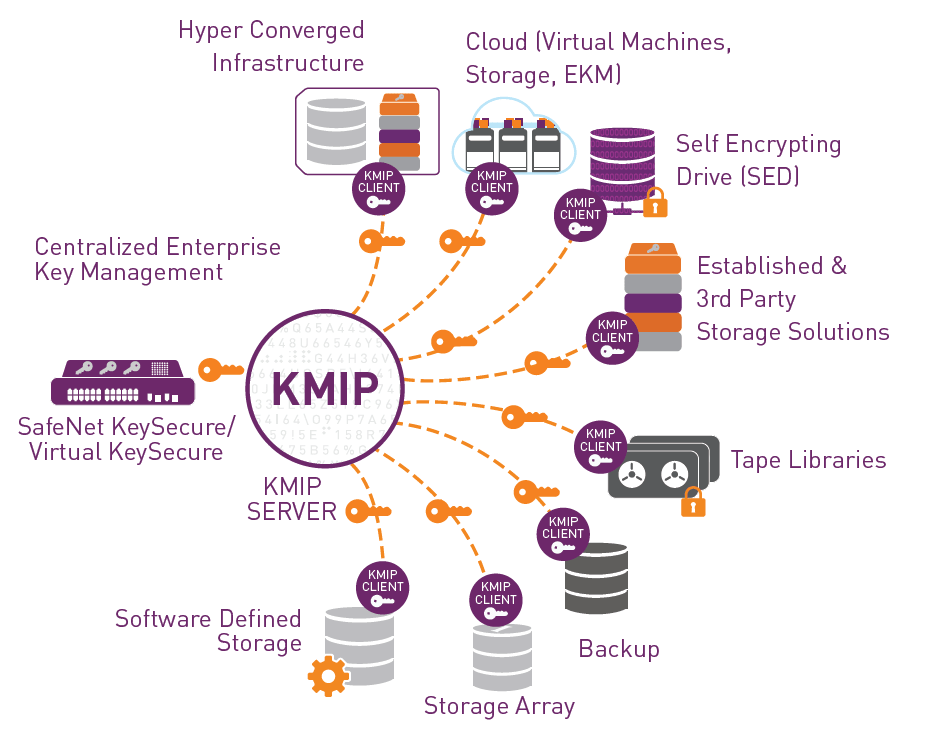
What Is The Key Management Interoperability Protocol Kmip The Benefit Of A Kmip Compliant Key Manager Thales Blog
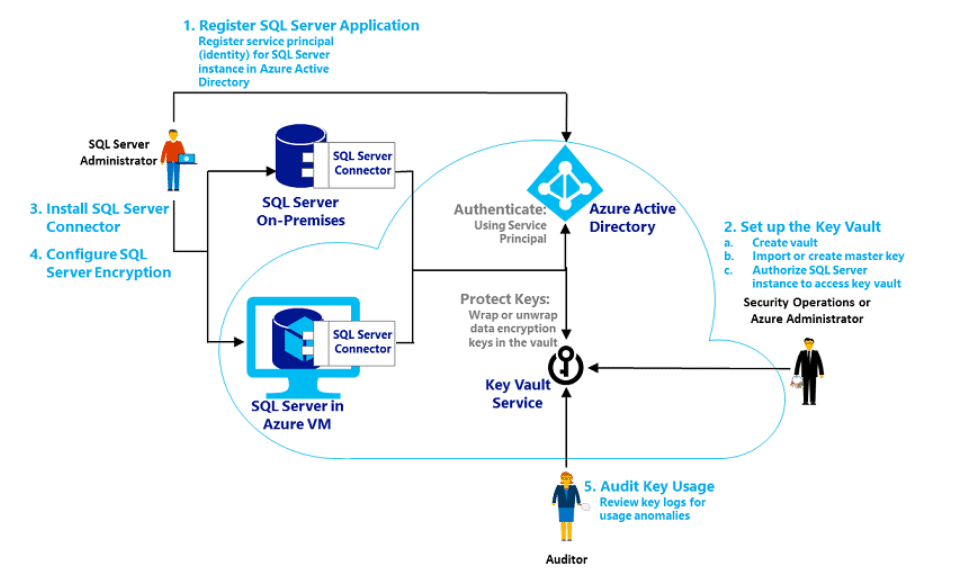
Configure Extensible Key Management Using Azure Key Vault Level 3 Of The Stairway To Tde Sqlservercentral

Customer Controlled Key Management Services With Sap Data Custodian Sap Blogs

Securosis Blog Article

Installation Of Encryption License Key Hitachi Vantara Knowledge

Setting Up A Kms Server Windows Server 12r2 Scom Other Geeky Stuff

Centralized Encryption Key Management Server Kms Townsend Security

Understanding Vsan Encryption Kms Server Accessibility Virtual Blocks
Centralized Encryption Key Management Server Kms Townsend Security

Vsphere Virtual Machine Encryption Components
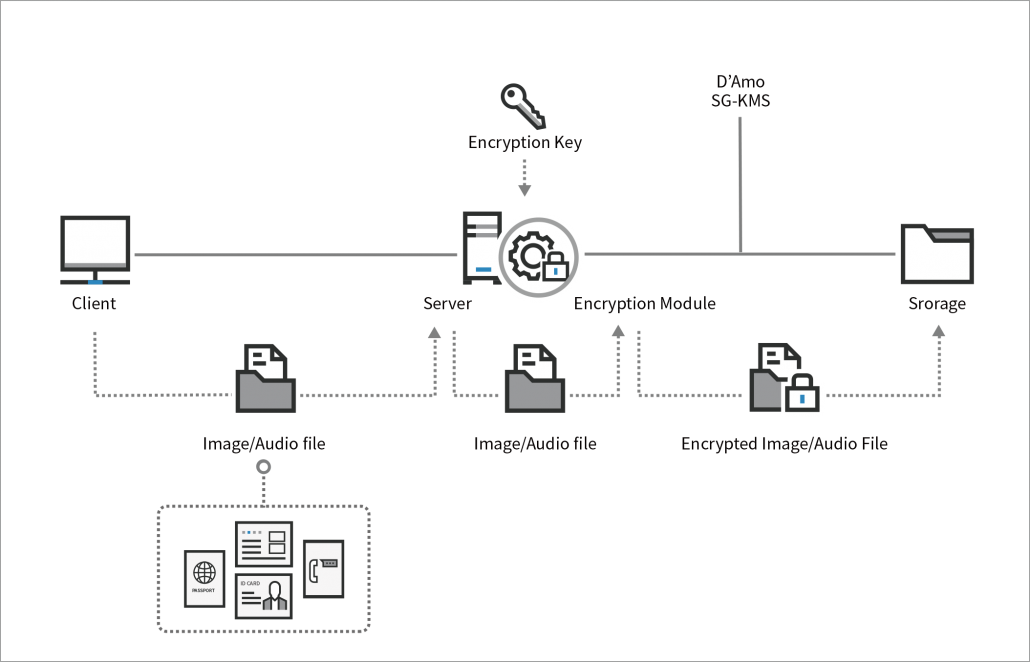
Enterprise Key Management Penta Security Systems Inc

Vsphere Vms Encryption Kms Server Installation Pt 1 Nolabnoparty
Q Tbn And9gcrxm9lz9dajwbhrmj Vj1wkxqjtxrvzbwcz4zghknlfngcnrb0x Usqp Cau

Ssh Key Management Dt Asia Group Singapore File System Syslog Firewall Database Banking Security Privileged Access Solution
.png)
Guidelines For Troubleshooting Kms Microsoft Docs



