Security Audit
Perform a physical audit Not all attacks start out using cyber tacticsensuring that the physical plant is secure, and people are trained to maintain physical security are as important as.

Security audit. Every organization should perform routine security audits to ensure that data and assets are protected First, the audit’s scope should be decided and include all company assets related to information security, including computer equipment, phones, network, email, data and any accessrelated items, such as cards, tokens and passwords. Help enforce security regulations and practices – audits allow you to make sure that all cyber security measures put in place in your company are thoroughly enforced and followed Determine the real state of your security and formulate the strategy for the future – audit will show you how things really are in a much more detailed way than risk assessment ever could. A security audit is a structured approach to assessing the security measures that a company has in place, using a set of defined criteria Typically, the criteria will be a security framework such as ISO , NIST Cyber Security Framework, Cyber Essentials or a technology specific standard such as EIDAS (ETSI EN 319 411).
An outside firm can perform the audit, establish compliance guidelines and help to create security documentation or simply validate that you did your risk assessment correctly and haven't missed. A detailed IT security audit consists of several independent assessments of various IT aspects The auditor would first access the external vulnerabilities of the IT infrastructure to assess how quickly an attacker can break into your defenses This aspect of auditing usually involves indepth system scans along with whitehat hacking. Perform a physical audit Not all attacks start out using cyber tacticsensuring that the physical plant is secure, and people are trained to maintain physical security are as important as.
A network security audit is a technical evaluation of a company’s network The audit checks policies, applications, and operating systems for security faults and risks Network auditing is a systematic process during which an IT specialist analyzes five aspects of a network. 184 IT Audit jobs available in Dallas, TX on Indeedcom Apply to IT Auditor, Senior IT Auditor, Internal Auditor and more!. A cyber security audit checklist is a valuable tool for when you want to start investigating and evaluating your business’s current position on cyber security It can be difficult to know where to begin, but Stanfield IT have you covered.
Set a security audit schedule, and establish criteria (such as “a change in location, a new threat, suspicion of loss or actual loss”) for unscheduled audits “Performing a security audit on a regular basis will help your organization minimize loss and increase the safety of employees and customers. The workplace security audit includes the verification of multiple systems and procedures – including the physical access control system – used for a comprehensive workplace security A checklist should cover all major categories of the security audit. A security audit is the highlevel description of the many ways organizations can test and assess their overall security posture, including cybersecurity You might employ more than one type of security audit to achieve your desired results and meet your business objectives.
A basic audit policy specifies categories of securityrelated events that you want to audit When this version of Windows is first installed, all auditing categories are disabled By enabling various auditing event categories, you can implement an auditing policy that suits the security needs of your organization. Managed Security Service Provider (MSSP) in Texas, USA Security is the most concerning factor for any industry today!. Free Security Audits for Your Home or Workplace in Dallas Give us a call (214) Increase the security of your home or business by having a top locksmith company, Dallas FW Locksmith, conduct security audits for youEvery possible point of entry is looked at to ensure that your property is secure We provide service to Dallas and Fort Worth, TX and surrounding communities.
A cyber security audit framework addresses how well your company identifies, detects, protects, responds and recovers from breaches and other incidents Specifically, you are expected to document compliance in the following areas Risk management, including hardware, software, assets and system interconnections Risk level must be communicated. WLAN Security Audit CTAdvanced Wireless Technology WLAN Security Auditing Tools • The hardware and software used during an audit varies based on the type of WLAN vulnerability to be identified • The tools selected must match the job at hand – For example, if an auditor is looking for the source of noise that is causing a potential denial of service, the proper tool is a spectrum. Audit Security State Change;.
A security audit is a systematic monitoring of the security of a company's information system by measuring how well it conforms to a set of established criteria Windows security auditing is a Windows feature that helps to maintain the security on the computer and in corporate networks Windows auditing is intended to monitor user activity. A network security audit is a technical assessment of an organization’s IT infrastructure—their operating systems, applications, and more But before we dig into the varying types of audits, let’s first discuss who can conduct an audit in the first place. A security audit is the inspection of the security management system of a certain organization or institution The checklist for the security audit provides an easier way to conduct the audit This checklist displays a list of all the items that are required to be done for the security audit.
Audit Security System Extension. Ultimately, security audits help ensure that your company is protected and that sensitive information is stored and handled appropriately In this blog, we’ll cover four types of security audits you should perform regularly to safeguard your business, employees and customers 4 Types Of Security Assessments Every Business Should Conduct. Audit Report Office Affiliation The Office of Audit Our objective was to determine the appropriateness of payments the Social Security Administration (SSA) issued to beneficiaries and representative payees who were deceased according to Texas Department of State Health Services vital records We also identified nonbeneficiaries who were.
A website security audit is a great way to stay at the top of your website’s security status and ensure that you put in your best efforts, and minimize infiltration threats The best part is that there are a lot of free scanning tools you can find online, empowering website owners the ability to perform audits autonomously with little help from third parties. Audit Other System Events;. Before prime time Scheduled/maintenance Audit Schedules Individual Host 1224 months Large Networks 1224 months Network 12 months Firewall 6 months How to do a Security Audit Preaudit verify your tools and environment Audit/review security policy Gather audit information Generate an audit report Take actions based on the report's findings.
Network Security Audit Checklist Conduct an audit on an internal level or hire a thirdparty to assess the state of the system’s security If you opt for inhouse testing, the network security audit checklist below will help you get started. The Security Audit Questionnaire was designed primarily to help evaluate the security capabilities of cloud providers and third parties offering electronic discovery or managed services The tool is also useful as a selfchecklist for organizations testing the security capabilities of their own inhouse systems. Perform a physical audit Not all attacks start out using cyber tacticsensuring that the physical plant is secure, and people are trained to maintain physical security are as important as.
Access OIG’s comprehensive archive of audit reports and investigations that have been conducted from 1996 to present You may view the audits and investigations in PDF or text format. Security audits have become a common feature of almost every industry in today’s datadriven world While the prospect of being audited usually doesn’t make anyone in an organization jump for joy, security audits play a vital role in protecting both organizations and their customers from data breaches and mismanagement While many compliance standards require companies to renew their. A security audit will locate viruses, malware or data breaches and help you decide on the best course of action for your business in the event of an active threat Lack of regulation or policy compliance Today, many businesses are bound by government regulations that define what security measures need to be taken to protect data.
From the US Attorney's Office, Northern District of Texas DALLAS — Four members of an Arlington, Texas, family were arrested earlier this week on charges outlined in a federal criminal complaint, unsealed late yesterday, stemming from their alleged conspiracy to defraud the Social Security Administration (SSA) by feigning mental illnesses to fraudulently collect Social Security benefits. 162 IT Audit jobs available in DallasFort Worth, TX on Indeedcom Apply to IT Auditor, Information Security Analyst, Senior IT Auditor and more!. Most will be overall risk management, security and financial audits Seek out the controls stressed by the agency that will be assessing compliance of your cybersecurity program If you’re in the process of getting a contract, look to the agency and its website to find information security policies and requirements.
The most timeconsuming aspect of an IT security audit is creating the audit trail An audit trail consists of the documentation provided to the auditor that shows proof of processes to secure an IT environment When preparing for an IT security audit, companies need to start by organizing the documents that meet audit requirements The documentation needs to prove business and industry knowledge. Audit logs enable your security team to reconstruct events after a problem occurs The documentation provides your security administrator with the information needed to recover rapidly from an intrusion Forensics Evidence If a data breach leads to a lawsuit, your audit log can be evidence to show appropriate event management Threat Detection. Cyber Security Solutions Penetration Testing Experts Security Audit Systems provide penetration testing services using the latest 'real world' attack techniques, giving our clients the most indepth and accurate information to help mitigate potential threats to their online assets.
Performing regular security audits is a best practice that every business should follow Every location is vulnerable to threats, be they physical theft, information theft, life safety risks to employees and patrons, and/or acts of God. A security audit is a systematic evaluation of the security of a company's information system by measuring how well it conforms to a set of established criteria A thorough audit typically assesses the security of the system's physical configuration and environment, software, information handling processes, and user practices. IT security audit tools automate the IT security audit process, making it more efficient and effective Here are 11 musthave IT security audit tools.
System security policy settings and audit events allow you to track systemlevel changes to a computer that are not included in other categories and that have potential security implications This category includes the following subcategories Audit IPsec Driver;. Security Audit Systems provide penetration testing services using the latest 'real world' attack techniques, giving our clients the most indepth and accurate information to help mitigate potential threats to their online assets. Logsecurity MicrosoftWindowsSecurityAuditing Kernel Driver Signing Why – Kernel driver signing improves defenses against injection of malicious drivers and activity in the Windows kernel The detection of a signed driver being tampered with, indicates malicious activity in most scenarios and requires immediate investigation.
Security audit in this regard is perceived as even more challenging, but it is a rather common myth To understand the necessity of security audit and explain its cost, let’s focus on the essence of this procedure It can be characterized as a general and full analysis and assessment of a site’s security state. The network security audit is a process that many managed security service providers (MSSPs) offer to their customers In this process, the MSSP investigates the customer’s cybersecurity policies and the assets on the network to identify any deficiencies that put the customer at risk of a security breach. A security audit is the inspection of the security management system of a certain organization or institution The checklist for the security audit provides an easier way to conduct the audit This checklist displays a list of all the items that are required to be done for the security audit.
An Information security audit is a systematic, measurable technical assessment of how the organization’s security policy is employed It is part of the ongoing process of defining and maintaining effective security policies Security audits provide a fair and measurable way to examine how secure a site really is. Perform a physical audit Not all attacks start out using cyber tacticsensuring that the physical plant is secure, and people are trained to maintain physical security are as important as. A security audit assesses how effectively your organization’s security policies are being implemented Our audits will show you where gaps and vulnerabilities might exist in your current systems and procedures With over 45 years of experience, we have seen countless reasons for noncompliance with existing security procedures.
Expanding computing solutions and evolving technology developments have simplified many critical and intensive tasks.

Cyber Security Audit Process Visual Ly

It Security Audit Checklist Empower It Solutions
Q Tbn And9gct Lk Xsez4wco4n Ejdxurojcgkglndjoesuyhwcmkstkhnod Usqp Cau
Security Audit のギャラリー

Conducting Network Security Audits In A Few Simple Steps Portnox Com

How To Do A Security Audit An 11 Step Checklist Useful Tools Medium

Safety Security Audit Optimus Trading Solutions
1

Beam Security Audits Results As A Privacy Focused Company We By Beam Privacy Beam Mw Medium

It Security Audit Services Why Businesses Need To Perform Cyber Security Audit Frequently And Who Should Perform It

Security Audit Security Assessment Huntsman Security

Security Audit Security Assessment Huntsman Security

Website Security Audit Top 25 Apac Cyber Security Providers

Free Api Security Tools Swagger Security Audit
Cyber Security Audit Home Office Base

What Is An It Security Audit The Basics Varonis

It Security Audit Iver Solutions

Smart Contract Security Audit Octofi

Leading Cyber Security Consulting Assessment And Audit Service Companies Singapore

4 Easy Steps How To Conduct It Security Audit Of Your Own Company

Security Audit Header Hostpapa Blog

Openzeppelin Security Audits

How To Do A Wordpress Security Audit 8 Easy Steps Malcare

Information Security Audit And Self Assessment Frameworks For Operators Of Essential Services And Digital Service Providers Enisa

What Not To Say During A Security Audit Of Your Startup Securicy

How It Security Audit Benefits Your Business Process

Could You Pass A Security Audit Take Our Security Audit Readiness Assessment To Find Out Digital Guardian

Internal Pentest What Is This Type Of Security Audit

Corporate Auditor Is Touching The Term Security Audit On A Transparent Stock Photo Picture And Royalty Free Image Image

Pdf It Security Audit
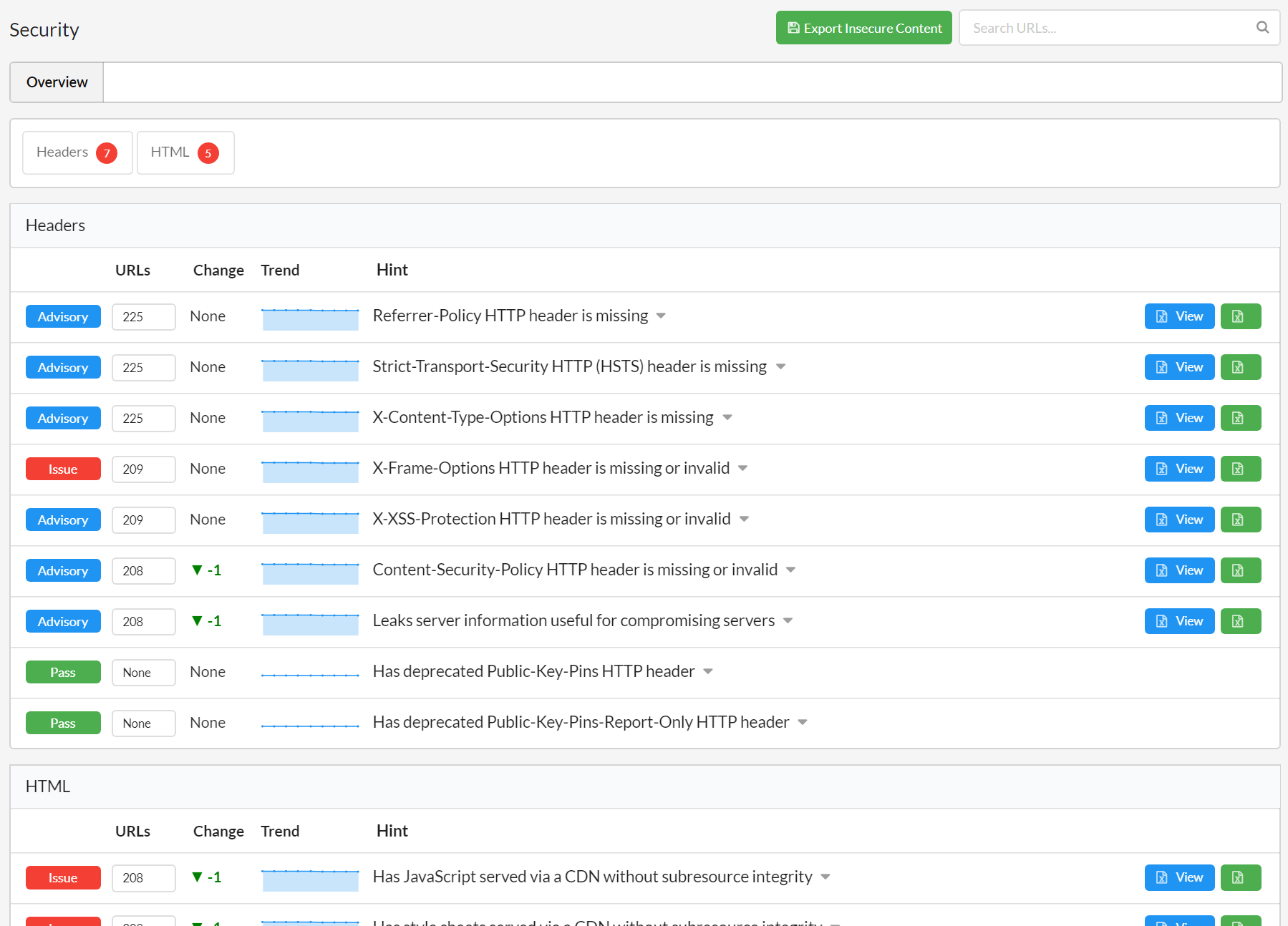
Perform A Website Security Audit With Sitebulb

7 Major Issues A Physical Security Audit Can Uncover

What Is The Difference Between Vulnerability Scanning And Security Aud

How To Run A Business Security Audit

Cyber Security Audit

Halborn Announces Reef Finance Security Audit By Reef Dec Medium

Kubernetes Open Sourced Their Security Audit What Can We Learn Snyk

Search Security Audit Service

How To Run A Business Security Audit

How To Do A Security Audit An 11 Step Checklist Useful Tools Medium

How Do Security Audits And Surveys Help In A Foolproof Security Plan Home Security Tips

Sitlearn Individual Course

Information Technology Security Audit Guidebook Nist Sp 800 171 Russo Cissp Issap Ciso Mark A Amazon Sg Books

Performing A Technical Security Audit And Assessment

It Security Audit Ti3 Intelligence

Application Security Audit Checklist Template Process Street
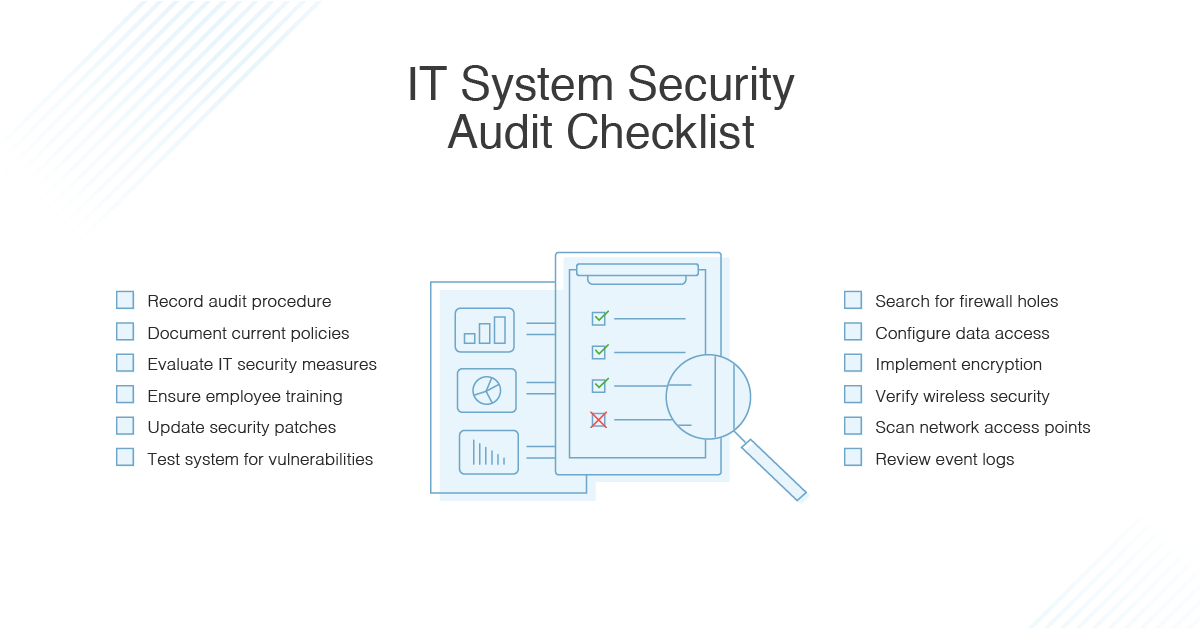
It Security Audit Standards Best Practices And Tools Dnsstuff

Beosin Has Completed The Security Audit Service Of Dego Of Defi Project By Beosin Chengdu Lianan Tech Medium

Website Security Auditing Testing Security Audit Systems

What Is An It Security Audit The Basics Varonis

Five Ways To Prepare For A Security Audit Riskwatch

Nordvpn Completes App Security Audit Nordvpn

What Is An It Security Audit Business Partner Magazine

What Is An It Security Audit Techwalls

What Does A Vpn Security Audit Really Prove

What Is A Security Audit The Best Times To Run One

Bluekrypt Security Audit

Huawei 5g Aces Gsma Nesas Security Audit The Impact Tech Arp

Enterprise It Security Audit Cyber Security Services
3

Openzeppelin Security Audits

What Is An It Security Audit The Basics Varonis

Beosin Has Completed The Security Audit Service Of Dego Of Defi Project By Beosin Chengdu Lianan Tech Medium

The Ultimate Network Security Audit Checklist

Infinito Wallet S Security Audit By World Leading Security Auditor Smartdec Our Commitment To Transparency Infinito Wallet

Cybersecurity Audit Masterclass Live Online 21

Network Security Audit How To Perform An Audit Checklist

What Is An It Security Audit The Basics Varonis

Is Penetration Testing Sufficient For A Security Audit

How To Effectively Conduct A Cyber Security Audit

How To Conduct A Small Business Security Audit Startupnation

Does Your Company Need An It Security Audit Network Security

How To Perform A Security Audit On Your Website Hostpapa Blog

The Simple Way To Reduce Your It Security Audit Findings Avatier

11 It Security Audit Tools You Can T Afford To Skip 11 Security Audit Essentials

Will You Survive Your Next Security Audit

Network Security Audit How To Perform An Audit Checklist

Roles And Responsibilities Of Information Security Auditor Infosec Resources

It Security Audit Best Practice To Perform Security Inspection Clickssl

Website Security Audit 7 Steps To A More Secure Wordpress Website
Q Tbn And9gcreeuaydxkwpprw8x3rvl2v86lghethp5klvkoy Sgjtztzgqza Usqp Cau
What Is A Network Security Audit Anderson Technologies

Prepare For An Ibm I Security Audit Helpsystems

Cyber Security Audit Services
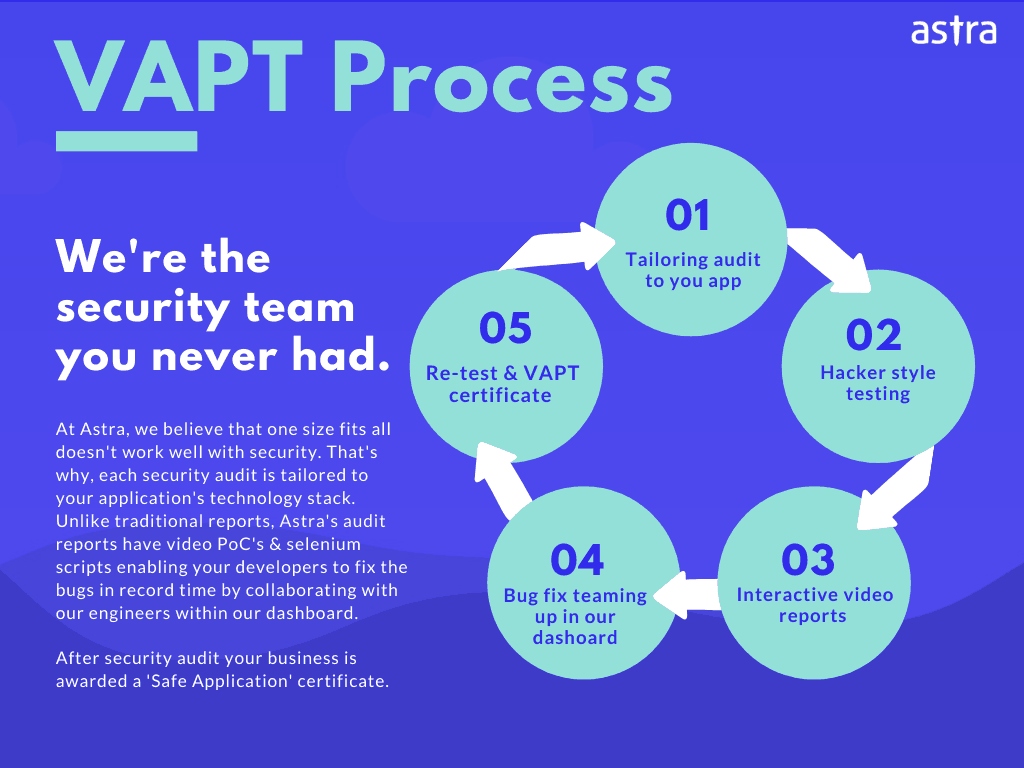
It Security Audit Types Importance And Methodology

Learn How To Become A Security Auditor Cyber Security Education

Automate Your Next Security Audit Tugboat Logic

Network Security Audit Checklist Reciprocity

Sap Security Audit Logs Which Event Types Should I Enable There Are 90 Of Them And How Much Disk Space Do I Need Sap Blogs

Cyber Security Audit Ashtree

6 Questions To Ask Before Conducting An Internal Security Audit 1password

Network And Server Security Audit Vulnerability Risk Assessment

What Is Cyber Security Audit And How It Is Helpful For Your Business Indusface Blog
It Security Audit Types Importance And Methodology

How To Perform A Wordpress Security Audit Nerdynaut
Application Security Audit Softscheck

Tips For Conducting A Personal Online Security Audit To Protect Yourself From Threats This Year Security Today

How To Perform A Wordpress Security Audit

Ahho6fryuapbcm

Security Audit Patronus Laboratories

It Security Consulting It Security Audit Compliance Risk Assessment

Security Audit Romano Security Consulting

Security Audit For Dummies Jscrambler Blog

Process Street

Wp Security Audit Log A Plugin For All Your Wordpress Activity Trail Wedevs



