Security Architecture
A zero trust security architecture is designed to reduce cybersecurity risk by eliminating implicit trust within an organization’s IT infrastructure With a zero trust security model, access to corporate resources is granted or denied based upon the access and permissions assigned to a particular.
Security architecture. The security architecture methodology and guidance given here can help in structuring the security architecture itself By providing mechanisms for moving from uncoordinated activities to a structured and highly logical approach, the implementation of this model enables the enterprise to support all security as it provides the alignment of an. # Security Architecture The strict separation of customer workloads is based on the MODS security architecture Separation of the customer VMs (and therefore CDBs) is implemented by OVM hardening measures On database level strict isolation of PDB from CDB (and between multiple PDBs) is the foundation of the security architecture. A security architecture program is a unified set of processes that help identify potential security risks, address vulnerabilities, and lays out a plan of action should a risk turn into an actual security threat To create an enterprise security architecture program, it's essential to map out all informational assets within an organization.
A customer identity and access management architecture can fill the gaps left behind by traditional IAM products Learn about the security and business benefits of CIAM, as well as criteria to. A customer identity and access management architecture can fill the gaps left behind by traditional IAM products Learn about the security and business benefits of CIAM, as well as criteria to. The cloud security architecture plan may vary from model to model So it is necessary to understand cloud computing security architecture for every model separately IaaS Cloud Computing Security Architecture Infrastructure as a service architecture has majorly security and networking tools to protect the network of data.
Luciana Obregon is a security architect at PayPal Holdings, Inc, a worldwide online payments system and money transfer company Prior to PayPal, Luciana spent nine years working for Marathon Petroleum Corporation serving under several capacities, including security solutions architecture, security engineering and network security engineering. Security architecture addresses the problem of disjointed and ineffective security implementations that lead to compromise of data or system or business failure The design of an integrated and resilient security framework is the goal of this course on Security Architecture In this course, Security Architecture, you will learn the value of. Enterprise Security Architecture a Serious Concern Across all industries and organizations, information security is a top priority From ransomware to phishing and hacking into IoT devices, the risk landscape is constantly evolving Businesses battle these threats through the use of tools such as firewalls, intrusion detection systems, and.
SEC545, Cloud Security Architecture and Operations, is the industryâs first indepth cloud security course that covers the entire spectrum of cloud security knowledge areas, with an emphasis on technical control design and operations. SEC545, Cloud Security Architecture and Operations, is the industryâs first indepth cloud security course that covers the entire spectrum of cloud security knowledge areas, with an emphasis on technical control design and operations. # Security Architecture The strict separation of customer workloads is based on the MODS security architecture Separation of the customer VMs (and therefore CDBs) is implemented by OVM hardening measures On database level strict isolation of PDB from CDB (and between multiple PDBs) is the foundation of the security architecture.
General web application architecture may contain serious security flaws Web application security is an attempt to remediate these This article will help identify ways to create a secure web application architecture We’ll consider the benefits of multitier architecture versus the use of single or twotier web application architectures. Network security and architecture;. Create a security architecture or design and document the different layers of protection If one security service fails the security system should still be resistant against threads Compartmentalize and work with secure boundaries for information flows.
The Ooni of Ife, Oba Adeyeye Ogunwusi on Wednesday disclosed that traditional security architecture saved Ife town from wanton destruction of property when hoodlums hijacked the EndSARS protest in. Security architecture is a unified security design that addresses the necessities and potential risks involved in a certain scenario or environment It also specifies when and where to apply security controls The design process is generally reproducible. A set of physical and logical securityrelevant representations (ie, views) of system architecture that conveys information about how the system is partitioned into security domains and makes use of securityrelevant elements to enforce security policies within and between security domains based on how data and information must be protected.
The security architecture should protect all elements of the company's IT environment — from publicly accessible Web and email servers and financial reporting systems to confidential human resources (HR) data and private customer information To address this breadth of resources and information, it is vital that a consistent architecture be. Enterprise security architecture is a comprehensive plan for ensuring the overall security of a business using the available security technologies. The cloud security architecture plan may vary from model to model So it is necessary to understand cloud computing security architecture for every model separately IaaS Cloud Computing Security Architecture Infrastructure as a service architecture has majorly security and networking tools to protect the network of data.
Security Architecture and Design describes fundamental logical hardware, operating system, and software security components and how to use those components to design, architect, and evaluate secure computer systems Understanding these fundamental issues is critical for an information security professional. Traditionally, security architecture consists of some preventive, detective and corrective controls that are implemented to protect the enterprise infrastructure and applications Some enterprises are doing a better job with security architecture by adding directive controls, including policies and procedures. Luciana Obregon is a security architect at PayPal Holdings, Inc, a worldwide online payments system and money transfer company Prior to PayPal, Luciana spent nine years working for Marathon Petroleum Corporation serving under several capacities, including security solutions architecture, security engineering and network security engineering.
Enterprise information security architecture (EISA) is the practice of applying a comprehensive and rigorous method for describing a current and/or future structure and behavior for an organization's security processes, information security systems, personnel, and organizational subunits so that they align with the organization's core goals and strategic direction. Enterprise Security Architecture a Serious Concern Across all industries and organizations, information security is a top priority From ransomware to phishing and hacking into IoT devices, the risk landscape is constantly evolving Businesses battle these threats through the use of tools such as firewalls, intrusion detection systems, and. Security Architecture is the design artifacts that describe how the security controls (= security countermeasures) are positioned and how they relate to the overall systems architecture These controls serve the purpose to maintain the system’s quality attributes such as confidentiality, integrity and availability.
Security Architecture Security From Ground to Cloud Now that security measures must extend to wherever access decisions are made — home offices, coffee shops, hospital rooms, checkout lines, factory floors, and even inside traditional office spaces — old perimetercentric security models are ineffective at stopping modern threats. “Security architecture is the art and science of designing and supervising the construction of business systems , usually business information systems, which are free from danger, damage, fear. Defenseindepth architecture Layered security Defenseindepth security architecture is based on controls that are designed to protect the physical, technical and administrative aspects of your network Defense in depth, layered security architecture.
The cloud security architecture plan may vary from model to model So it is necessary to understand cloud computing security architecture for every model separately IaaS Cloud Computing Security Architecture Infrastructure as a service architecture has majorly security and networking tools to protect the network of data. "The GIAC Defensible Security Architecture (GDSA) certificate is an industry certification that proves an individual is capable of looking at an enterprise defense holistically A GDSA no longer emphasizing security through a single control but instead applies multiple controls ranging from network security, cloud security, and datacentric. Create a security architecture or design and document the different layers of protection If one security service fails the security system should still be resistant against threads Compartmentalize and work with secure boundaries for information flows.
SEC545, Cloud Security Architecture and Operations, is the industryâs first indepth cloud security course that covers the entire spectrum of cloud security knowledge areas, with an emphasis on technical control design and operations. SEC545, Cloud Security Architecture and Operations, is the industryâs first indepth cloud security course that covers the entire spectrum of cloud security knowledge areas, with an emphasis on technical control design and operations. The Open Group Security Forum has a long history of providing guidance and expertise in the area of security architecture In addition to publishing the Open Security Mobile Architecture (OSMA) Standard, the Security Forum has published documents for a Credentials Program around Integrating Risk and Security within a TOGAF® Enterprise Architecture.
Enterprise and security architecture;. Once the security architecture is there, you need to ensure that it is used by the rest of the organization To accomplish this, communication is key People like visual information, this is a. Security architecture combines hardware and software knowledge with programming proficiency, research skills, and policy development Security architects anticipate potential threats and design systems to preempt them As senior information technology professionals, security architects plan, implement, and supervise computer and network.
Security Architecture Security From Ground to Cloud Now that security measures must extend to wherever access decisions are made — home offices, coffee shops, hospital rooms, checkout lines, factory floors, and even inside traditional office spaces — old perimetercentric security models are ineffective at stopping modern threats. The following diagram provides a highlevel overview of the security architecture Authentication By default, only authenticated users who have user rights can establish a connection Microsoft Azure Active Directory (AAD) is a primary identity provider To access the system, users must be provisioned into a Finance and Operations instance and. # Security Architecture The strict separation of customer workloads is based on the MODS security architecture Separation of the customer VMs (and therefore CDBs) is implemented by OVM hardening measures On database level strict isolation of PDB from CDB (and between multiple PDBs) is the foundation of the security architecture.
Wired and wireless security;. A zero trust security architecture is designed to reduce cybersecurity risk by eliminating implicit trust within an organization’s IT infrastructure With a zero trust security model, access to corporate resources is granted or denied based upon the access and permissions assigned to a particular. The Microsoft Cybersecurity Reference Architecture describes Microsoft’s cybersecurity capabilities and how they integrate with existing security architectures and capabilities We recently updated this diagram and wanted to share a little bit about the changes and the document itself to help you better utilize it.
A zero trust security architecture is designed to reduce cybersecurity risk by eliminating implicit trust within an organization’s IT infrastructure With a zero trust security model, access to corporate resources is granted or denied based upon the access and permissions assigned to a particular. A zero trust security architecture is designed to reduce cybersecurity risk by eliminating implicit trust within an organization’s IT infrastructure With a zero trust security model, access to corporate resources is granted or denied based upon the access and permissions assigned to a particular. Security architecture for cloud applications Use the IBM security architecture to safeguard and monitor your cloud applications and data Architecture Center Security architecture Overview Multicloud identity and access management Network security Application security.
The security architecture is defined as the architectural design that includes all the threats and potential risk which can be present in the environment or that particular scenario This also includes the security controls and the use of security controls For the security architecture, the proper documentation is done that include all the. The security architecture should protect all elements of the company's IT environment — from publicly accessible Web and email servers and financial reporting systems to confidential human resources (HR) data and private customer information To address this breadth of resources and information, it is vital that a consistent architecture be. Security Architecture provides a means for engineers to maintain consistency and traceability in security design Just as a plot of land is charted, a foundation is laid, and framing constructed for a physical building, similar milestones occur in the world of cyber security architecture.
Practicing security architecture provides the right foundation to systematically address business, IT and security concerns in an organization Security measures A state of computer "security" is the conceptual ideal, attained by the use of the three processes threat prevention, detection, and response. A customer identity and access management architecture can fill the gaps left behind by traditional IAM products Learn about the security and business benefits of CIAM, as well as criteria to. # Security Architecture The strict separation of customer workloads is based on the MODS security architecture Separation of the customer VMs (and therefore CDBs) is implemented by OVM hardening measures On database level strict isolation of PDB from CDB (and between multiple PDBs) is the foundation of the security architecture.
As this is a management position you will need excellent written and verbal communication skills It will be vital to know how to maintain staff morale and to inspire creative solutions and innovation. The cloud security architecture plan may vary from model to model So it is necessary to understand cloud computing security architecture for every model separately IaaS Cloud Computing Security Architecture Infrastructure as a service architecture has majorly security and networking tools to protect the network of data. Security architecture and design looks at how information security controls and safeguards are implemented in IT systems in order to protect the confidentiality, integrity, and availability of the data that are used, processed, and stored in those systems.
A customer identity and access management architecture can fill the gaps left behind by traditional IAM products Learn about the security and business benefits of CIAM, as well as criteria to. Defenseindepth architecture Layered security Defenseindepth security architecture is based on controls that are designed to protect the physical, technical and administrative aspects of your network Defense in depth, layered security architecture. Security architecture reviews are nondisruptive studies that uncover systemic security issues in your environment They are ideally suited for organizations wanting to maximize their return on any security technology investment by evaluating their needs and validating the security of their existing deployments The result is an actionable.

Figure 4 From Construction Of Network Security Architecture Based On Formal Specification In Digital Campus Semantic Scholar
Lorawan Security Architecture 17 Download Scientific Diagram

Security Architecture Documentation For Remedy Action Request System 18 08 Bmc Documentation
Security Architecture のギャラリー
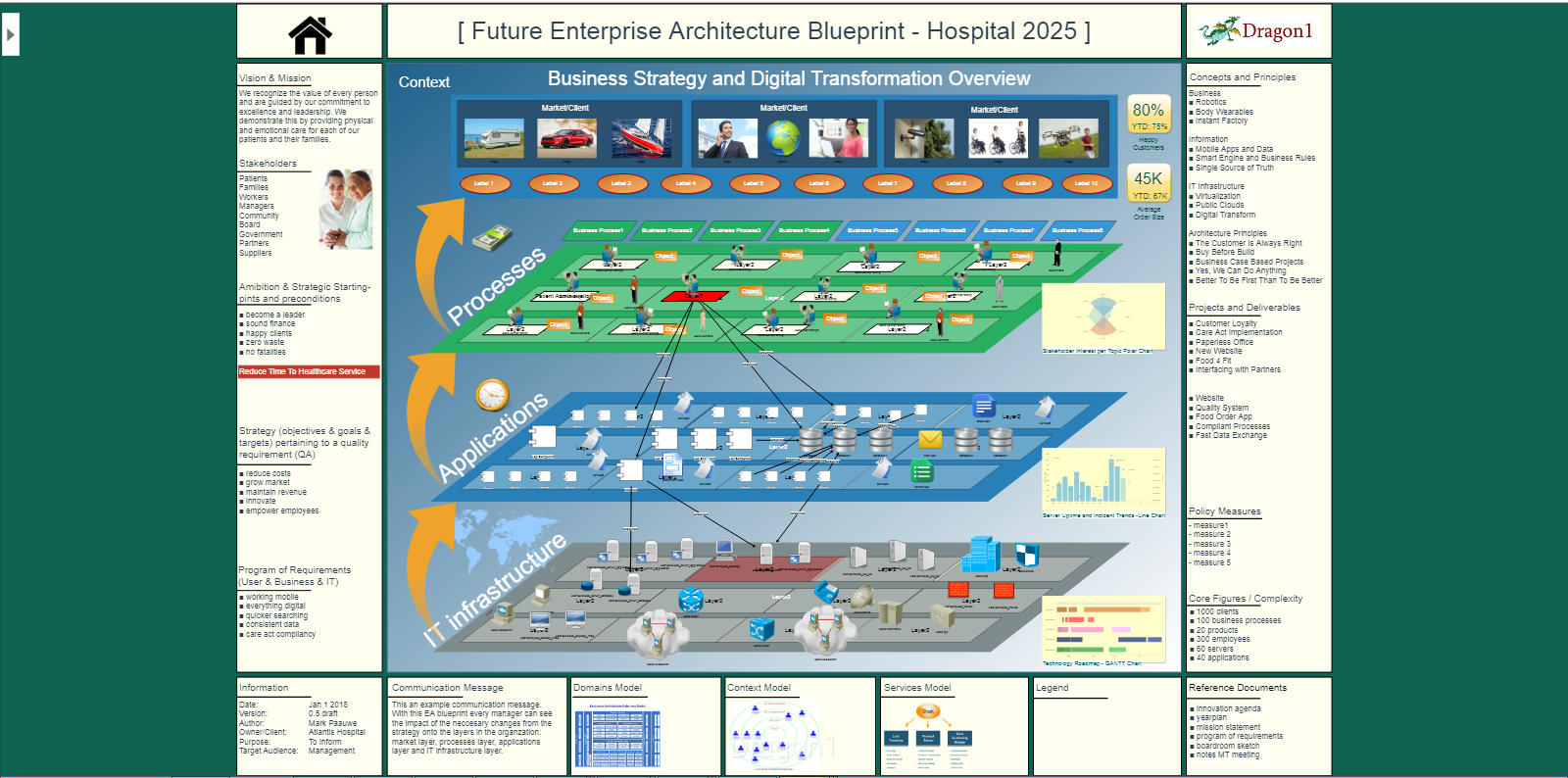
Health Informatics Security Architecture Dragon1

A Security Architecture For Railway Signalling Springerlink
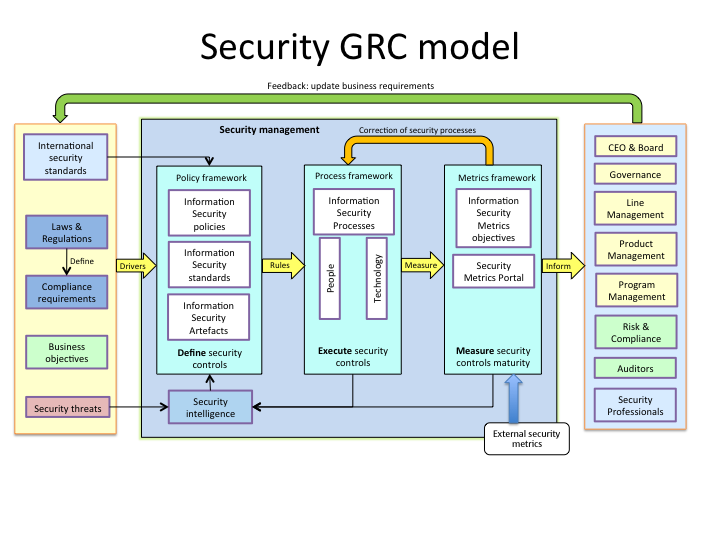
Security Model Business Oriented Security Vladimir Jirasek On Security And Technology

Enterprise Security Architecture 101 Secure Knowledge Management
Best Home Design Information Security Architecture
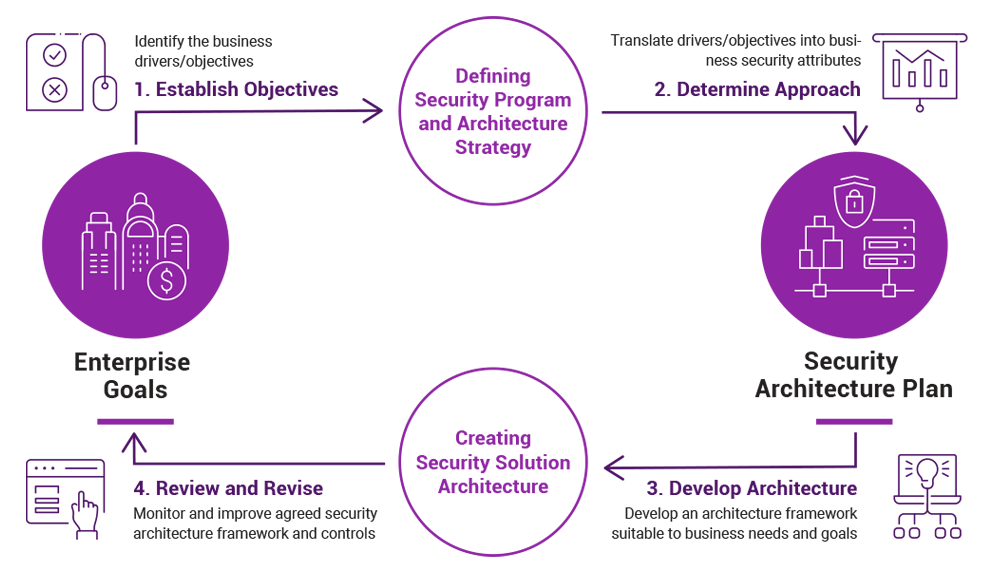
What Is Security Architecture And What Do You Need To Know Dig8ital
Q Tbn And9gcsub8iptin1x8ykdgoxycx4cynjvq170 Fks P8onu Usqp Cau

Oracle S Maximum Security Architecture For Database Security Oracle Cloud Security Blog

Thoughts On Security Architecture For Enterprise Permission D Blockchain Applications By Naresh Kurada Medium

Should Security Architecture Remain Separate From Other Architecture Disciplines James Mcgovern
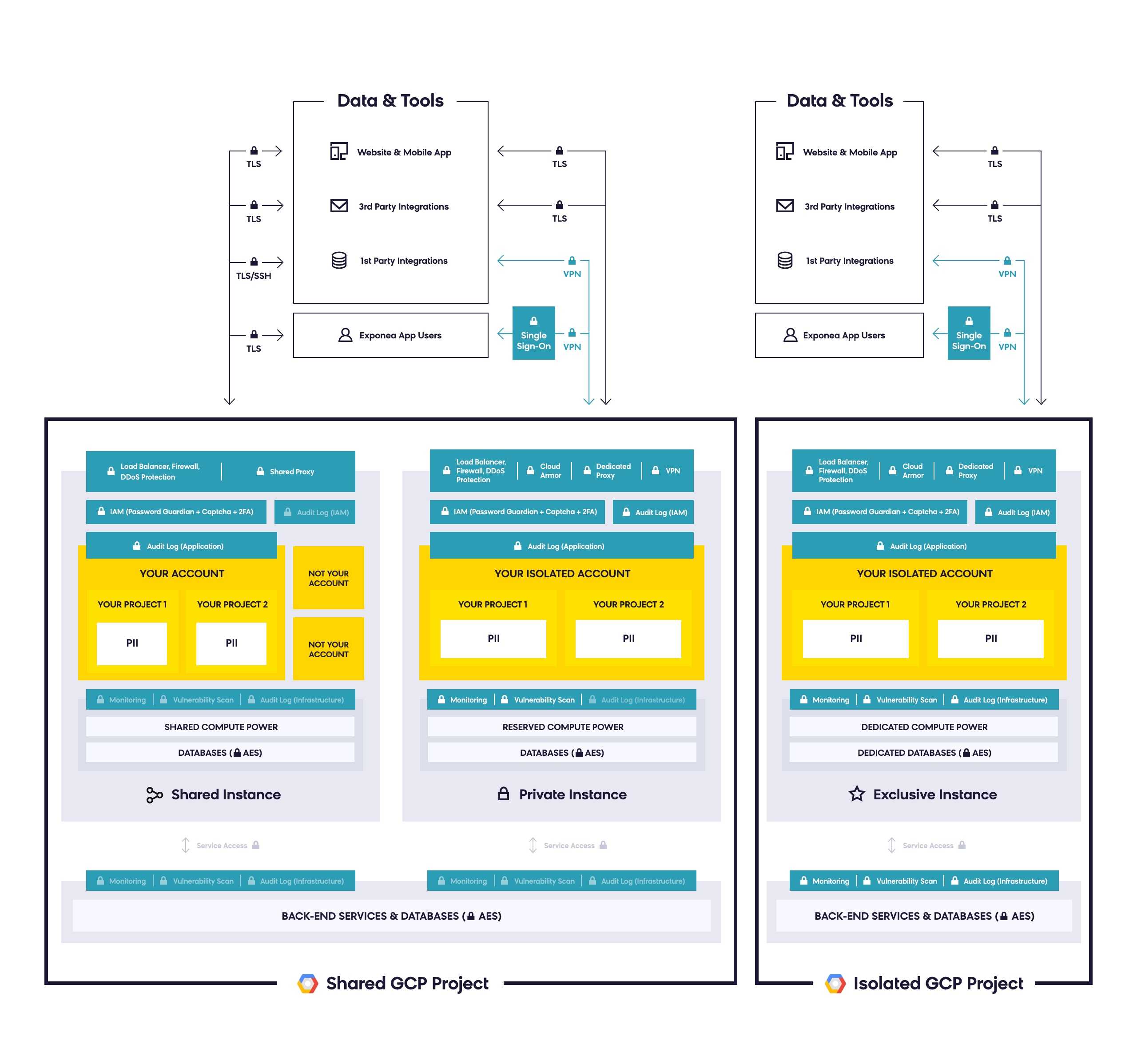
Security Architecture

Topic 5 Security Architecture Enterprise Reflections

Value Proposition Of Business Outcome Driven Cyber Security Architecture

Security Architecture How To Leron Zinatullin S Blog
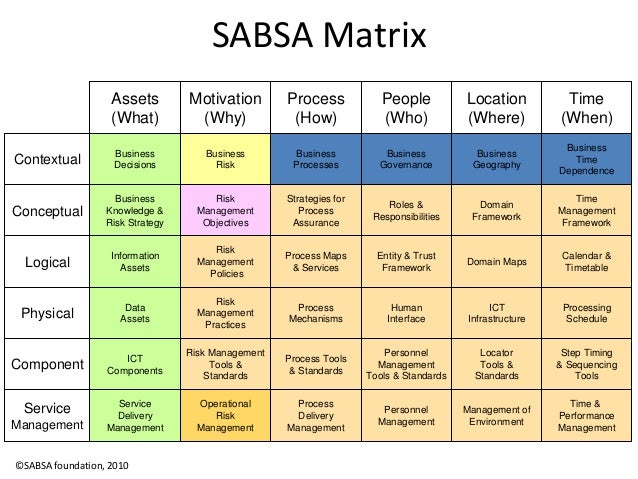
Enterprise Security Architecture Design

Security Architecture Download Scientific Diagram
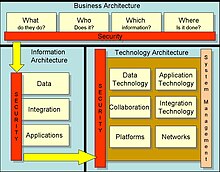
Enterprise Information Security Architecture Wikipedia

Enterprise Security Architecture A Short Overvie Isc Community
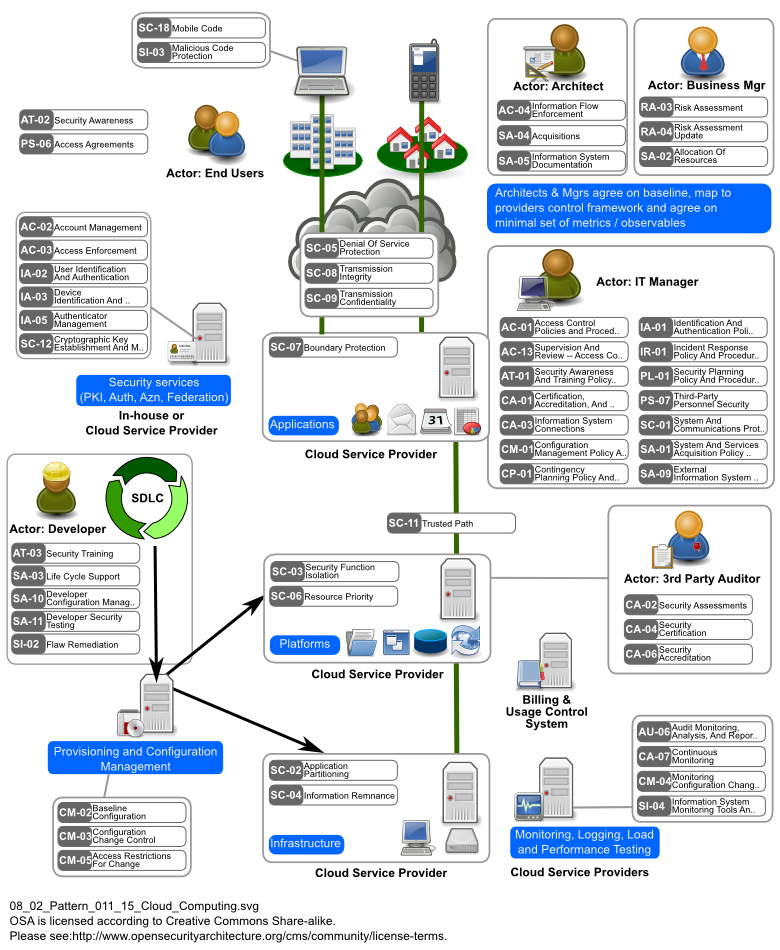
Sp 011 Cloud Computing Pattern
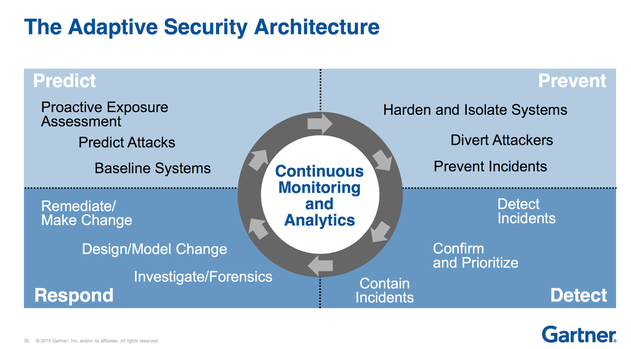
Adaptive Security Architecture Priyanca Pillay

Security Architecture Devops Ibm Cloud Architecture Center

Iot Security Architecture Trust Zones And Boundaries Build5nines

Security Architecture Frameworks

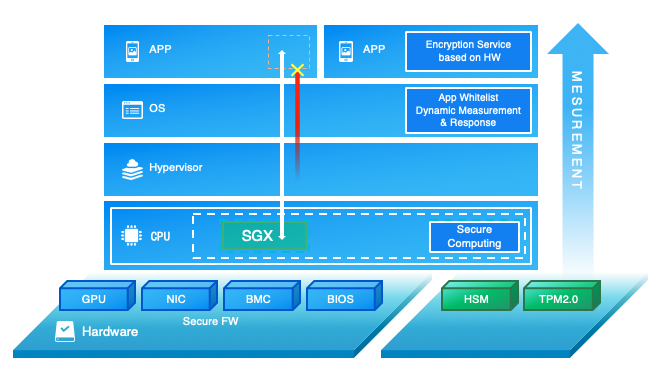
Security Architecture Enables Intel S Digital Transformation

Security Architecture Security Blog

Security Architecture Design Knowledge Synopsys

Operational Technology Architecture Design Yokogawa Europe

Togaf Certification The Open Group Website

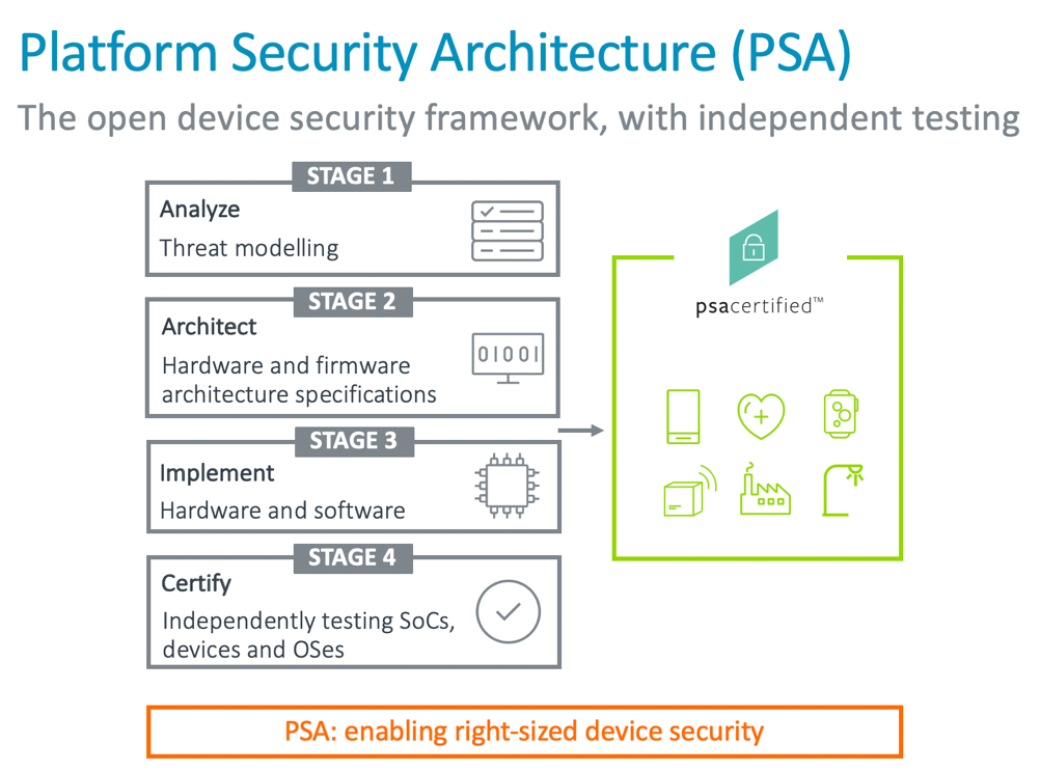
Arm Introduces Psa Platform Security Architecture Pc Perspective

Develop Security Architecture Nige The Security Guy

The Security Architecture Cycle Sogetilabs

History And Evolution Of Adaptive Security Architecture Develop Paper

Develop Security Architecture Nige The Security Guy

Security Architecture Applications Ibm Cloud Architecture Center

Osi Security Architecture Youtube

Adaptive Security Architecture And How Can It Benefit The Organisations
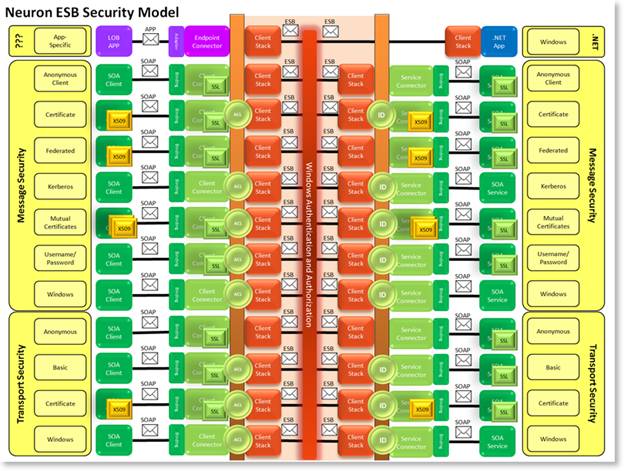
Security Architecture Neuron Esb
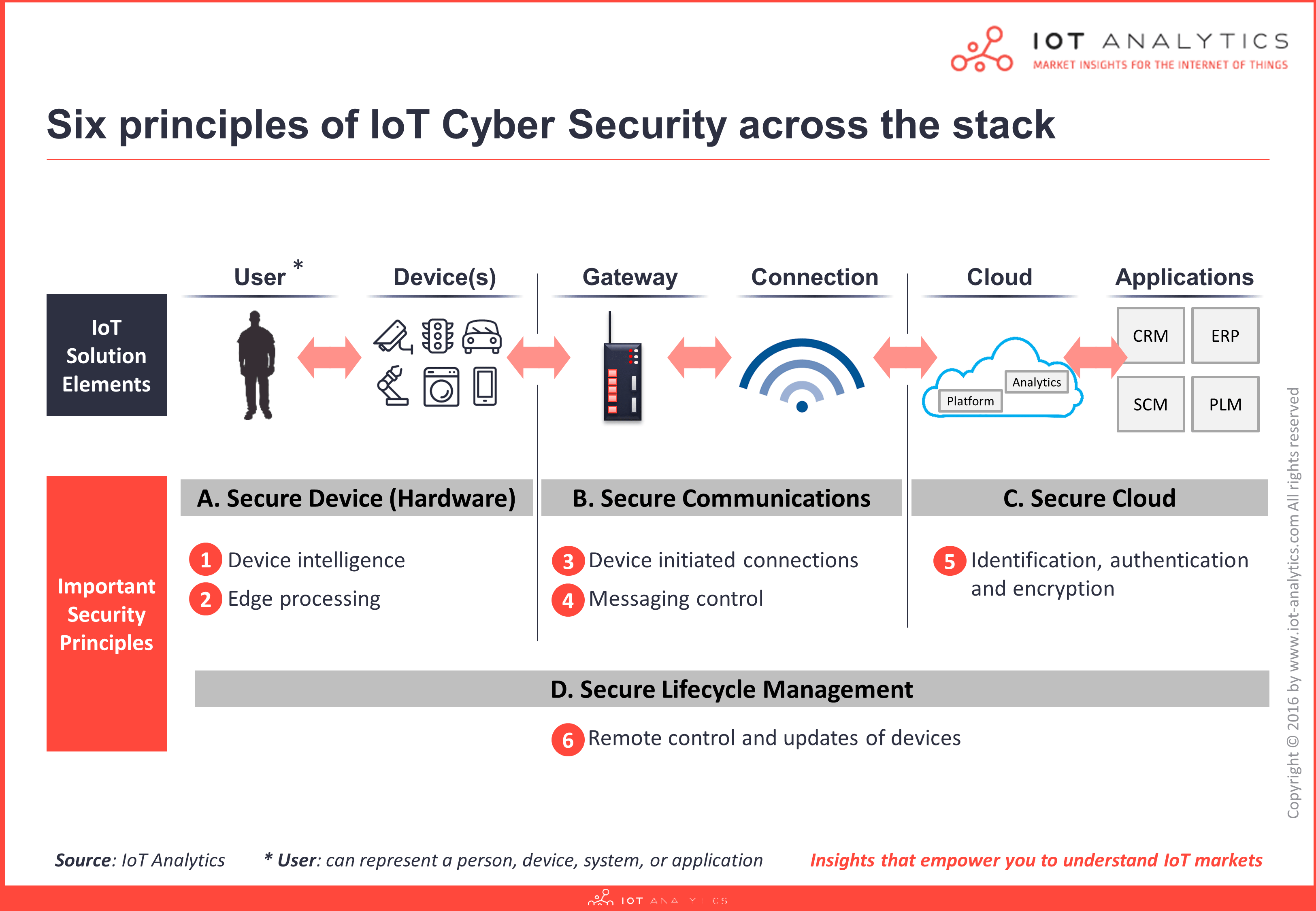
Understanding Iot Security Part 1 Of 3 Iot Security Architecture On The Device And Communication Layers Iot Analytics
3

Adaptive Security Architecture To Protect Companies From Attacks

Holistic View Of The Deep Security Solution Trend Micro

Service Provider Security Architecture Part 2 Cisco Blogs

Cloud Computing Security Architecture For Iaas Saas And Paas

What Is Adaptive Security What Necessitates Its Architecture Around
Www Checkpoint Com Downloads Products Checkpoint Enterprise Security Framework Whitepaper Pdf
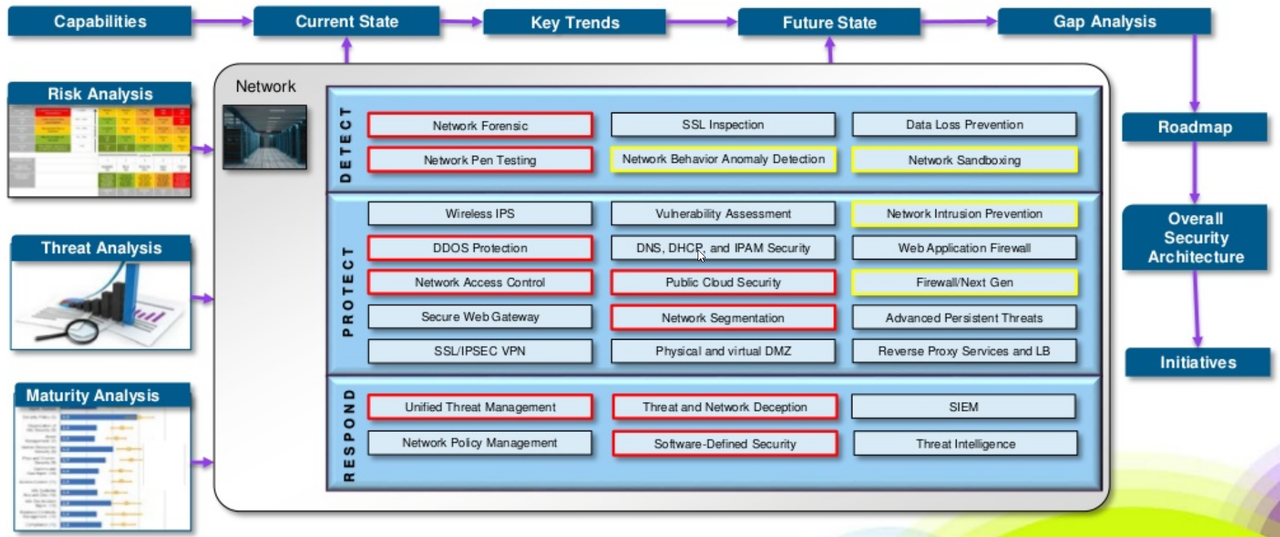
Security Architecture Roadmap Examples Tools Cyber Security Memo
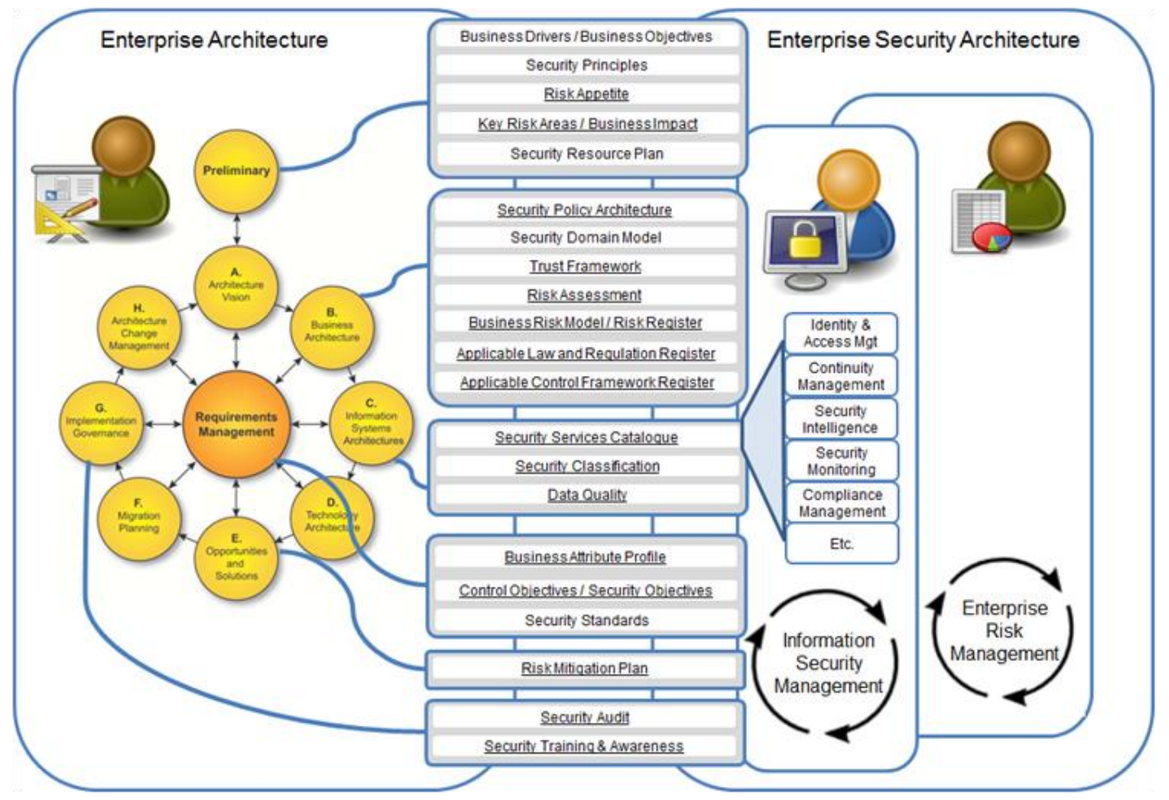
Cyber Security Frameworks And Integrated With Togaf Cyber Security Memo
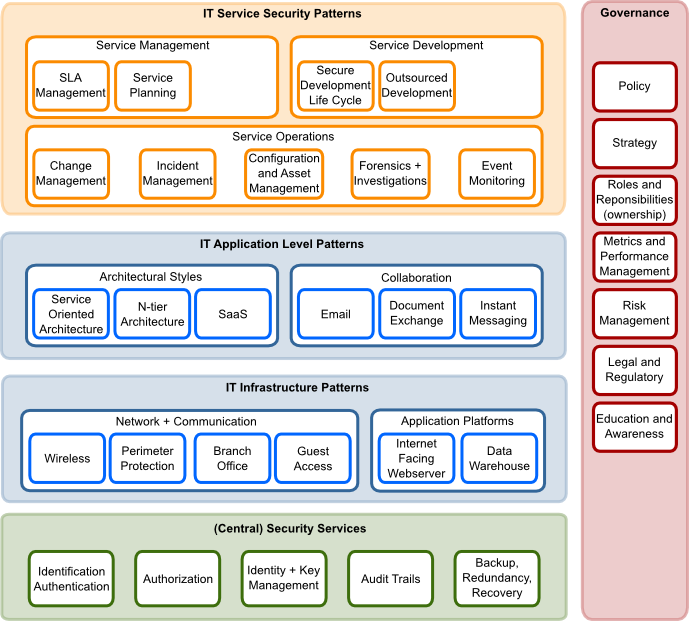
Pattern Landscape

Enterprise Security Architecture A Top Down Approach

Pdf Security Architecture Of The Internet Of Things Oriented To Perceptual Layer Semantic Scholar

From Security Architecture To A Secure Architecture Bizzdesign
Floodgate Security Framework Draft Icon Labs

Enterprise Security Architecture A Top Down Approach

Security Architecture Design Knowledge Synopsys

Cybersecurity Reference Architecture Security For A Hybrid Enterprise Microsoft Security

Ernst Young Review Verifies Tresorit S Security Architecture

Mobile Clients Security Architecture Download Scientific Diagram
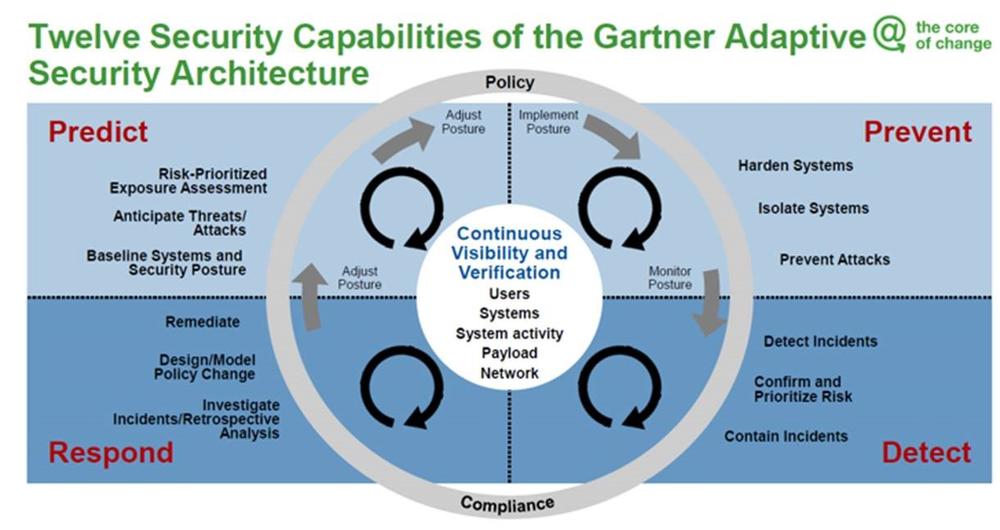
Gartner Adaptive Security Architecture Model

5g Ensure Architecture 5g Ensure

Enterprise Security Architecture A Top Down Approach
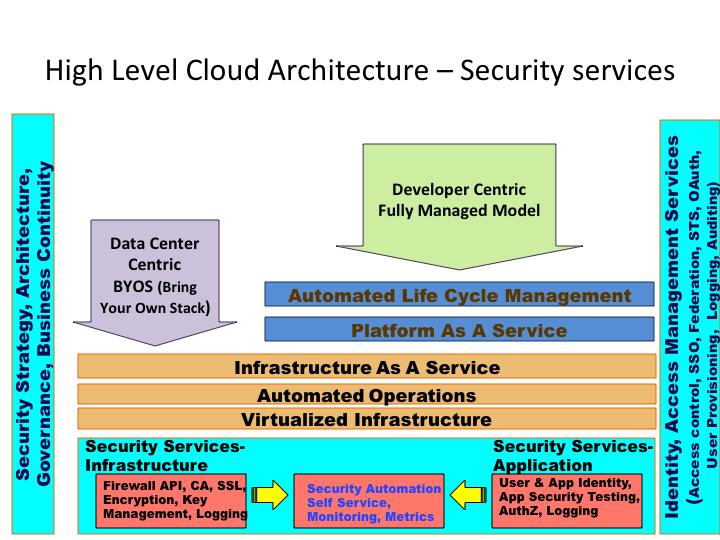
Introduction To Cloud Security Architecture From A Cloud Consumer S Perspective

Building A Cybersecurity Architecture To Combat Today S Threats Logrhythm

At Last What Is Security Architecture Conviso Appsec

Security Architecture
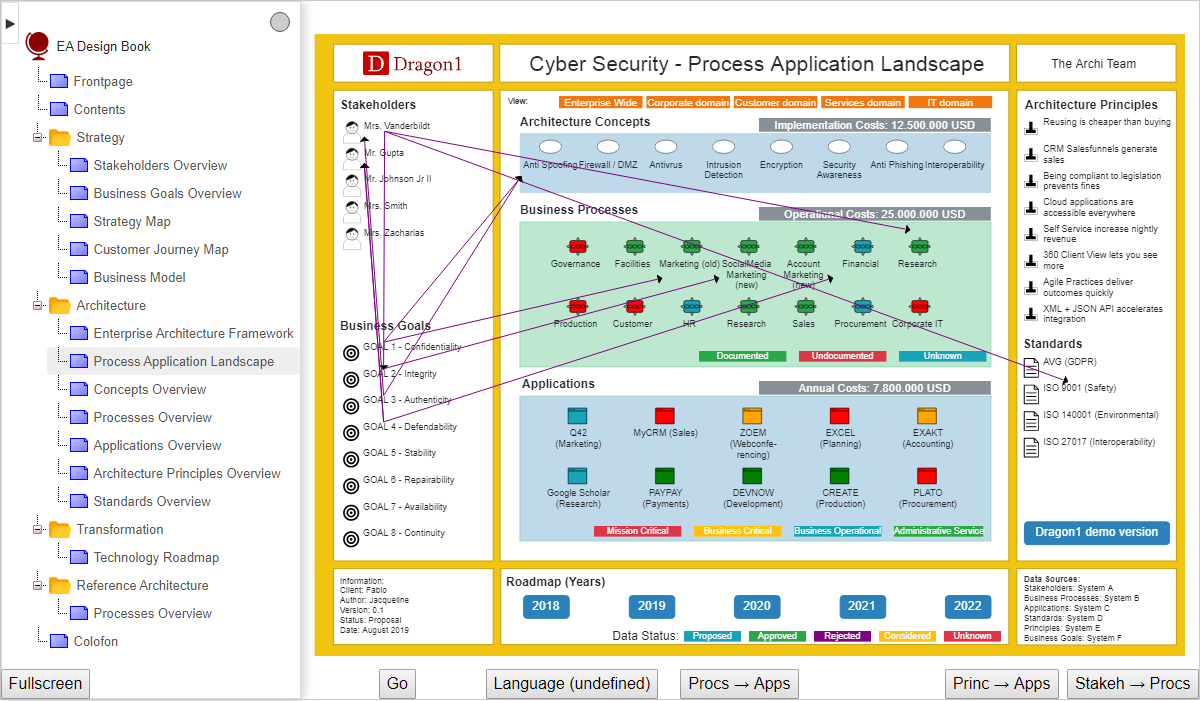
Cyber Security Solution Dragon1
The Iot Architect S Guide To Security Arm Community Internet Of Things Internet Of Things Arm Community

Security Architecture Cloudec V600r019c00 Solution Description Enterprise On Premises Huawei

Security Architecture Policy Governance Risk And Compliance Ibm Cloud Architecture Center

File Huxham Security Framework Jpg Wikipedia

Technical Report Isif Asia

What Is Security Architecture Sogetilabs
Home Secure Constitution Limited
Is Your Data Secure In The Cloud An Overview Of Alibaba Cloud S Data Security Architecture Alibaba Cloud Community
1

Security Architecture Ts Data61

Protect Your Enterprise Analyze Your Security With Architecture Models

Cybersecurity Roadmap Global Healthcare Security Architecture Rsa Conference
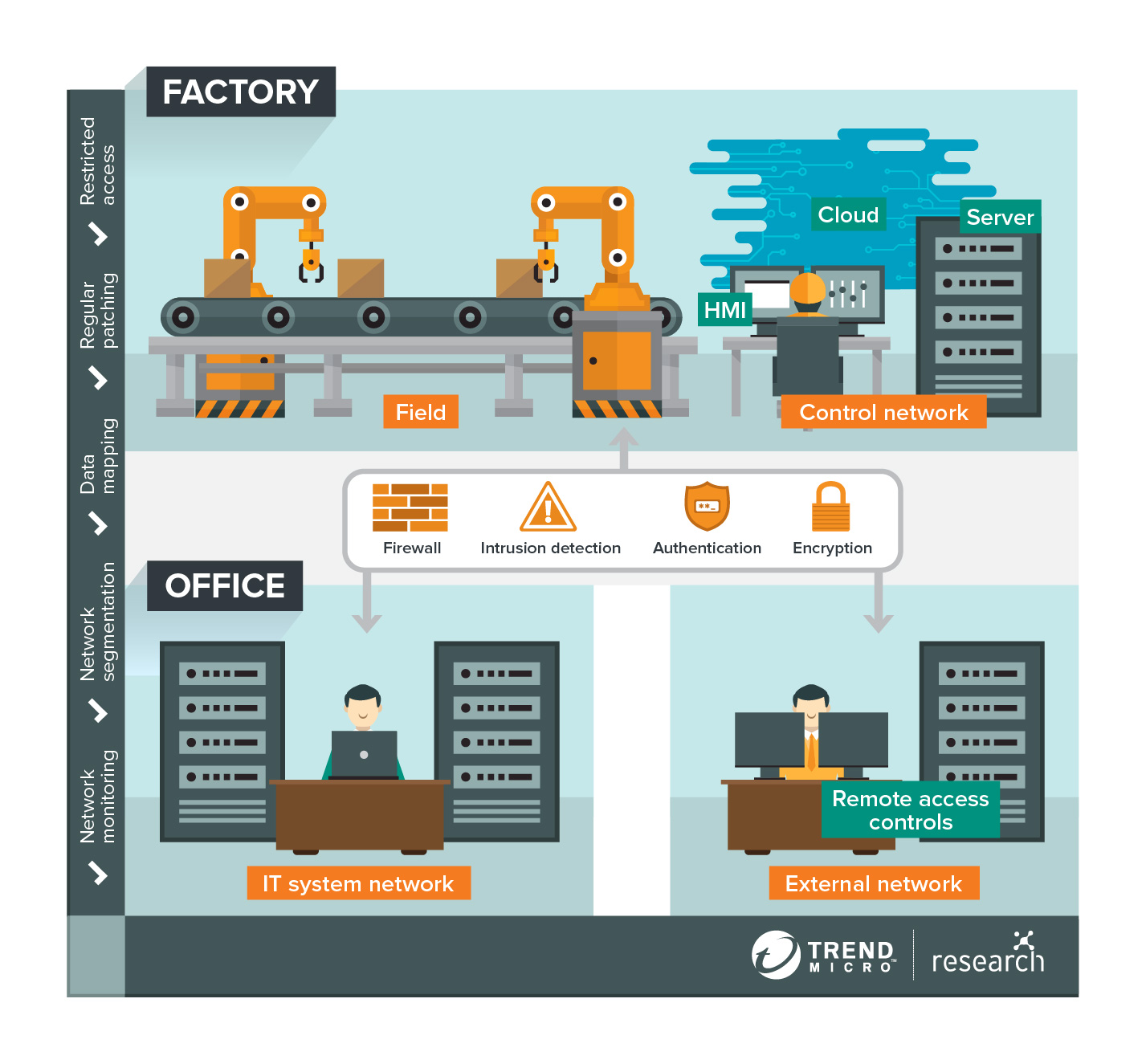
Security Architecture For Smart Factories Security News

Logical Layer Tanya Arora S Portfolio
Integrated Endpoint Security Architecture Wwt

Proposed Physical Security Architecture Download Scientific Diagram
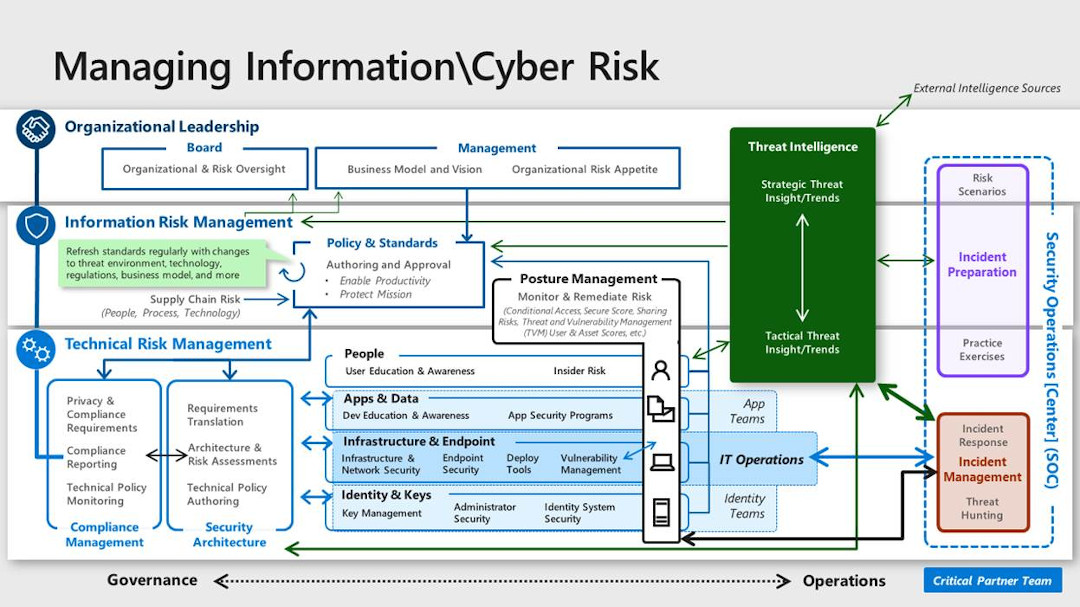
Cloud Security Functions Cloud Adoption Framework Microsoft Docs

Modern Network Security Must Have These Features Cso Online

Security Architecture Design Phase The Concept Of A Threat Intelligence Driven Defendable Architecture Telenor Group
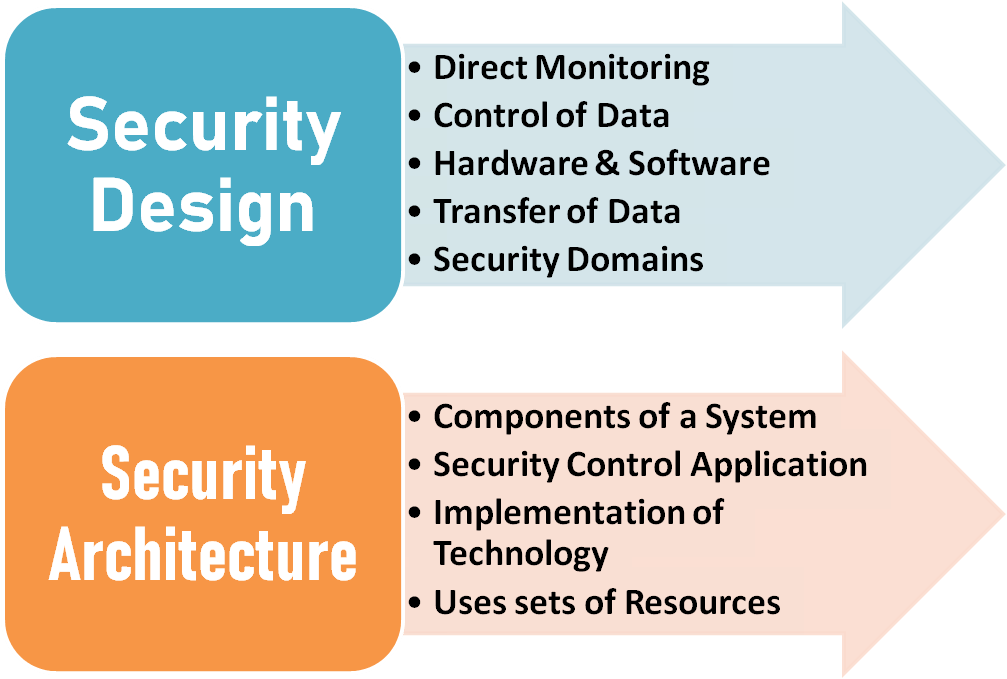
What Is The Difference Between A Degree In Security Architecture And Security Design

Security Architecture Cloudec V600r019c00 Solution Description Enterprise On Premises Huawei

The Five Essential Capabilities Of An Analytics Driven Soc Adopt An Adaptive Security Architecture Splunk
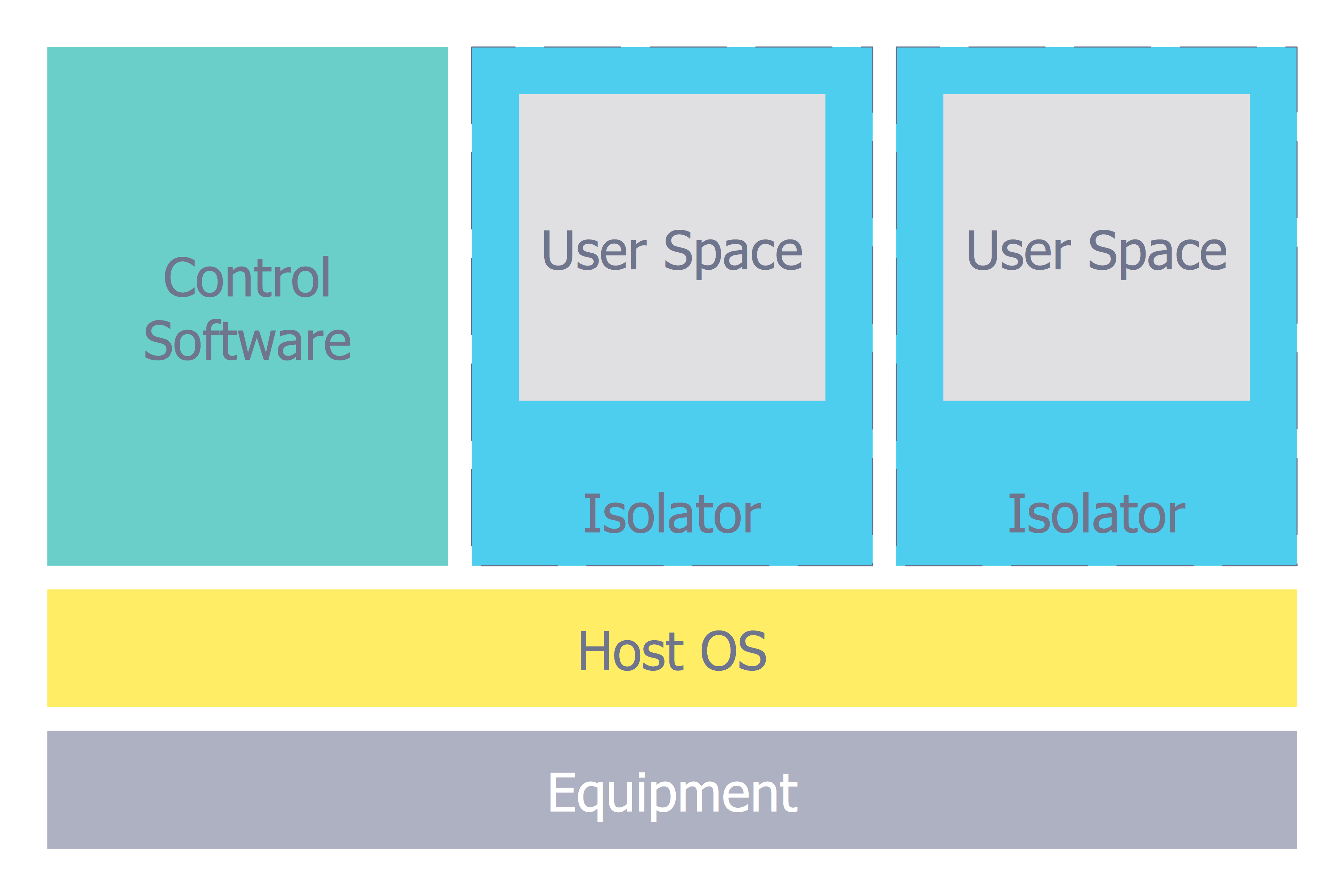
Network Security Architecture Diagram

Building A Secure Architecture With Cisco Safe Cisco Blogs

Enterprise Architecture Cloud Security Alliance

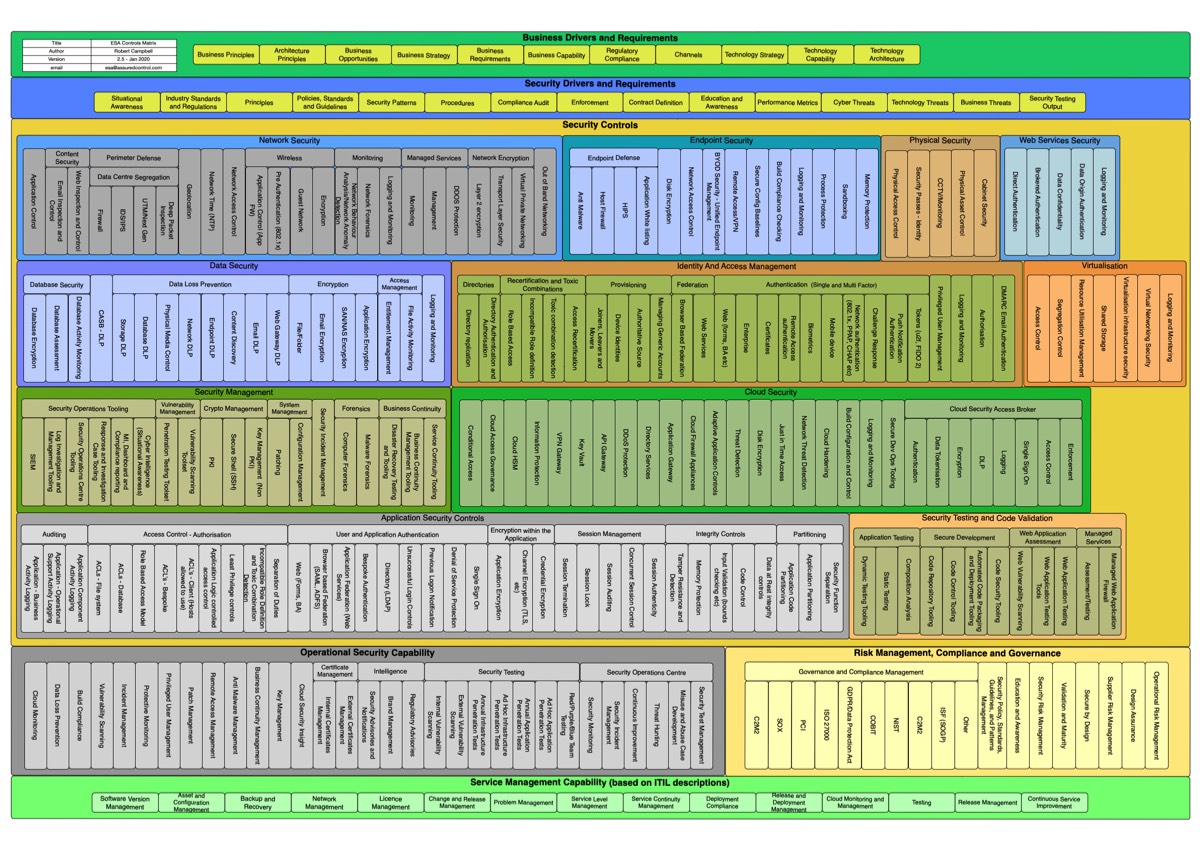
Open Enterprise Security Architecture O Esa A Framework And Template For Policy Driven Security Wahe Stefan Petersen Gunnar Van Haren Publishing Amazon Sg Books
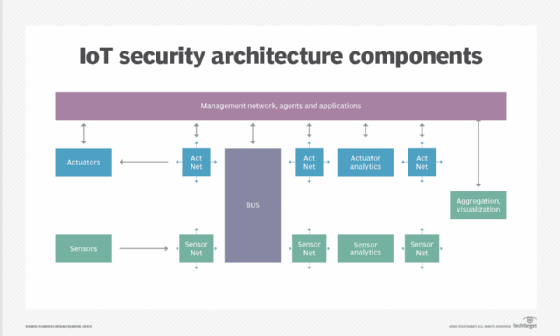
Use An Iot Security Architecture To Protect Networks End To End
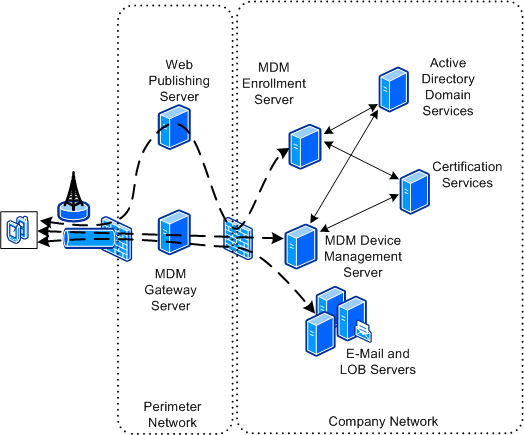
Mdm Security Architecture

Security Architecture Review Of A Cloud Native Environment
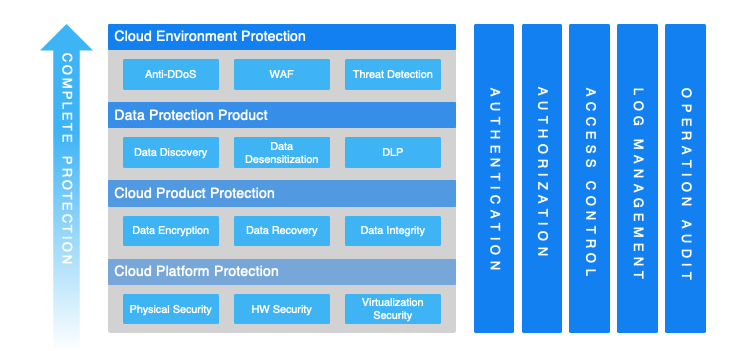
Is Your Data Secure In The Cloud An Overview Of Alibaba Cloud S Data Security Architecture Alibaba Cloud Community

Security Architecture Fusionaccess Desktop Solution 6 5 1 Security Description 06 Huawei

Simplifying Security Architectures With Safe Cisco Blogs

Open Enterprise Security Architecture O Esa A Framework And Template For Policy Driven Security

Build Adaptive Security Architecture Into Your Organization Smarter With Gartner
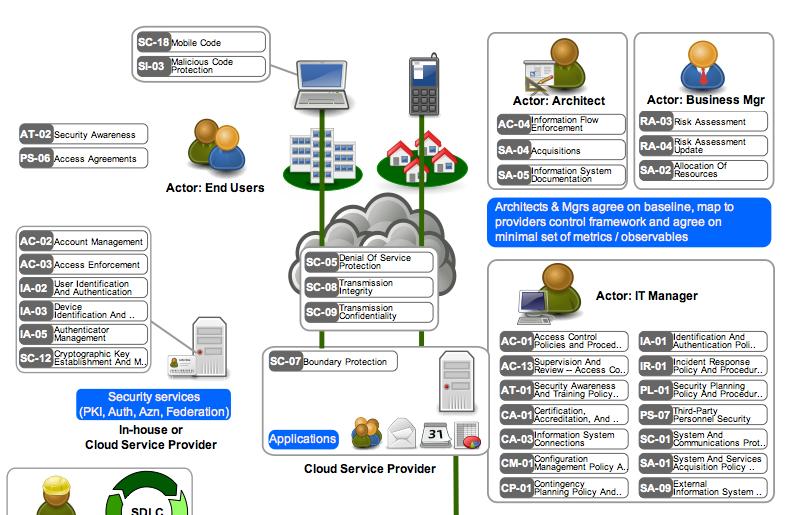
Introduction To Cloud Security Architecture From A Cloud Consumer S Perspective
Q Tbn And9gctn Ss0oizj5ljin3uwnn9q3bilzaokubrct2zuffsr8fcguex2 Usqp Cau



