Privileged Account Management
Privileged Account Management for Dummies is written for IT and systems administrators, along with security professionals responsible for protecting your organization from security threats It assumes a basic level of IT expertise and experience, but is also great for educating business users and others on the importance of privileged account.

Privileged account management. Maintain an uptodate inventory of all privileged accounts Be sure to inventory accounts from critical Active Do not allow admins to share accounts Make administrators accountable for their actions by personalizing their Minimize the number of personal privileged accounts Ideally, each. Audit domain and local accounts as well as their permission levels routinely to look for situations that could allow an adversary to gain wide access by obtaining credentials of a privileged account 11 12 These audits should also include if default accounts have been enabled, or if new local accounts are created that have not be authorized. Examples of nonhuman privileged access Application account A privileged account that’s specific to the application software and is typically used to administer, configure or manage access to the application software Service account An account that an application or service uses to interact with the operating system Services use these.
Privileged Account Manager (PAM, Privileged User Manager) support resources, which may include documentation, knowledge base, community links,. The term "privileged account" includes the most powerful accounts spread across an. BENEFITS OF PRIVILEGED ACCount MANAGEMENT ADVISORY Actionable insights based on the outcome of an analysis of the state of your environment and distribution of privileged accounts and their permissions;.
Values and stored in the privileged account management system The focus of this Privileged Password Security Policy document is on the second type of password, Privileged Account Passwords However, because User Account passwords often have elevated or administrative privileges attached to them, both types of passwords are. Privileged user accounts are those to which rights to perform system and/or application administration have been assigned This policy defines the requirements surrounding the creation, use, monitoring, and decommissioning of privileged user accounts within the Franklin & Marshall data network. Privileged account management (PAM) is emerging as one of the hottest topics in cybersecurity — and it’s easy to understand why Cybercriminals are relentless when it comes to finding and.
Realistic assessment of the state of your organization’s privileged access capabilities and identification of both high risk accounts and low hanging fruit for risk mitigation. By combining the power of privileged account management (PAM) with identity governance, you’ll close security gaps, reduce risk and eliminate redundant processes for privileged and nonprivileged accounts Now you can streamlineIT using automated provisioning and deprovisioning, along with faster reporting and auditing for all your users. Managing privileged access reduces your risks of a cyberattack But to do so effectively, you need to follow privileged access management best practices.
BENEFITS OF PRIVILEGED ACCount MANAGEMENT ADVISORY Actionable insights based on the outcome of an analysis of the state of your environment and distribution of privileged accounts and their permissions;. The NCCoE recently released a draft of the NIST Special Publication (SP) Privileged Account Management for the Financial Services Sector The project's public comment period closed on November 30, 18 For ease of use, the guide is available to download or read in volumes SP A Executive Summary. Privileged account management (PAM) is a domain within identity and access management (IdAM) that focuses on monitoring and controlling the use of privileged accounts Privileged accounts include local and domain administrative accounts, emergency accounts, application management, and service accounts.
The Password Server itself is a fullfeatured shared account and password management solution It can be used in combination with Remote Desktop Manager for privileged account and session management tools integrating over 150 integrations and technologies Download this Directory and get our Free Privileged Access Management Buyer’s Guide. Securing privileged access has never been an easy task for organizations With several high profile breaches linked to breach of privileged credentials, security teams are now increasingly aware of the high risk associated with these privileged accounts The recent SolarWinds attack only further validates the need to secure these privileged accounts Once the defense of. Privileged Account Management solutions have a specific focus on securing privileged credentials Because of this you will see a clear difference in their functionality compared to your typical identity management solution used for personal accounts.
In this article Privileged access management allows granular access control over privileged admin tasks in Office 365 It can help protect your organization from breaches that use existing privileged admin accounts with standing access to sensitive data or access to critical configuration settings. Privileged password management systems can periodically audit password records, monitor for account login sessions, trigger alerts, write to logs, and shut down suspicious activity effortlessly. Privileged account management can be defined as managing and auditing account and data access by privileged users A privileged user is someone who has administrative access to critical systems For instance, anyone who can set up and delete user accounts and roles on your Oracle database is a privileged user.
CyberArk PAS is one of the leading solutions in the Privileged Account Management (PAM) space, which is what WWT considers one of the five pillars of Identity and Access Management The environment includes several Windows and Linux endpoints to demonstrate CyberArk’s Privileged Session Manager functionality This lab guide provides an overview of the CyberArk PAS solution and provides a brief walkthrough of some of the primary use cases within CyberArk PAS. Privileged account management (PAM) is a part of identity and access management (IAM) that deals exclusively with the protection of privileged accounts in an enterprise, including those of operating systems, databases, servers, applications, virtual machines, and networking devices What is a privileged account?. Privileged access management (PAM) technologies are designed to simplify the access management for privileged accounts to ensure that only designated users are able to access the company’s most sensitive data.
Privileged Account Management managing and auditing account and data access by privileged users Privileged user someone who has administrative access to critical systems or to a vast amount of confidential data with edit privileges. Privileged access management (PAM) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for users, accounts, processes, and systems across an IT environment By dialing in the appropriate level of privileged access controls, PAM helps organizations condense their organization’s attack surface, and prevent, or at least mitigate, the damage arising from external attacks as well as from insider malfeasance. Privileged Account Management (PAM) 12/02/ Contributors Download PDF of this page Privileged Account Management (PAM) This feature provides a specific, auditable record of granular administrative permission sets granted to VDS and/or Active Directory privileged accounts External access automatically expires by default.
Privileged Access Management, also known as PAM, is a critical security control that enables organizations to simplify how they define, monitor, and manage privileged access across their IT systems, applications, and infrastructure Because administrator accounts have elevated privileges that can. Values and stored in the privileged account management system The focus of this Privileged Password Security Policy document is on the second type of password, Privileged Account Passwords However, because User Account passwords often have elevated or administrative privileges attached to them, both types of passwords are. As confusing as it may sound, privileged user management is all about accounts and not particular people Privileged user management is the process of managing privileged accounts with permanent access to critical assets PUM is responsible for managing builtin admin accounts, such as root and system administrator accounts.
Privileged Account Management (also known as ‘Privileged Access Management’) is pivotal to controlling access It delivers the required balance between system administrators and users Allowing users to be 100% productive and an organisation controlling access to its most valuable asset. CyberArk PAS is one of the leading solutions in the Privileged Account Management (PAM) space, which is what WWT considers one of the five pillars of Identity and Access Management The environment includes several Windows and Linux endpoints to demonstrate CyberArk’s Privileged Session Manager functionality. Privileged Account Management (PAM) is a domain within Identity and Access Management (IdAM) focusing on monitoring and controlling the use of privileged accounts Privileged accounts include local and domain administrative accounts, emergency accounts, application management, and service accounts.
Privileged account management platforms can help you mitigate the risks associated with elevated access These products can help close out audit findings, assist in meeting compliance mandates, and increasingly enable an organization to pass its SAS 70 reviews. Privileged account management (PAM) is a domain within identity and access management (IdAM) that focuses on monitoring and controlling the use of privileged accounts Privileged accounts include local and domain administrative accounts, emergency accounts, application management, and service accounts. For each role, an account with the minimum necessary privileges is created This account is given strong credentials in terms of passwords or keys The PAM solution then maps Identities to Roles, while auditing access on the way through This delivers the following advantages The attack surface is kept to the absolute minimum Enterprise Class Credential Lifecycle Management within the Privileged Access Management solution keeps all the credentials long, strong and regularly changed.
ARCON Privileged Access Management (PAM) is the bestinclass PAM solution that offers an array of features that not only mitigates data breach threats but also predicts risks arising from suspicious users in the network Request A Demo Download Brochure. In fact, Thycotic notes 70% of enterprises fail to discover all of the privileged accounts on their network Meanwhile, 40% never make an attempt to look for all of their superuser accounts For 19, You Need Privileged Access Management In this context, a distressing pattern also emerges enterprises struggle with enforcing their PAM. Privileged Access Management (PAM) refers to systems that securely manage the accounts of users who have elevated permissions to critical, corporate resources These may be human administrators, devices, applications, and other types of users.
Privileged Account Management (PAM) refers to the process of maintaining and safeguarding the accounts within a system that have special access to sensitive data Privileged users can take a variety of forms, from trusted highsecurity company managers to IT contractors with the ability to access necessary data. Day after day, we see the evidence of an increased number of breaches As a Privileged Account Management (PAM) provider, we are also seeing a similar increase in requests for proposals on our Core Privileged Access Manager (BoKS) solution What is most interesting is that a large number of security professionals who contact us indicate that they are not not even sure what privileged accounts. For holistic management of privileged accounts and credentials, execute across these eight core strategies 1 Discover all privileged credentials, such as shared admin, user, application, and service accounts, SSH keys, 2 Bring privileged accounts and credentials under centralized management.
Securing privileged access has never been an easy task for organizations With several high profile breaches linked to breach of privileged credentials, security teams are now increasingly aware of the high risk associated with these privileged accounts The recent SolarWinds attack only further validates the need to secure these privileged accounts Once the defense of. Privileged Account Management Best Practices There are many types of accounts within systems and some accounts have more privileges or power to access and execute highly sensitive data and transactions than standard accounts The majority of accounts fall within what is considered to be “normal” or “user” Although user account credentials can be stolen to access systems, it is not likely these accounts will present a great threat to the organization. By combining the power of privileged account management (PAM) with identity governance, you’ll close security gaps, reduce risk and eliminate redundant processes for privileged and nonprivileged accounts Now you can streamlineIT using automated provisioning and deprovisioning, along with faster reporting and auditing for all your users.
Complex organizations, including financial services companies, face challenges managing privileged accounts, which opens a significant risk to their business If used improperly, these accounts can cause significant operational damage including data theft, espionage, sabotage, ransom, or bypassing important controls. By combining the power of privileged account management (PAM) with identity governance, you’ll close security gaps, reduce risk and eliminate redundant processes for privileged and nonprivileged accounts Now you can streamlineIT using automated provisioning and deprovisioning, along with faster reporting and auditing for all your users. Realistic assessment of the state of your organization’s privileged access capabilities and identification of both high risk accounts and low hanging fruit for risk mitigation.
Privileged Account Manager (PAM, Privileged User Manager) support resources, which may include documentation, knowledge base, community links,. Securing privileged access has never been an easy task for organizations With several high profile breaches linked to breach of privileged credentials, security teams are now increasingly aware of the high risk associated with these privileged accounts The recent SolarWinds attack only further validates the need to secure these privileged accounts Once the defense of. Privileged account management (PAM) has emerged to be one of the hottest topics of the cybersecurity industry, all because of the everlasting impacts that a simple mistake could lead to Cybercriminals are always on their toes when it comes to intercepting the connections, stealing the target’s privileged credentials, and compromising the data.
Securing privileged access has never been an easy task for organizations With several high profile breaches linked to breach of privileged credentials, security teams are now increasingly aware of the high risk associated with these privileged accounts The recent SolarWinds attack only further validates the need to secure these privileged accounts Once the defense of. Privileged Account Management With Xton Access Manager, we ensure all access (passwords, keys, certificates, documents and more) to privileged accounts are kept safe, secure and out of the reach of threats, both internal and external. For information on how to protect privileged accounts, please read the rest of our brief guide, which also highlights best practices “The Three Phases of Securing Privileged Accounts” You can also find guidance on how to prioritize your approach for effective, riskbased privileged access management.
An appropriate level of privileged account control and management plays a significant role in ensuring your organization’s cybersecurity Verizon reports that in 17, privilege misuse was behind 12% of all security breaches And according to Gartner, by , the lack of Privileged Account Management (PAM) processes will be the cause of more than half of all security failures associated. Defining PAM Privileged Account Management We call privileged accounts those accounts that have the most power inside an IT department and are used by the team to set up the IT infrastructure, to install new software or hardware, to run critical services or to conduct maintenance operations. The Password Server itself is a fullfeatured shared account and password management solution It can be used in combination with Remote Desktop Manager for privileged account and session management tools integrating over 150 integrations and technologies Download this Directory and get our Free Privileged Access Management Buyer’s Guide.
Privileged Session Management Control, monitor and record privileged sessions of administrators, remote vendors and other highrisk users Sessions recordings are indexed to simplify and accelerate searching for events Automated reports enable you to easily meet your auditing and compliance requirements. Maintain a complete list of all active privileged accounts in your network, and update that list whenever a new account Store privileged identities like passwords, SSH keys, and SSL certificates in a secure vault using standardized Enforce stringent IT policies that cover password complexity,.

Implementing Privileged Access Management Pam The Pam Lifecycle
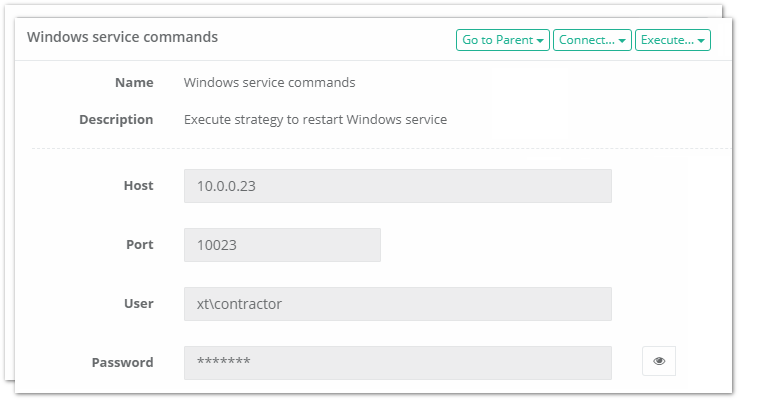
Privileged Access Management Pam Solutions Xton Technologies
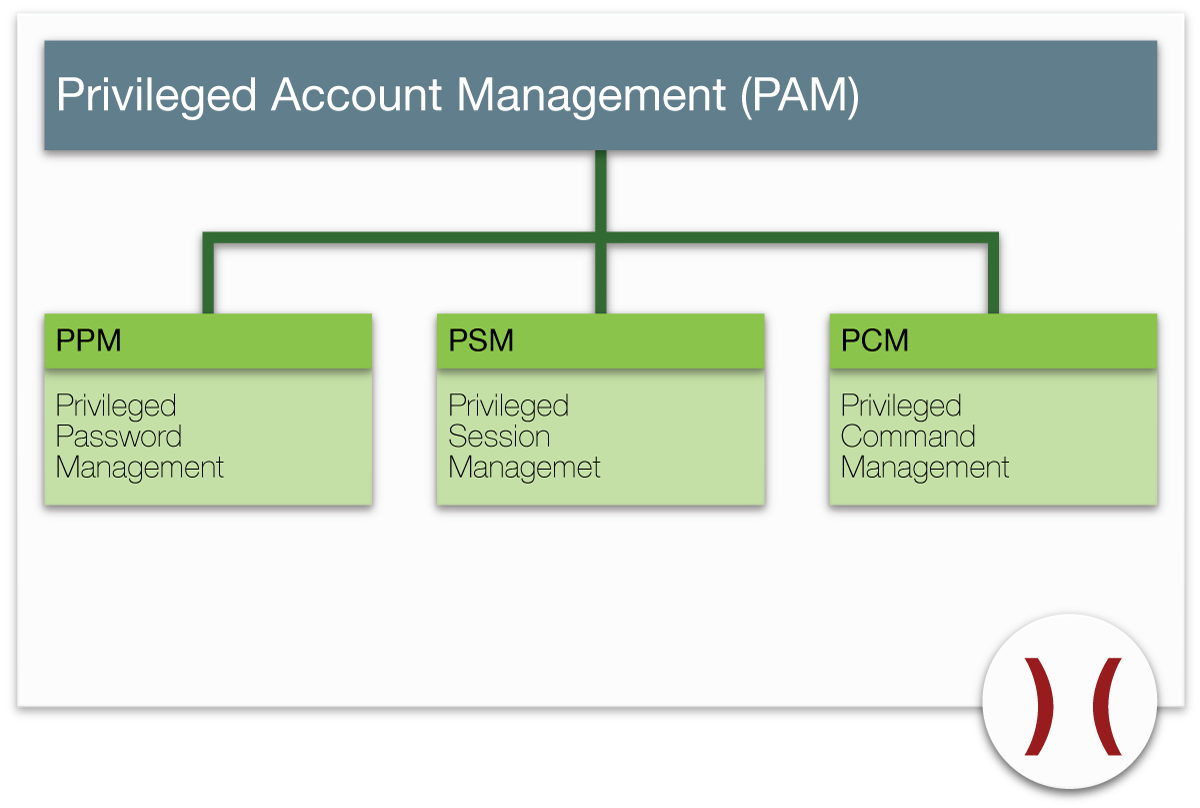
Some Thoughts About Privileged Identity Management And Privileged Account Management
Privileged Account Management のギャラリー

Can Privileged Account Management Really Stop Credential Theft Javelin Networks Blog

What Is Privileged Access Management Pam Explained Security Wiki

Privileged People And Powerful Systems Balancing Trust With Thycotic Techhq

Lessons Learned While Implementing Azure Ad Privileged Identity Management Pim Modern Workplace Blog

The Security Sector To Watch Privileged Account Management By Jeffrey Feng Medium
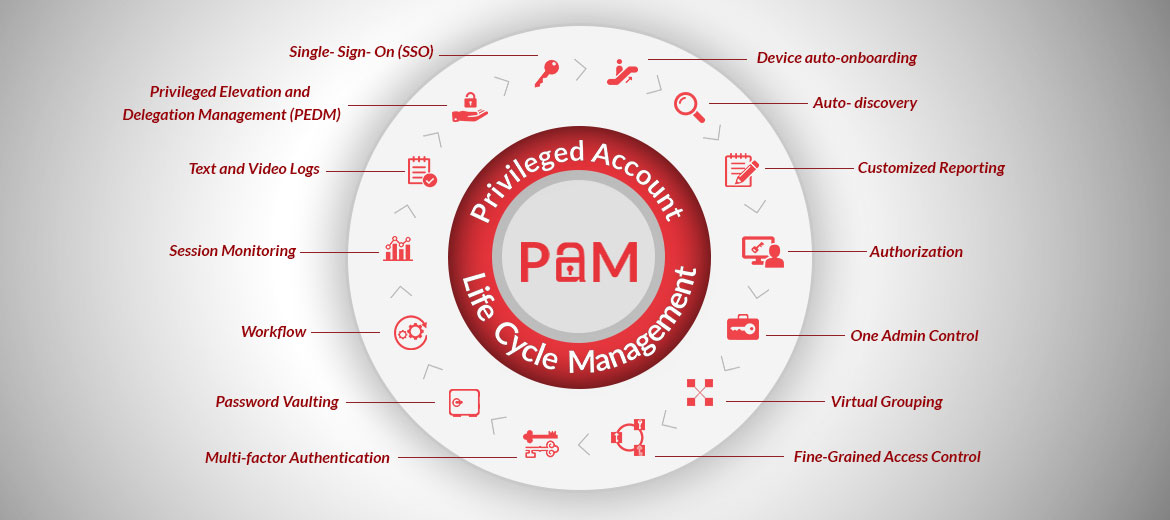
Privileged Access Management Solutions Overview
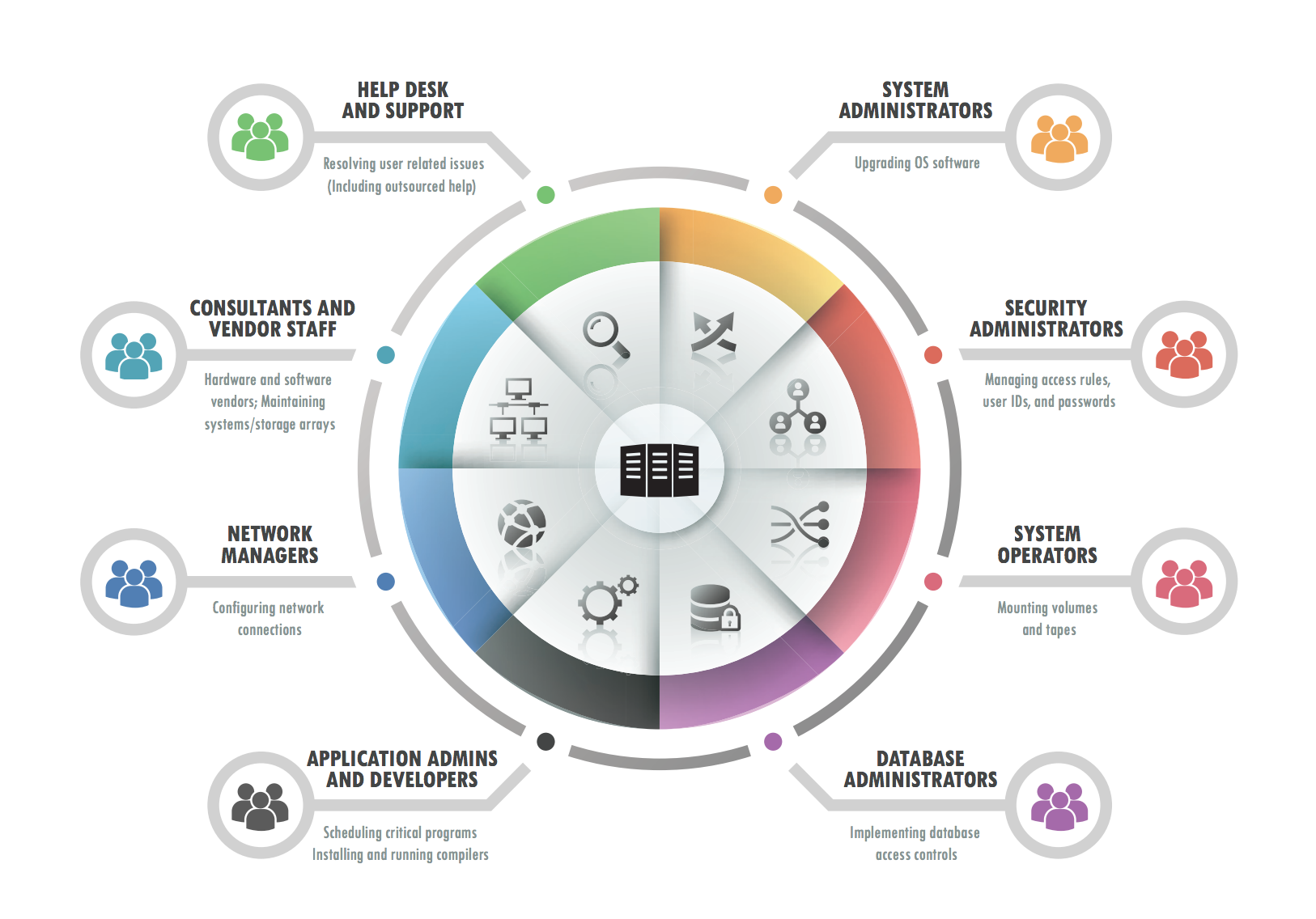
What Is Privileged Access Management Core Security

Nist 800 53 Privileged Access Management Security Privacy

Integrating Privileged Account Management Into Devops Devsecops
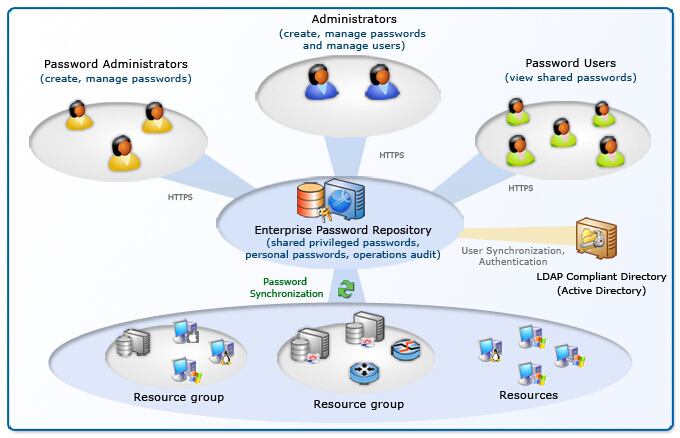
Privileged Password Management Solution Privileged User Account Manager
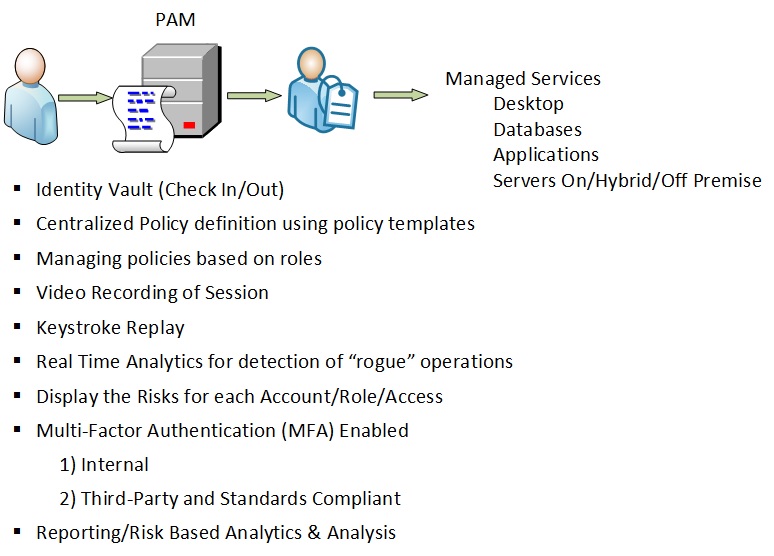
Privileged Access Management Pam Best Practices

Privileged Access Management Pam Solutions Ekran System

Privilege Account Management Solidfish
Privileged Account Management 101 How Can Privileged Accounts Compromise Your Security

One Identity Manager Privileged Account Governance 3 Safeguard User Management Youtube
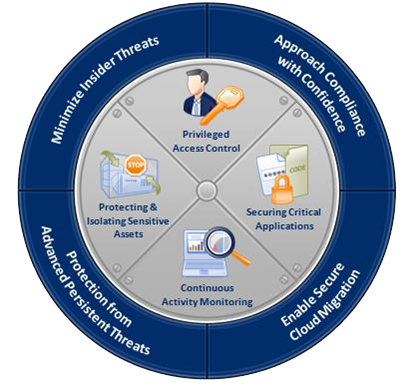
Privilege Access Management
The Seven Keys To A Successful Privileged Account Management Strategy Kuppingercole

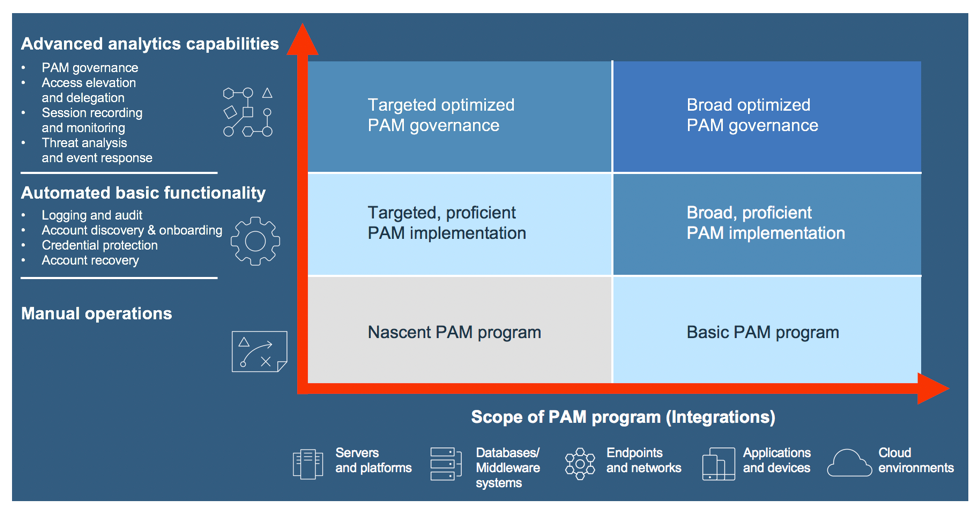
Tech Talk Privileged Account Management Maturity Model

Ciso Series Secure Your Privileged Administrative Accounts With A Phased Roadmap Microsoft Security

Privileged Access Management For Active Directory Domain Services Microsoft Docs

Secure Sensitive Data With Robust Privilege Account Lifecycle Management Arcon Blog

Discover Privileged Accounts On Your Network Micro Focus Community

What Is Privileged Access Management Security Priority 1
Protect Your Matrix With Strong Privileged Access Management

Top 5 Poor Privileged Account Management Practices Ekran System
7 Essential Features Of A Perfect Privileged Access Management Solution

Latest Stories Published On Best Privileged Account Management Articles Medium

What Is Privileged Access Management Pam Read The Definition In Our Security Glossary Beyondtrust
Cyberark Privileged Account Management Wwt

Privileged Account Management Pam Identity Management Institute
Q Tbn And9gcra3bbhof R0q9celbr14idqicmddrf9hwgenqk1a Bl D9qcom Usqp Cau
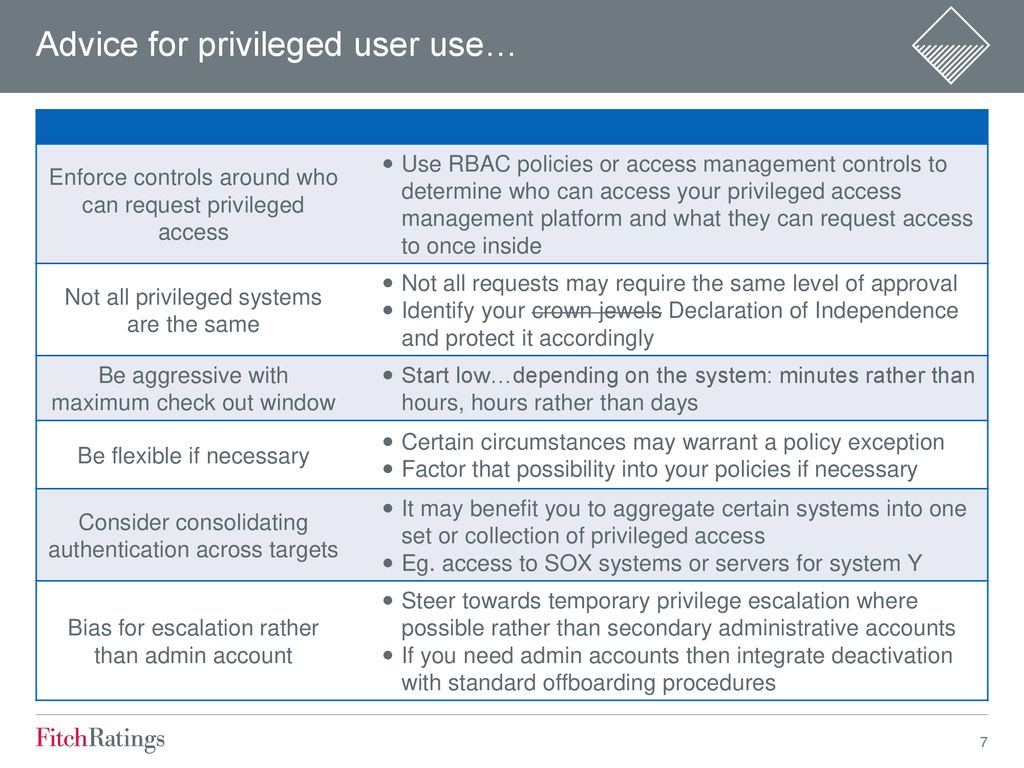
Privileged Access Management Ppt Download
Privileged Identity And Credential Management Beyondtrust

How Privileged Account Manager Solves The Business Challenges Privileged Account Manager Administration Guide

Pam Market Size Worldwide Statista
B2bsalescafe Files Wordpress Com 17 11 Market Guide For Privileged Access Management Aug 17 Pdf

Microsoft Azure S Privileged Identity Management Dev Community

Breaches Are Inevitable Adding Resiliency To Your Pam Program Technology Insights Blog

Privileged Account Management 1 In Gartner Top 10 Security Projects

Privileged Access Management In Office 365 Is Now Generally Available Microsoft Tech Community

Reports Dashboards And Analytics Bravura Privilege

What Is Privileged Account Management Manageengine Password Manager Pro

Managing The Keys To The Kingdom Privileged Shared Accounts Simeio Solutions Oracle Cloud Security Blog

A Seven Step Process To More Effective Privileged Account Management

Tech Talk Privileged Account Management Maturity Model

Privileged Access Management Pam Is The 1 Cyber Security Priority

Privileged Account Management Is Critical For Information Security
Infographics Ten Functions Of Privileged Account Management Xton Technologies
Privileged Account Management Best Practices
It S Time To Rethink Privileged Account Management Security Boulevard

Thycotic Unveils Solution For Rapid Limitless Scalability Of Privileged Account Management Deployments In Secret Server 8 9
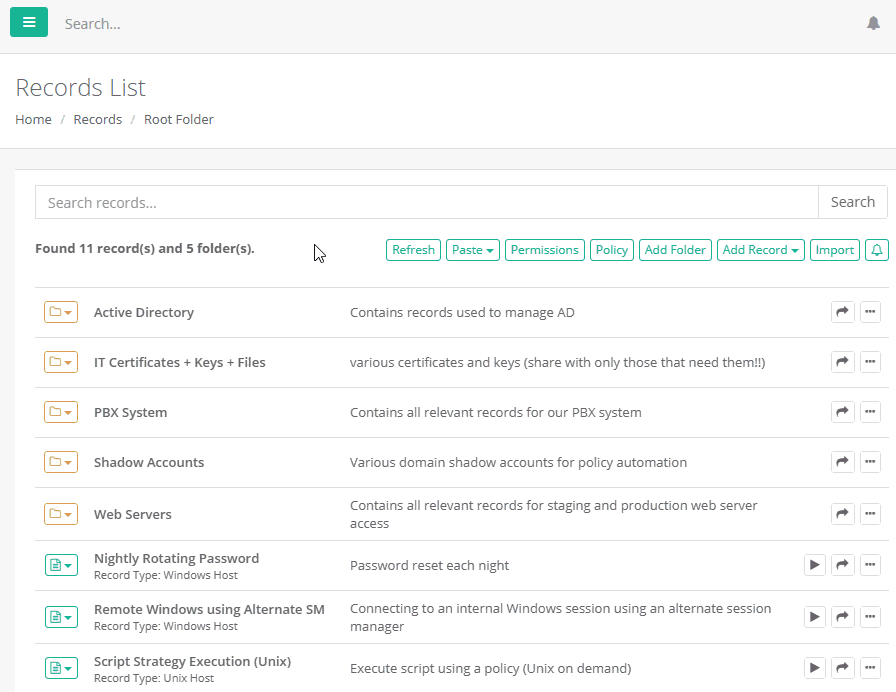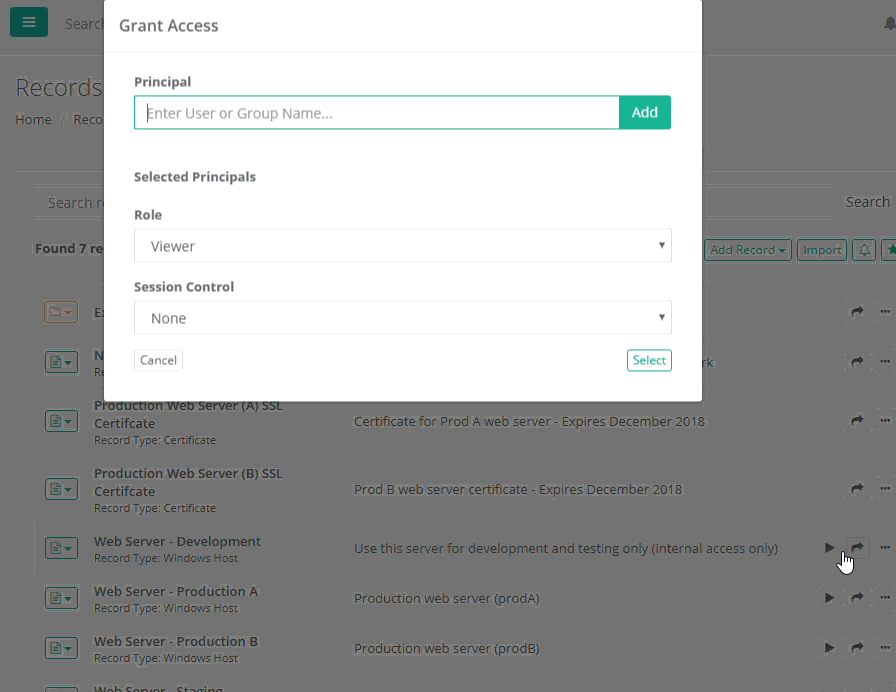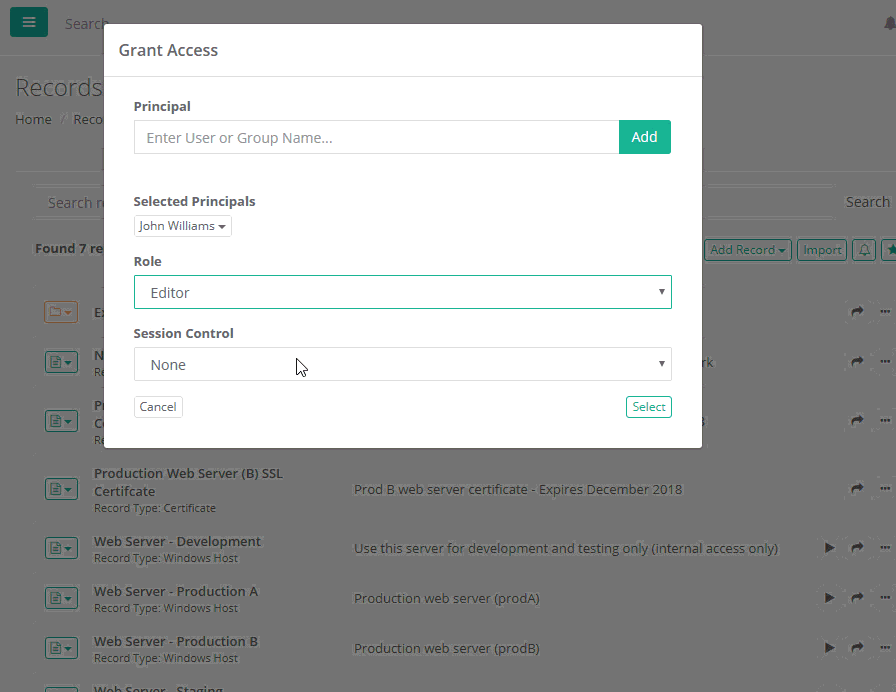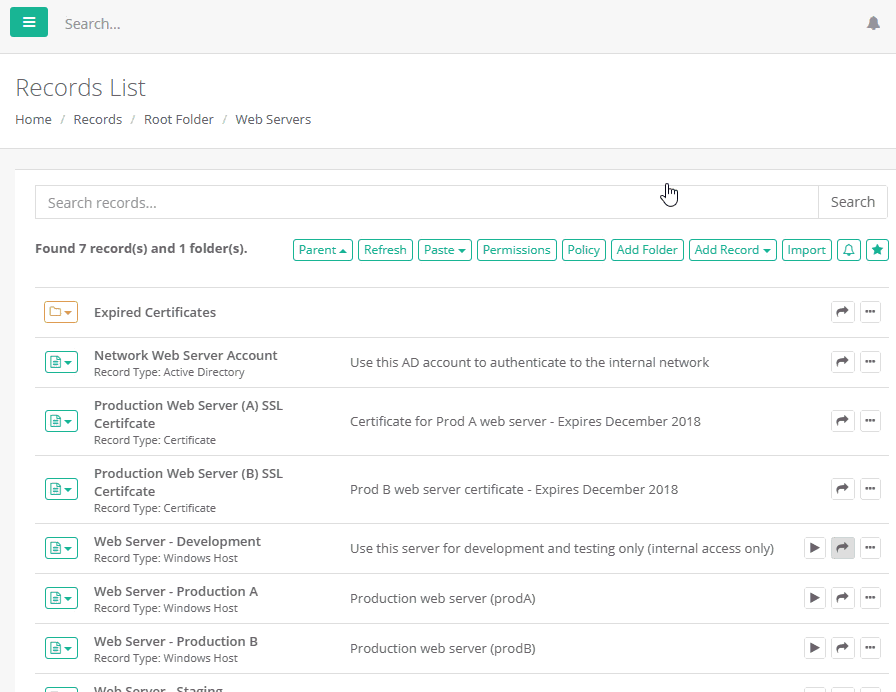
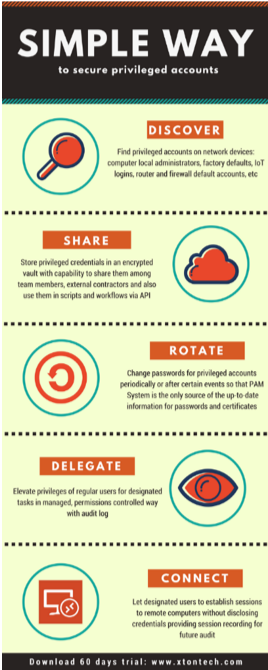
Privileged Account Management Xton Technologies

What Is Privileged Access Management Security Priority 1

Privileged Account Management For Dummies Bankinfosecurity
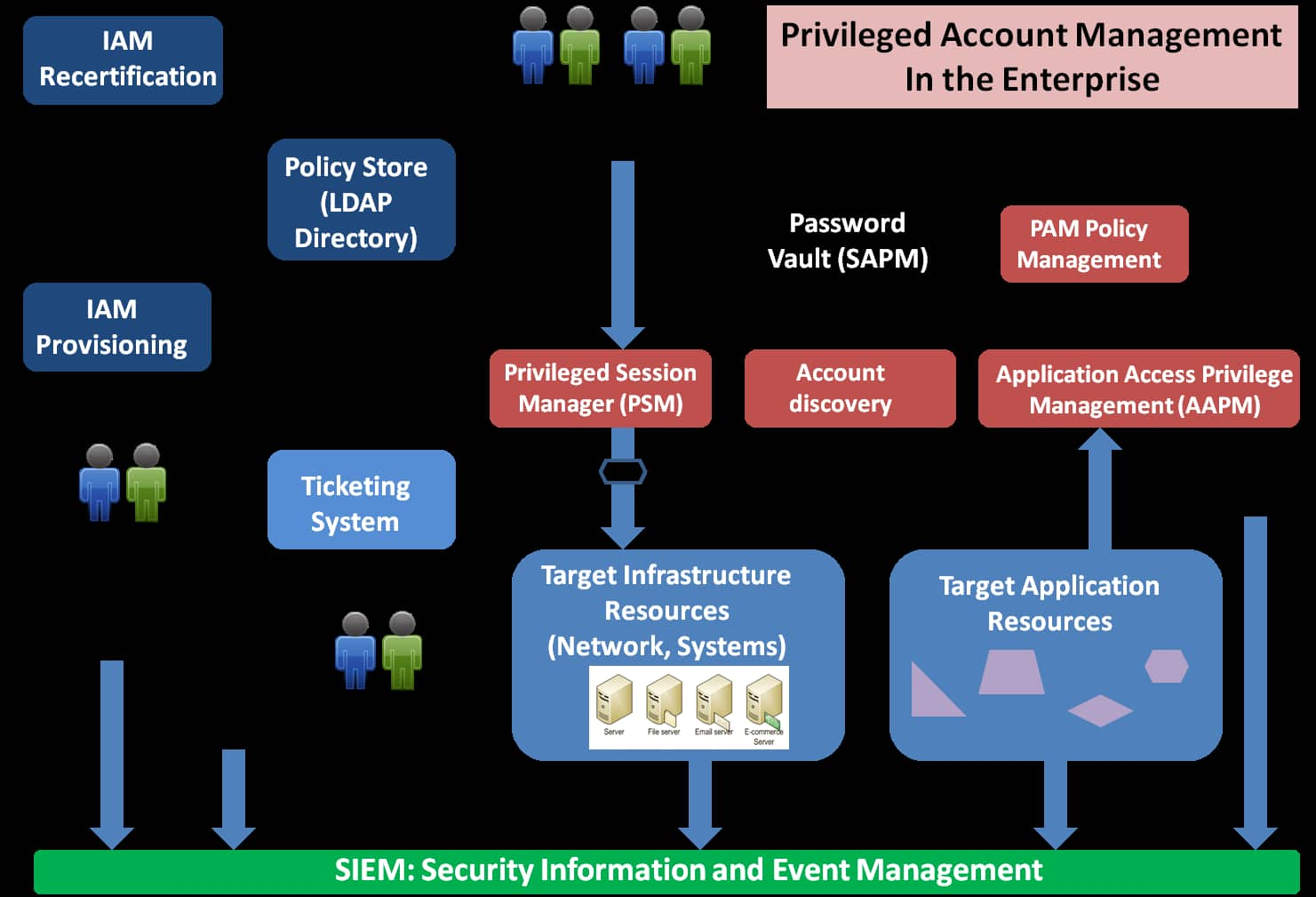
The Components Of Privileged Account Management Process Download Scientific Diagram
Privileged Access Management For Windows Active Directory Domains

Different Paths Same Goal Privileged Account And Session Management Pasm And Privilege Elevation And Delegation Management Pedm

Secret Vault Privileged Account Management Platin Bilisim

Privileged Account Management 101 How Can Privileged Accounts Compromise Your Security
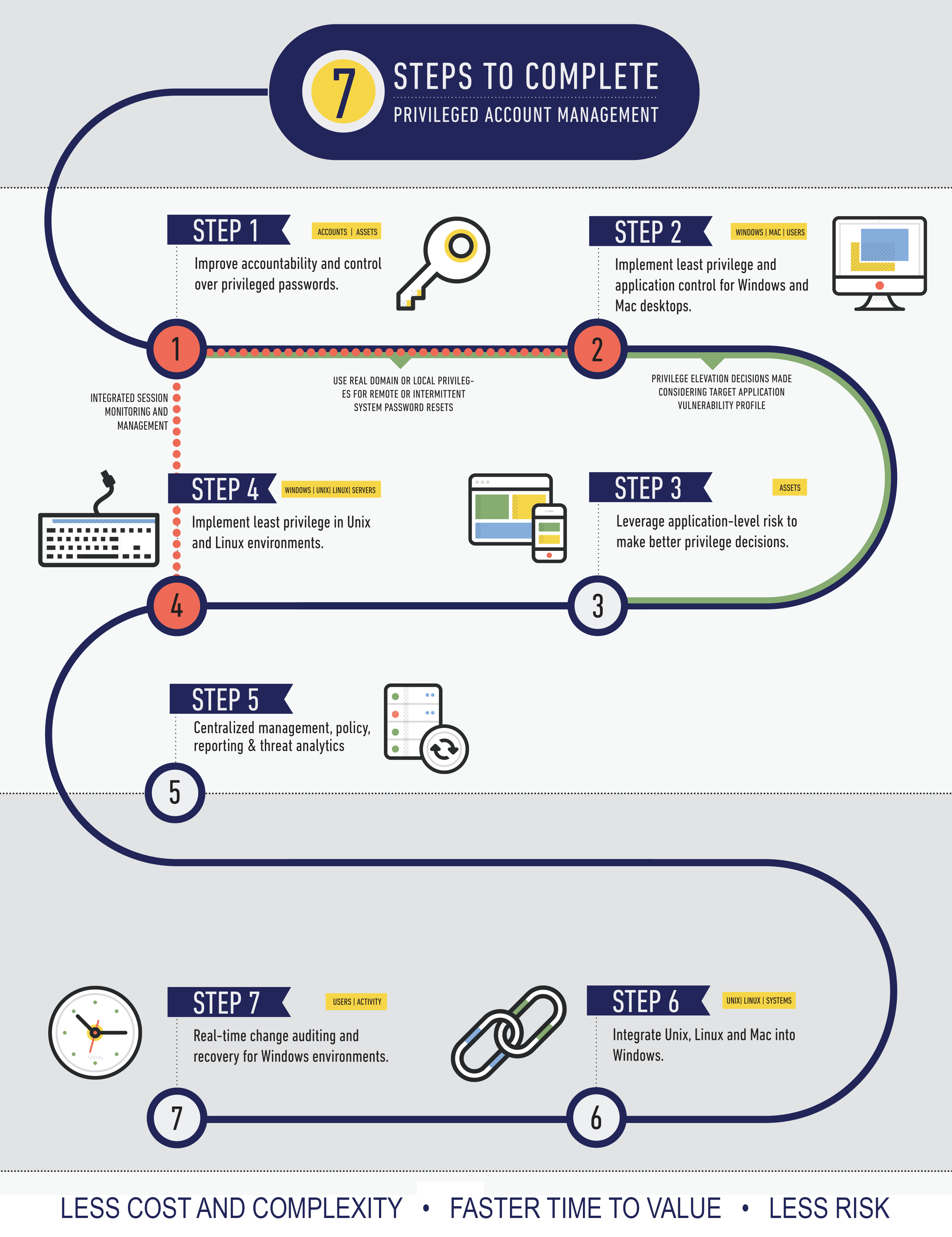
Where To Begin A 7 Step Strategy To Achieving Complete Privileged Account Manag Beyondtrust

Application Model For Privileged Account Access Control System In Enterprise Networks Sciencedirect

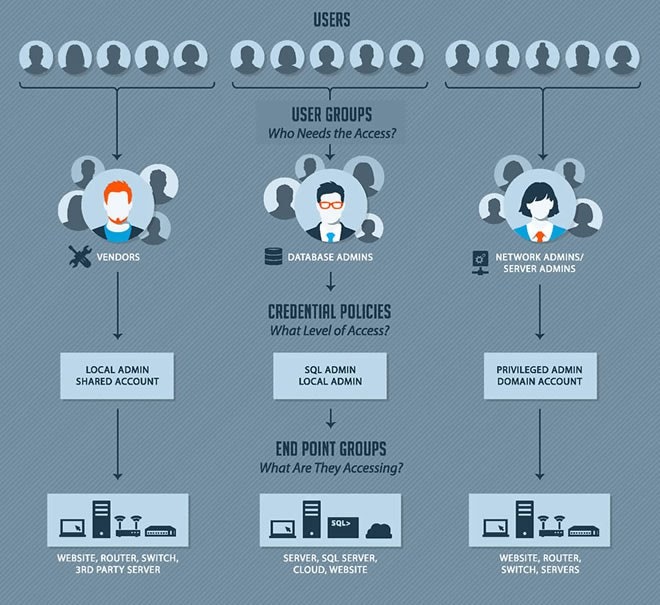
7 Most Common Privileged User Management Systems The Techeries

19 Zero Trust Privilege Maturity Model Episode 1
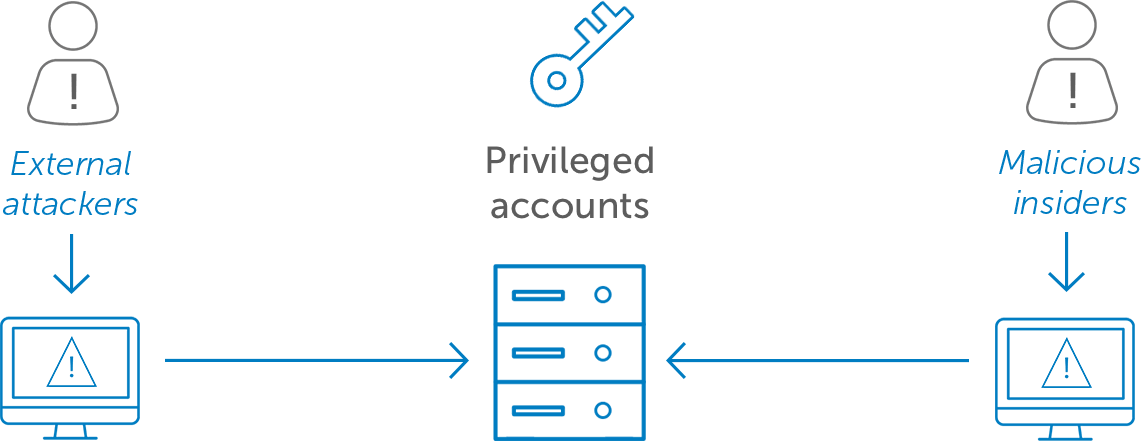
Privileged Access Management Okta

What Is Privileged Account Management Manageengine Password Manager Pro
1

Shows How Privileged Access Management Pam Helps To Address Five Download Scientific Diagram

Cst Thycotic Privileged Account Management For Dummies
Q Tbn And9gctpjnb9hbyz6uq354eupuksflw5vrl 4yn Xu6gaae Usqp Cau
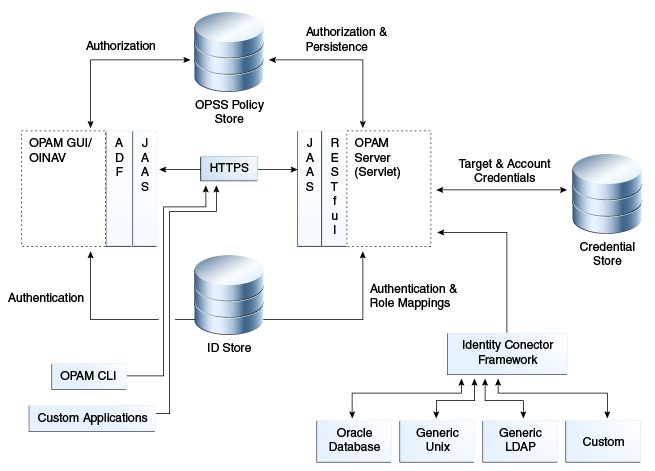
Understanding Oracle Privileged Account Manager

What Is Privileged Account Management Pam

How Privileged Account Manager Solves The Business Challenges Privileged Account Manager Administration Guide

Pam Deployment Is Challenging And Requires Well Managed Projects

What Is Privileged Access Management Pam Varonis

Learn About Privileged Access Management Microsoft 365 Compliance Microsoft Docs

Privileged Account Security Solutions With Cyberark
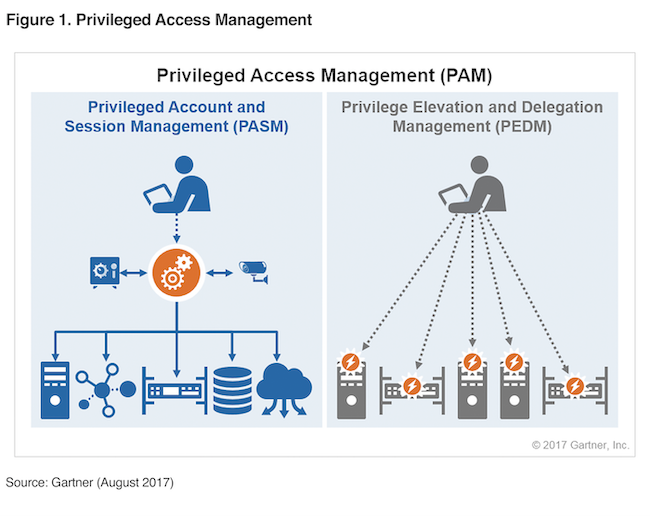
Privileged Account Management A Mandatory Requirement A Dnext
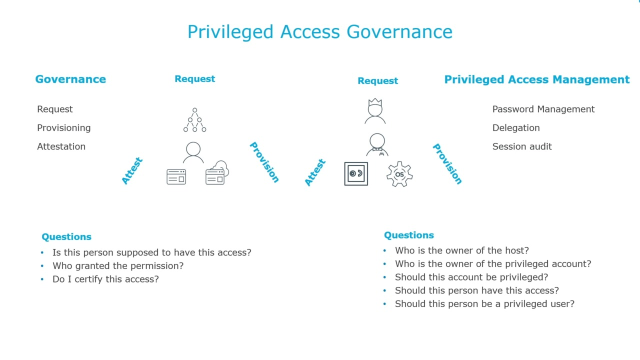
Privileged Access Governance

What Is Privileged Access Management Pam Varonis

Privileged Account Management With Cyberark Don T Panic
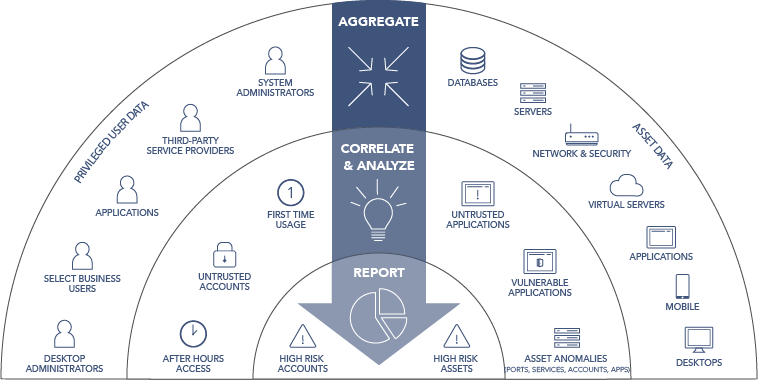
What Is Privileged Access Management Pam Read The Definition In Our Security Glossary Beyondtrust

Privileged Access Threat Report 19 Beyondtrust
Q Tbn And9gcrnc1smthjizbbj9kds2igecehsrafcgcyawyjytan2vuxatk Usqp Cau

Privileged Access Management Pam Zero Trust Privilege Service Centrify

3 Strategic Decisions That Power Your Privileged Account Access Approach Cybersheath

Why Privileged Access Management Pam Should Be Cisos Top Priority

Privileged Account Management Best Practices
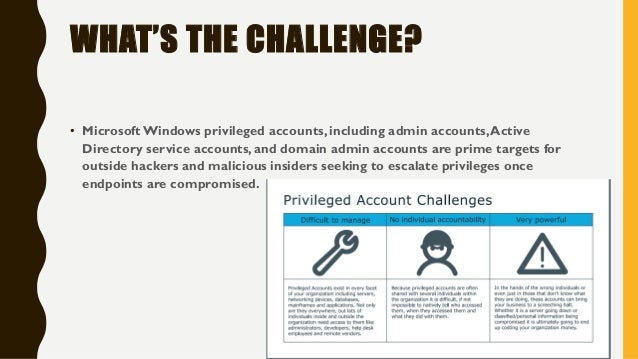
10 Steps To Better Windows Privileged Access Management
Www Nccoe Nist Gov Sites Default Files Library Project Descriptions Fs Pam Project Description Draft Pdf

What Is Privileged Access Management Onelogin

What Is Privileged Account Management Manageengine Password Manager Pro
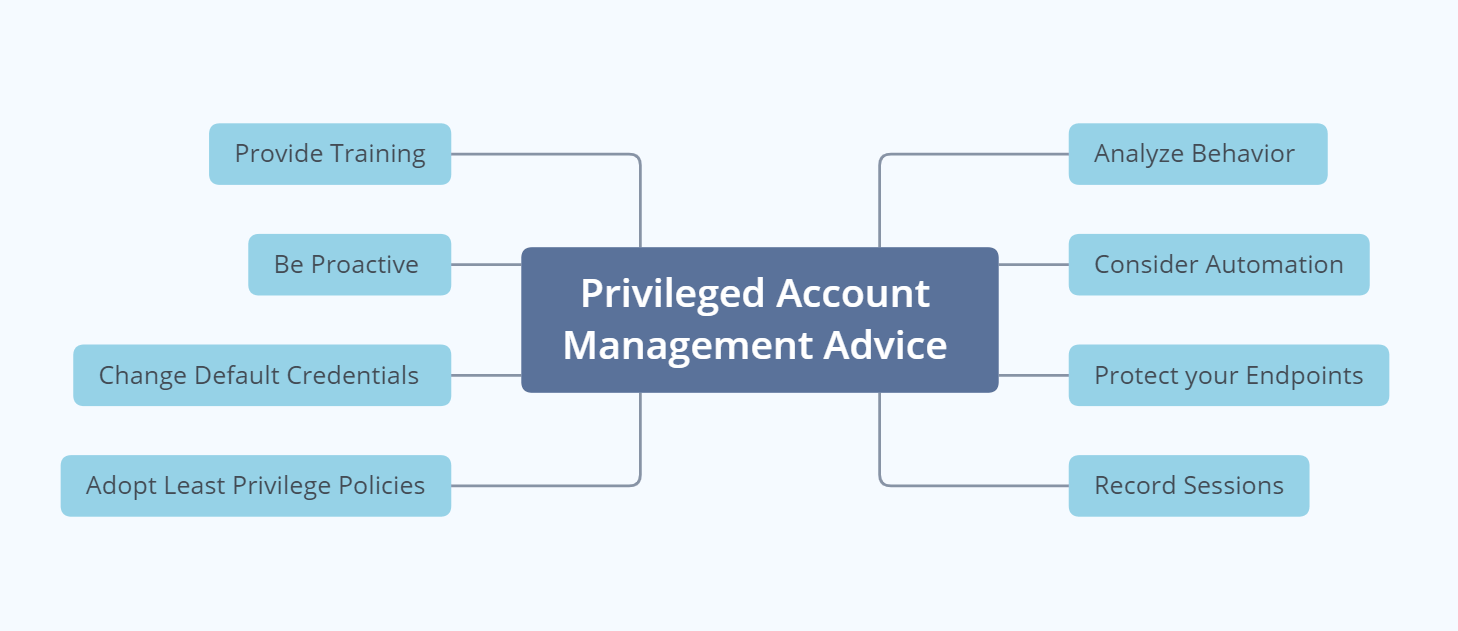
Privileged Account Management 101 How Can Privileged Accounts Compromise Your Security
Http Wearearmadillo Com Wp Content Uploads 17 11 Cyberark Privileged Account Security Pdf

Privileged Access Management Netiq Privileged Account Manager Micro Focus

Privileged Access Management For Active Directory Domain Services Microsoft Docs

Capability Framework For Privileged Access Management

What Is Privileged Access Management Pam Varonis

Why Privileged Access Management Is Essential For All Businesses Patecco En
Docs Broadcom Com Docs Kuppingercole Leadership Compass Privileged Access Management

What Is Privileged Account Management Pam
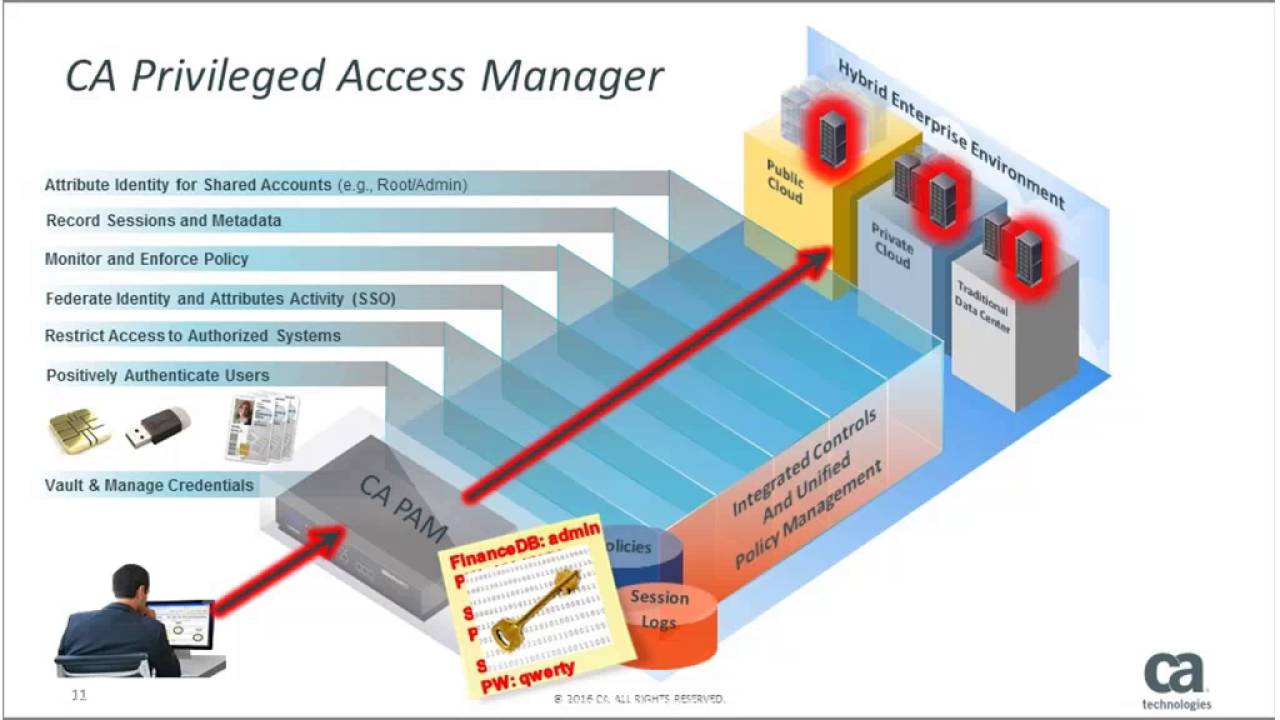
What Is Ca Privileged Access Manager Definition From Whatis Com



